
Preface:
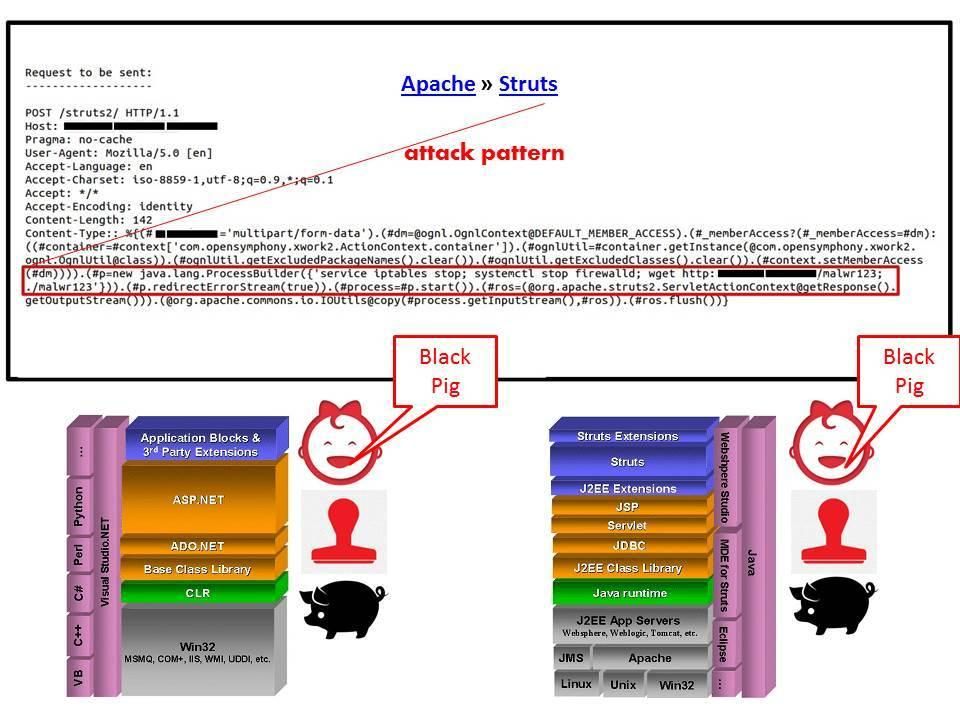
We heard shocking news this year especially EQUIFAX breach. The hackers accessed up to 143 million customer account details earlier this year. Thereafter a data breach happened on July 29 and the details taken include names, social security numbers, drivers licences, and credit card numbers of around 200,000 people. Perhaps you could said that the incident given by vulnerability on Apache component Struts CVE-2017-5638. A design limitation was found in the Jakarta Multipart parser. A proof of concept shown that we can set the Content-Type to an OGNL expression such as:
Content-Type: ${(#_='multipart/form-data').
The Content-Type is not escaped after the error, and is then used by LocalizedTextUtil.findText function to build the error message. This function will interpret the supplied message, and anything within ${…} will be treated as an Object Graph Navigation Library (OGNL) expression. As a result the attacker can leverage these conditions to execute OGNL expressions that in turn execute system commands (see below diagram for reference).
API security is important today especially the API infiltration
So far includes myself only focusing in ring 0 attack. It looks that information security bring my attention to kernel hooking. Once upon a time, kernel hooking looks like it is everything. I think it might have similarity and such a way anti-virus manufacturer address in the same place. But when do we awake? I believed that it is the Java application century. API security level equivalent to kernel level.
Actually the defense mechanism not difficult to detect the malware on 32-bit operating system. For instance, on a 32-bit windows system, antivirus software may use SSDT hooking (System Service Dispatch Table hooking). Using SSDT hooking, the Antivirus software can prevent attacks based on the APIs being called by the malicious software.
So, it looks secure that once modern antivirus installed, right?
But what is the reason let cyber attack victims growth rapidly? Even though IDS , firewall and modern antivirus software was deployed?
Closer Look details
Windows 7 x64 is shipped with Patch Guard which doesn’t allow to hook SSDT/MSRa/code section. Disabling PatchGuard is the 1st priority of objective for malware. Since we are the system owner and therefore it is easy to disable the Patch Guard function in your 64 bit window operating system by yourself. The instruction displayed below:
Type msconfig, Go to the boot tab and delete the patched boots.
Or running the following commands in a root-shell and restarting the PC afterwards.
Bcdedit /debug ON
Bcdedit /dbgsettings SERIAL DEBUGPORT:1 BAUDRATE:115200 /start AUTOENABLE /noumex
As we know, malware couldn’t conduct manual driven job task. If malware is going to find their target named function. It must go to the correct memory address (refer to table 1). But the objective of the PatchGuard is protect the following data and structures.
• Modifying system service tables, for example, by hooking KeServiceDescriptorTable
• Modifying the interrupt descriptor table (IDT)
• Modifying the global descriptor table (GDT)
• Using kernel stacks that are not allocated by the kernel
• Patching any part of the kernel (detected only on AMD64-based systems)
Remark: The inline hooking 3 step slogan. However it doesn’t work since patch guard is enable.
- The Hook – A 5 byte relative jump which is written to the target function in order to hook it, the jump will jump from the hooked function to our code.
- The Proxy – This is our specified function (or code) which the hook placed on the target function will jump to.
- The Trampoline – Used to bypass the hook so we can call a hooked function normally.
How malware trim down himself, then go to kernel level. How to bypass antivirus or malware detector?
Attempt 1. Find out design limitation on web portal then using the scripting API or dynamic JSP inject command. One of the example has shown from our discussion first page. Try to find out vulnerability on web server side module or component. Or find our the weakness of programming design (see below for reference) then inject system command.

