Preface
I can’t hold the tears back!
Rest in peace to victims who were killed in a suspected chemical attack on the rebel-held town of Khan Sheikhoun in north-western Syria on 4 April, 2018.
International Law
About Convention on the Prohibition of the Development, Production, Stockpiling and Use of Chemical Weapons and on their Destruction
Reference :
- Australia Group of countries and the European Commission that helps member nations identify exports which need to be controlled so as not to contribute to the spread of chemical and biological weapons
- 1990 US-Soviet Arms Control Agreement
- General-purpose criterion, a concept in international law that broadly governs international agreements with respect to chemical weapons
- Geneva Protocol, a treaty prohibiting the first use of chemical and biological weapons
Prelude
United state of America is the leader keen to fight against of the evils. As a result their country possibly will be receive high volume of cyber attack after completed the justice military action.
UK a member of the alliance. As a result the situation will be similar.
Forecast target (health care and clinic)
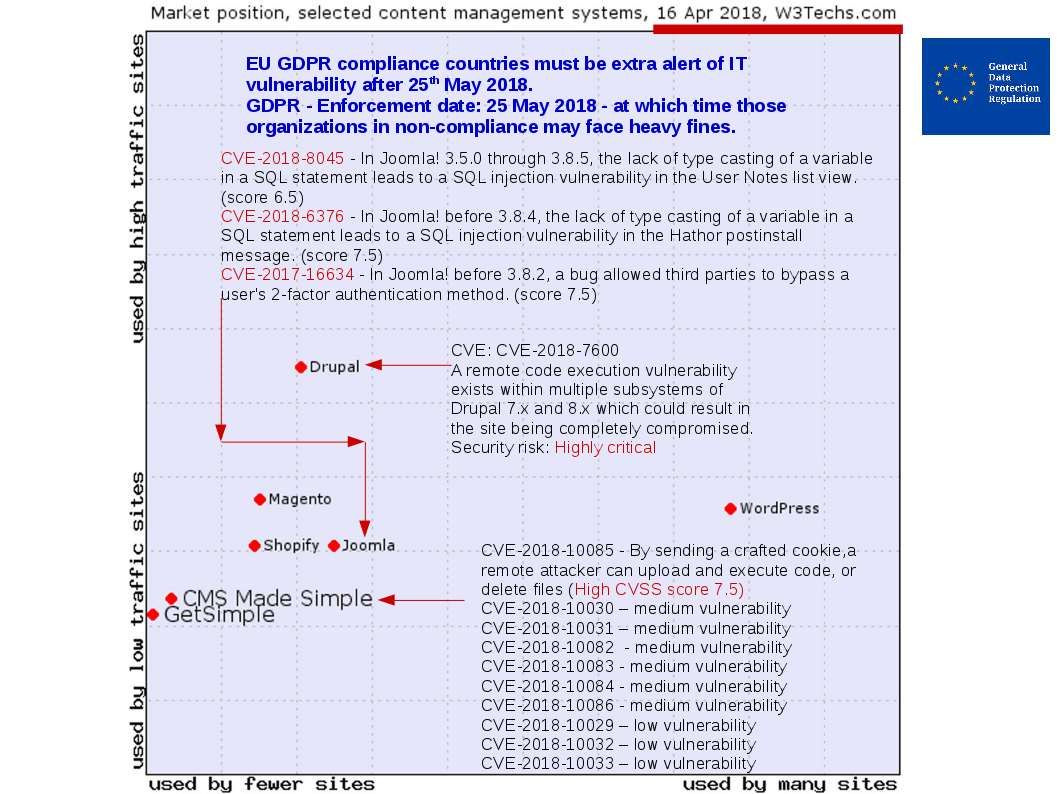
