Microsoft formalized Patch Tuesday in October 2003 till today. It was focus on workstation, server and software product till today. Any differences in the Microsoft architecture model in last decade? Perhaps your answer is the cloud platform and collaboration cloud. Yes, the cloud computing technology similar 14th and 17th centuries renaissance. Thus, a major component in existing technology world.
The point of view of IT management avoid of cloud computing in the earlier stage till today they are enjoy of this technology. As times go by, Microsoft SharePoint product widely deploys in IT environment. There is system architect build SharePoint work as data warehouse.
SharePoint design looks fine from Microsoft point of view. Furthermore both authentication and security are coexist with Active directory. It is a popular setup since it is a single sign on.
The vulnerabilities found on SharePoint in 2018 in retrospect (see below), it display that SharePoint are easy to cause remote code execution by attacker.
| CVE | Score | Vulnerability Type(s) | |
| CVE-2018-8254 | An elevation of privilege vulnerability exists when Microsoft SharePoint Server does not properly sanitize a specially crafted web request to an affected SharePoint server. An authenticated attacker could exploit the vulnerability by sending a specially crafted request to an affected SharePoint server.
The attacker who successfully exploited the vulnerability could then perform cross-site scripting attacks on affected systems and run script in the security context of the current user. These attacks could allow the attacker to read content that the attacker is not authorized to read, use the victim’s identity to take actions on the SharePoint site on behalf of the user, such as change permissions and delete content, and inject malicious content in the browser of the user. |
not yet calculated | |
| CVE-2018-8252 | An elevation of privilege vulnerability exists when Microsoft SharePoint Server does not properly sanitize a specially crafted web request to an affected SharePoint server. An authenticated attacker could exploit the vulnerability by sending a specially crafted request to an affected SharePoint server.
The attacker who successfully exploited the vulnerability could then perform cross-site scripting attacks on affected systems and run script in the security context of the current user. These attacks could allow the attacker to read content that the attacker is not authorized to read, use the victim’s identity to take actions on the SharePoint site on behalf of the user, such as change permissions and delete content, and inject malicious content in the browser of the user. |
not yet calculated | |
| CVE-2018-8168 | A remote code execution vulnerability exists in Microsoft Office software when the software fails to properly handle objects in memory, aka “Microsoft Office Remote Code Execution Vulnerability.” This affects Microsoft Word, Word, Microsoft Office, Microsoft SharePoint. This CVE ID is unique from CVE-2018-8157, CVE-2018-8158. | 9.3 | Exec Code Overflow |
