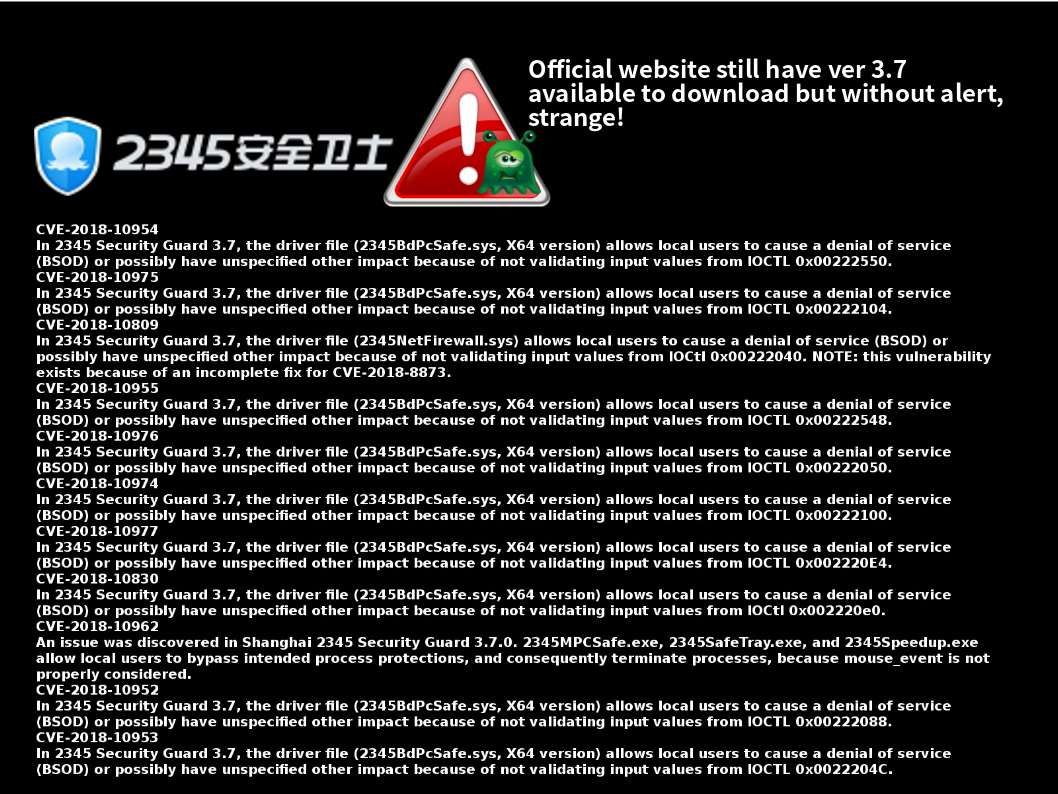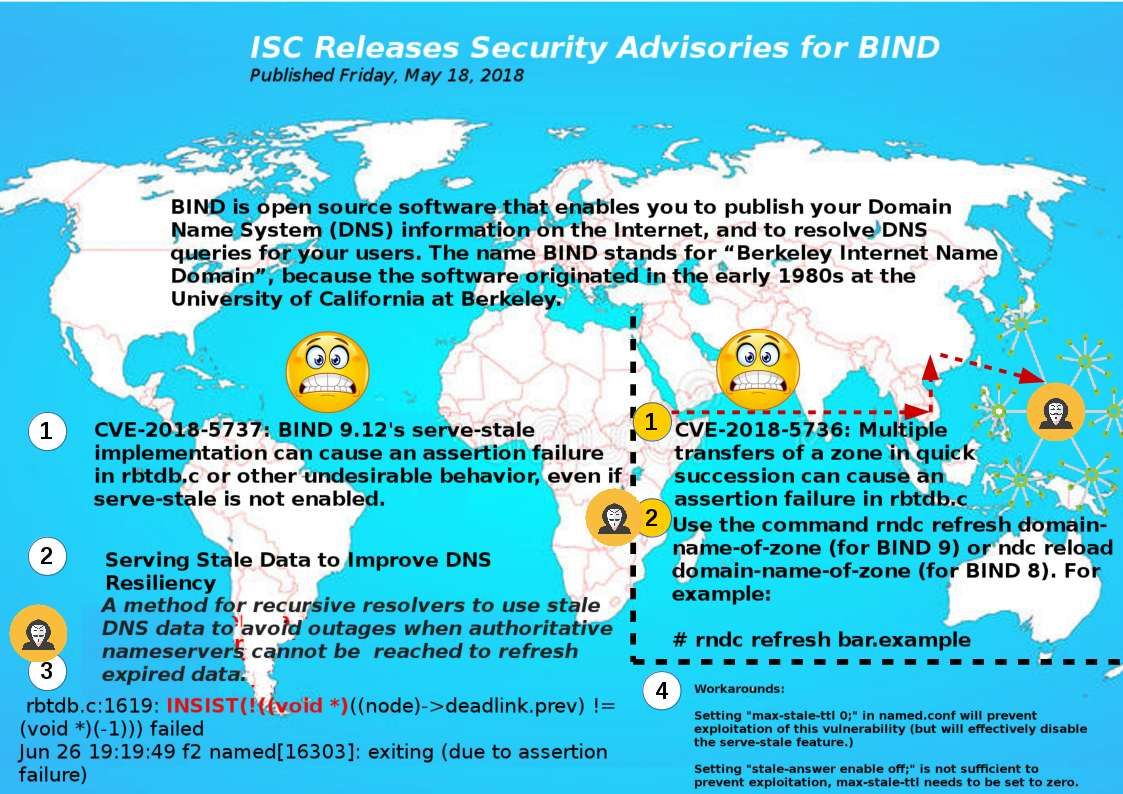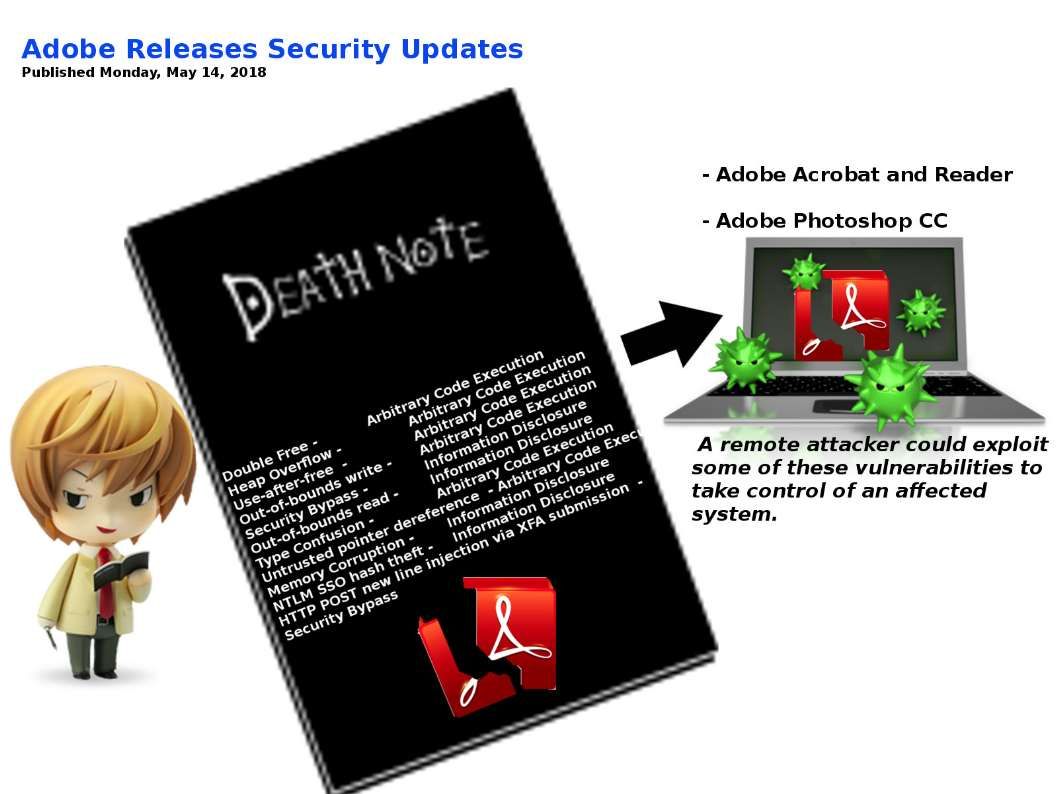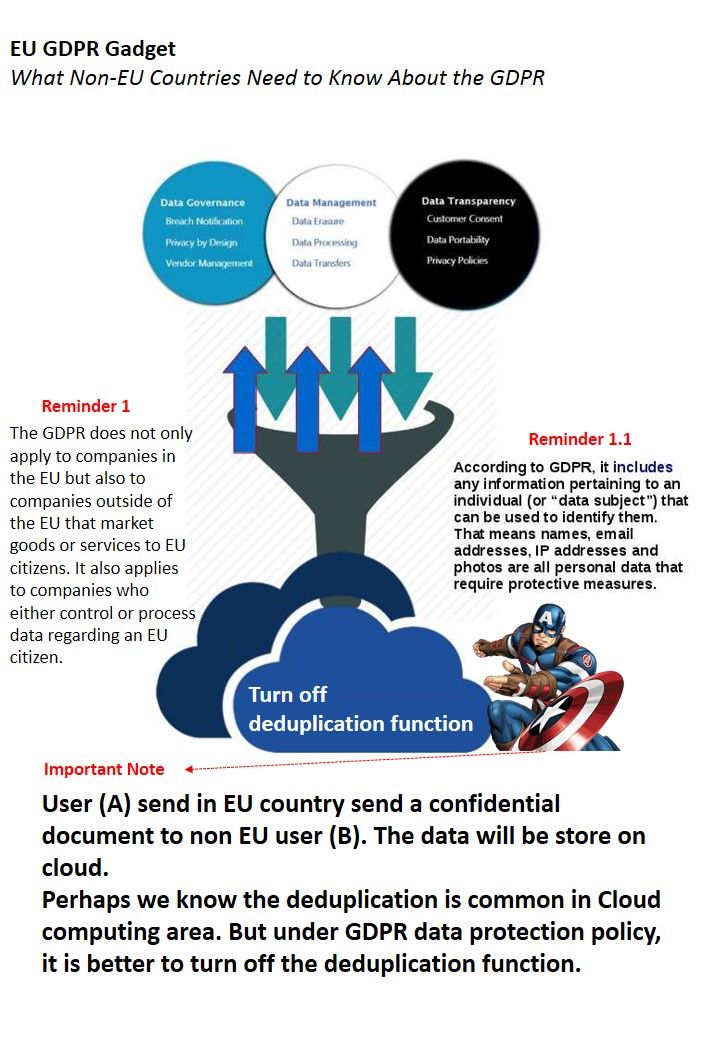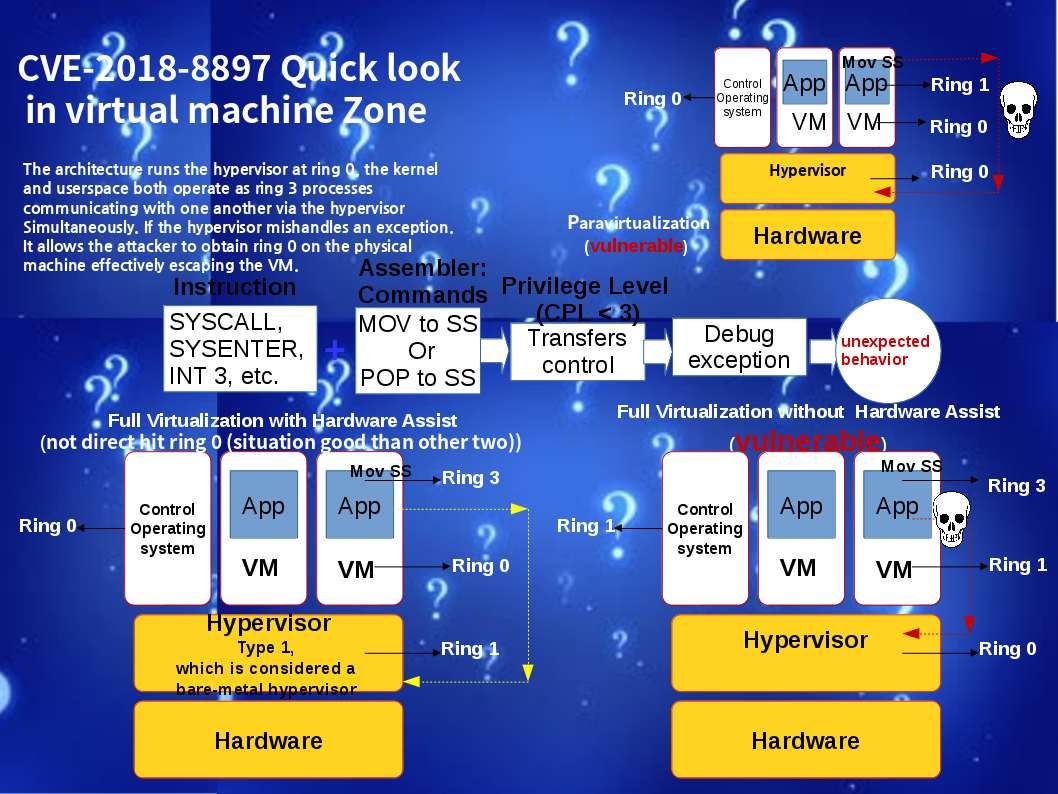
Technology world is a challengeing zone. The key word “rest” looks do not apply to system developer, application programmer and IT expert! I re-call the vulnerability (CVE-2018-8897) to review. It ennounced by security experts for week ago. Perhaps you have full understanding. However no harm in my view point to do the review since it is important. I have time to drill down the detail and visualize my standpoint. This CVE subject mainly focus mishandling of assembler command syntax by system developer since they overlook some advice by CPU vendor. In short the issue is that if the instruction following the MOV to SS or POP to SS instruction is an instruction like SYSCALL, SYSENTER, INT 3, etc. that transfers control to the operating system at CPL < 3, the debug exception is delivered after the transfer to CPL < 3 is complete. OS kernels may not expect this order of events and may therefore experience unexpected behavior when it occurs. So the focus will be go to virtual machine world. Yes, we are a cloud computing world in the moment. For more details, please refer below url for reference.