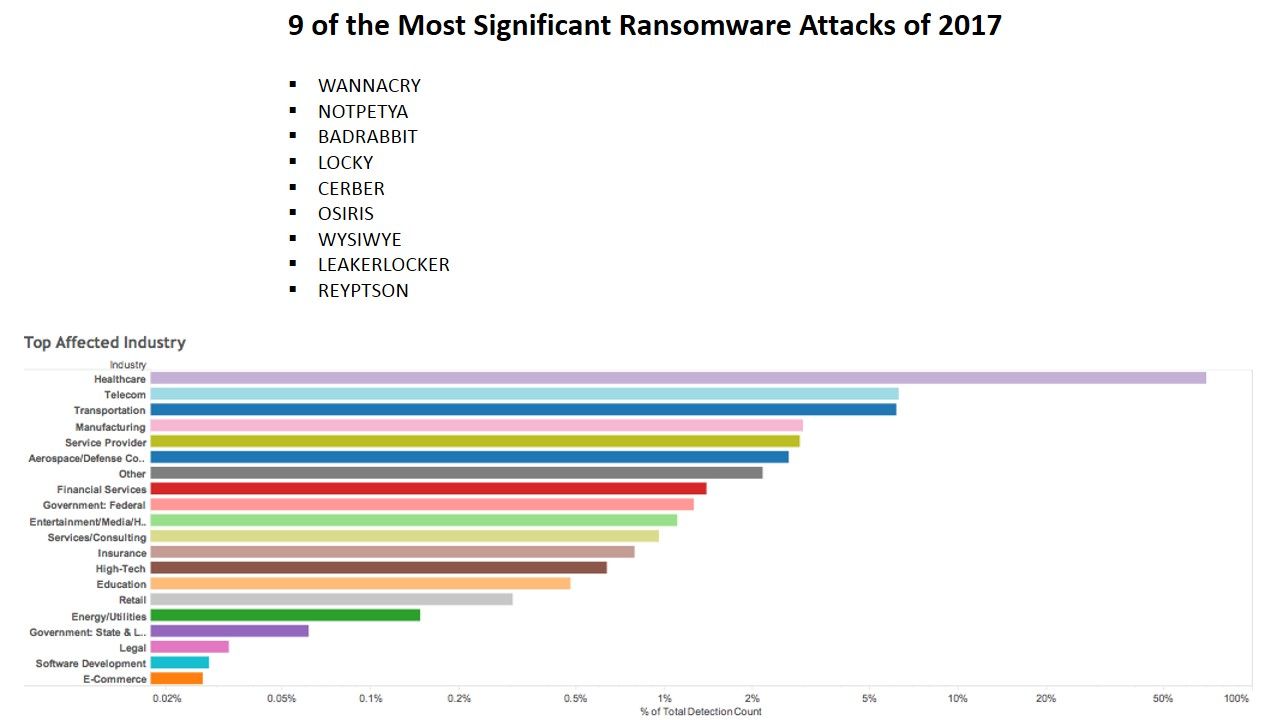
Per observation so far, the wreak havoc ransomware activities in between 2017 to present. Retrospective that the UK healthcare and clinical areas suffered such attack last year. Below table of chart showing the (Ransomware) attack vector to specific industry.
In additional of UK joined the military action. The terrorist will spend the efford to find out the weakness of the healthcare system infrastructure. In logic point of view the healthcare and clinic will become the attack target because the terrorist will buy the details from the criminal group. As a result a complete understanding of the design weakness on those area. Whereby it have high possibilities to engage the 2nd round of attack similar a revenge action.
Earlier last week an article issued by US-CERT with subject. Protecting Your Networks from Ransomware. Their aim is going to provide a guidance to fight against ransomware. Before you read the articles. There are few slogans are able to enhance your data protection framework. For instance:
1. Ransomware and Phishing Work Together
2. For whom who visiting online Gaming zone and Pornography web site in frequent are easy for encounter ransomware attack.