| CVE-2018-0922 | Microsoft Office 2010 SP2, 2013 SP1, and 2016, Microsoft Office 2016 Click-to-Run Microsoft Office 2016 for Mac, Microsoft Office Compatibility Pack SP2, Microsoft Office Web Apps 2010 SP2, Microsoft Office Web Apps 2013 SP1, Microsoft Office Word Viewer, Microsoft SharePoint Enterprise Server 2013 SP1, Microsoft SharePoint Enterprise Server 2016, Microsoft Office Compatibility Pack SP2, Microsoft Online Server 2016, Microsoft SharePoint Server 2010 SP2, Microsoft Word 2007 SP3, Microsoft Word 2010 SP2, Word 2013 and Microsoft Word 2016 allow a remote code execution vulnerability due to how objects are handled in memory, aka “Microsoft Office Memory Corruption Vulnerability”. | 9.3 | Exec Code Overflow Mem. Corr. |
| CVE-2018-0797 | Microsoft Office 2010, Microsoft Office 2013, and Microsoft Office 2016 allow a remote code execution vulnerability due to the way RTF content is handled, aka “Microsoft Word Memory Corruption Vulnerability”. | 9.3 | Exec Code Overflow Mem. Corr. |
| CVE-2018-0792 | Microsoft Word 2016 in Microsoft Office 2016 allows a remote code execution vulnerability due to the way objects are handled in memory, aka “Microsoft Word Remote Code Execution Vulnerability”. This CVE is unique from CVE-2018-0794. | 9.3 | Exec Code Overflow |
| CVE-2018-0789 | Microsoft SharePoint Foundation 2010, Microsoft SharePoint Server 2013 and Microsoft SharePoint Server 2016 allow an elevation of privilege vulnerability due to the way web requests are handled, aka “Microsoft SharePoint Elevation of Privilege Vulnerability”. This CVE is unique from CVE-2018-0790. | 9 |
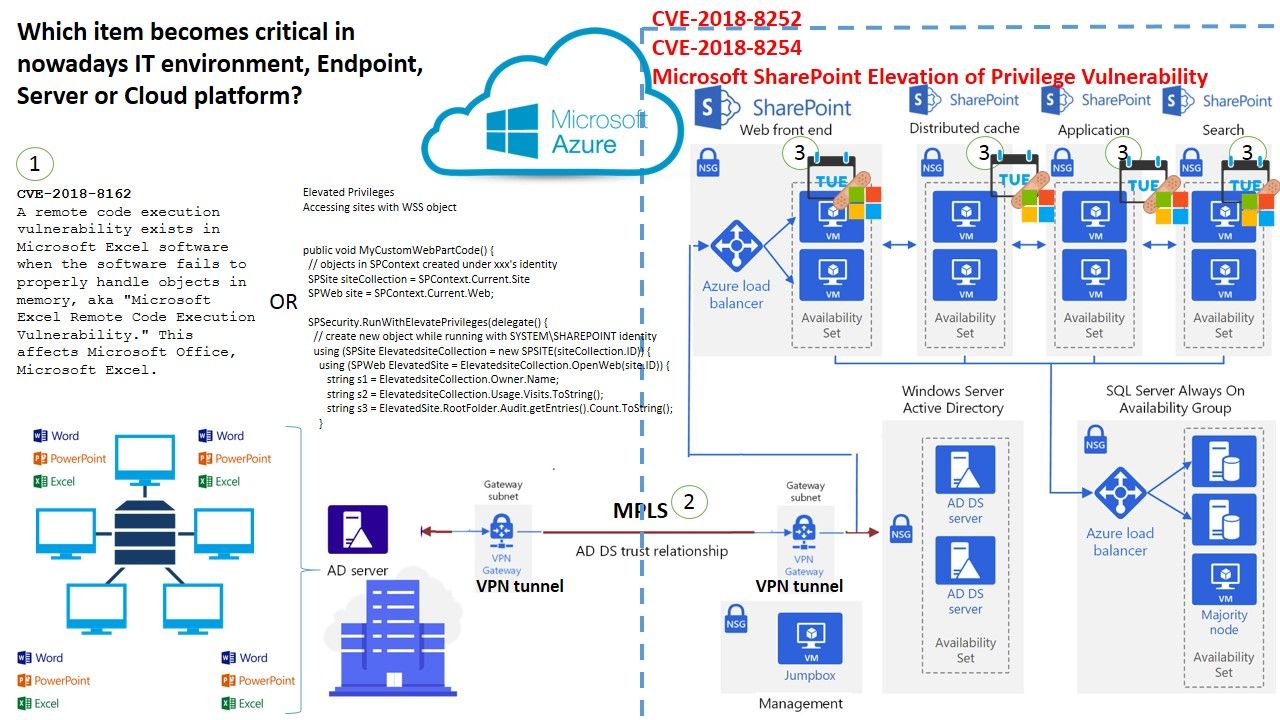
Refer to attach Share Point architecture diagram, this is a common practice model deployment integrate to Azure (IaaS) Cloud platform. If coincidentally MS Excel and Share Point has vulnerabilities occurs (similar situation display on diagram). Which item become critical in nowadays IT environment, end point, server or cloud platform?
See whether below high vulnerabilities items happened on Jun 2018 can provides hints to you in this regard.
CVE-2018-8233 | Win32k Elevation of Privilege Vulnerability – An elevation of privilege vulnerability exists in Windows when the Win32k component fails to properly handle objects in memory, aka “Win32k Elevation of Privilege Vulnerability.” This affects Windows 10, Windows 10 Servers.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8233
CVE-2018-8251 | Media Foundation Memory Corruption Vulnerability – A memory corruption vulnerability exists when Windows Media Foundation improperly handles objects in memory, aka “Media Foundation Memory Corruption Vulnerability.” This affects Windows 7, Windows Server 2012 R2, Windows RT 8.1, Windows Server 2012, Windows 8.1, Windows Server 2016, Windows Server 2008 R2, Windows 10, Windows 10 Servers.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8251
CVE-2018-8252 | Microsoft SharePoint Elevation of Privilege Vulnerability – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8252
CVE-2018-8254 | Microsoft SharePoint Elevation of Privilege Vulnerability – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8254
— End —