But is there additional way to conduct API infiltration?
Attempt 2. Hooking Shared Library Function Calls
Phenomenon: Apache web server deployment high coverage in the world. However not less Apache servers are running on Windows operating system.
Variables factor: enable patchguard and ASLR (those functions might be make hack activities more difficulties)
Below diagram is the reference of example how does inline hook jumping to malicious code and then executing the original function.

Since defense function was strengthen today. Antivirus embedded malware detection function, Microsoft PatchGuard verify the instruction and ASLR conduct random address function limit malware infection and therefore below traditional way of cyber attack can not work well!
- DLLs loaded at runtime into process address space
For kernel32 – target private addres space between 0x00010000 and 0x7FFE0000 - Hiding files in a directory
Replace FindFirstFile(),FindNextFile() in Kernel32 to skip rootkit files
Is there any benefits in below attack methods?
DirectX/OpenGL APIs and time functions – Typically hooked to implement cheating in on-line games.
Status: Possibility high, under our observation.
Winsock API – Hooked to monitor network traffic.
Status: It was happened in frequent. Under observation now.
But a security gap still valid because of today fast growth business strategy
Further to my study on cyber attack incident over past few months, a hints to me that API hook technique on layer 7 (application layer) is the key milestone of hacker today. See below cyber incident records for reference:
February 2017 – The internet infrastructure company Cloudflare announced that a bug in its platform caused random leakage of potentially sensitive customer data.
Incident root cause analysis: Search engines like Google and Bing that crawl the web, though, automatically cached the errant data—everything from gibberish to users’ Uber account passwords and even some of Cloudflare’s own internal cryptography keys—making it all easily accessible through search.
June 2017 (It discovered the data breach June 19): 198 Million Voter Records Exposed
Incident root cause analysis: Misconfiguration isn’t a malicious hack in itself. However such incident shown to the world that a wide range of component could be impact the information security world. A misleading message bring people major focus on operatio system level from past.
July 2017 (It discovered the hack on July 29) : Equifax recently had 143 million customer records breached in a hack.
Incident root cause analysis: Found security weakness on patch management in IT operation and vulnerability awareness. The incident given by vulnerability on Apache component Struts CVE-2017-5638.
A major unknown area will be transformed to hacker new target
Technology zone: The IP telephony technology integrated with TCP stack more than decade. However business operation keen to enhance the functional features. And therefore do the customization for system integration is hard to avoid. We seen some network communications hardware vendor will be involved in the application interface technologies. Modern business world more tough and demanding competition. Looks Cisco also become the victim on former vulnerability hiccups. For more details, please see below url for reference.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170909-struts2-rce
Summary: Seems, I did not has final checkpoint guide me to drawn any conclusion on this discussion. Hey Guy, keep your eye open. There will be more strange things happened in today such demanding and tough business world!
Be a happy Sunday. I remain with my best regards.

Reference table 1:





DirectX 12 continues to be a brand-new technology – and in a few ways it is still – however in reality we’ve now been discussing the images API for the better part of half of a 10 years. Microsoft first released the then-next technology images API to much fanfare again at GDC 2014, with the original iteration shipping within House windows 10 a calendar year later. For a variety of reasons DirectX 12 adoption continues to be in its start – software dev cycles are long and Operating-system adoption cycles are much longer still – but with their low-level images API firmly set up, Microsoft’s DirectX groups already are hard at the job on another generation of design technology.