In order to avoid similar of cyber attack, enhance your awareness is the first priority. For more details, please refer below url for reference.
Protecting Your Networks from Ransomware
Predict the target – Pathway (router and network switch)
Since the market share of Cisco in both network switch and router are in big portion (see below diagram)
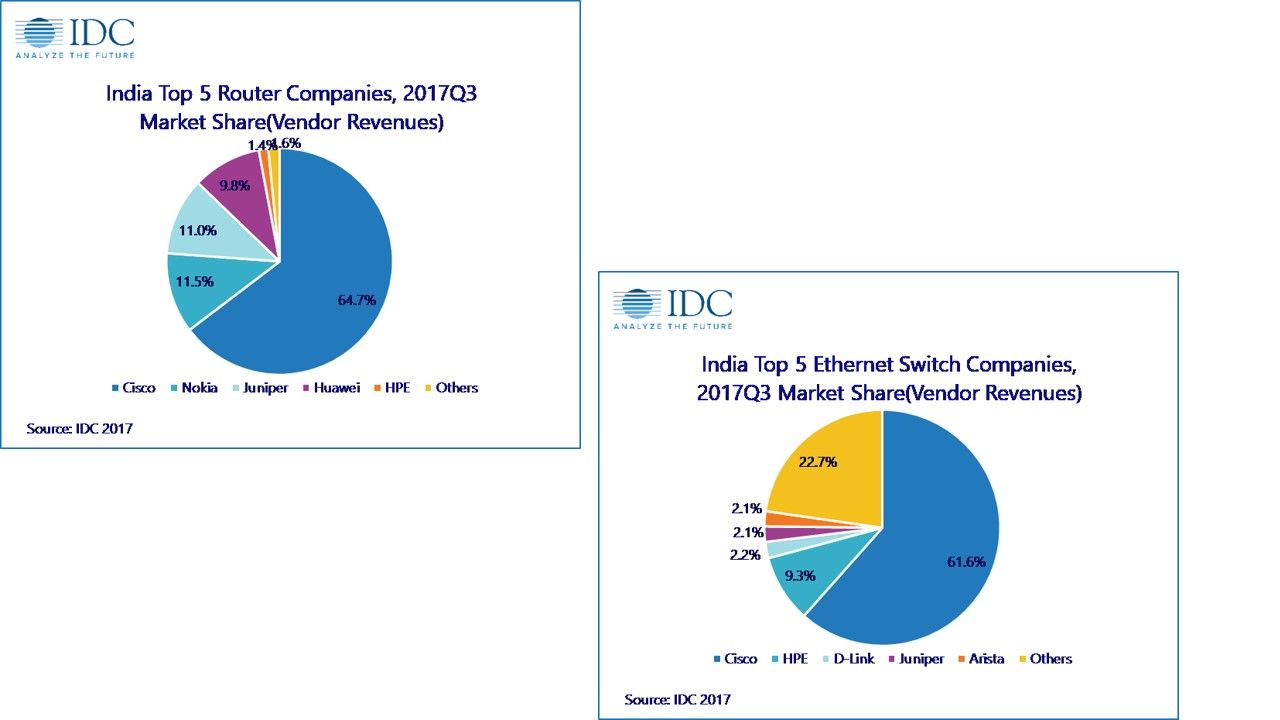
From technical point of view, it is not easy to identify the product design in perfect way in modern technology business market. And therefore the threat actors will be make use of vulnerabilities to engage the cyber attack. In regards to the view point of security expert , hacker now keen to compromise the network switch nowadays. As a matter of fact hacker will prefer to compromise a hardware switch or router because he can control the traffic and retrieve the information. So the Cisco end users must be stay alert of security update announce by Cisco in this period of time. Below informative diagram will provides hints to you in this regards.
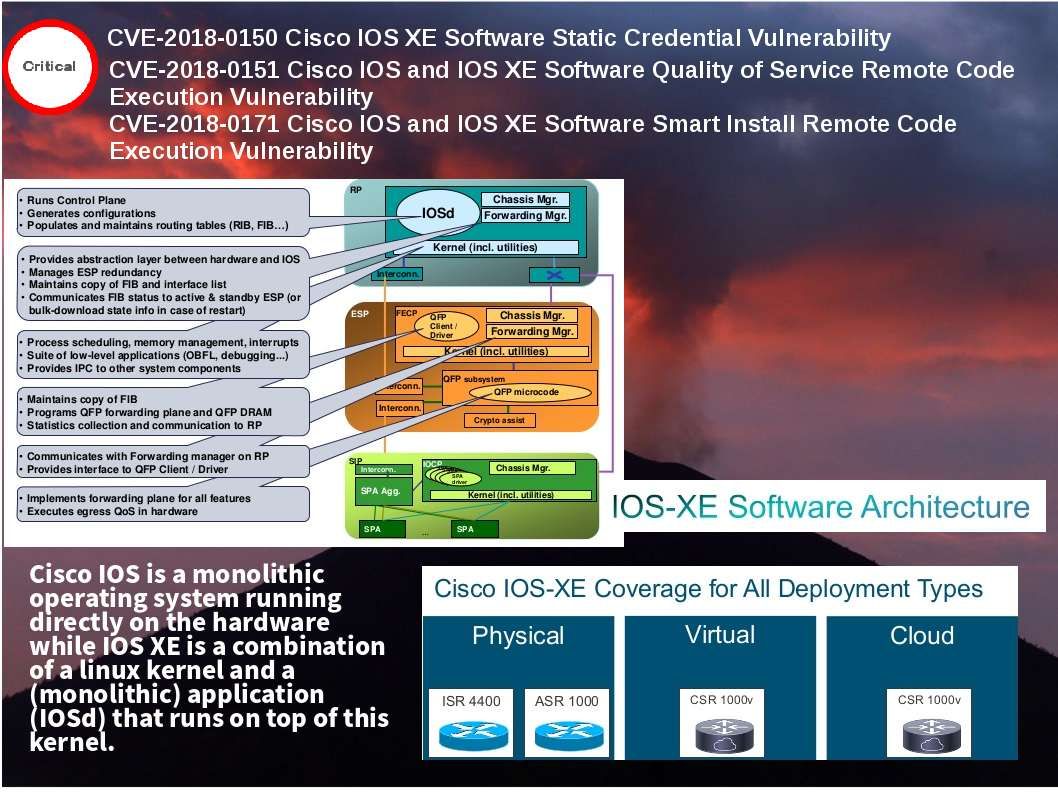
Cisco IOS is a monolithic operating system running directly on the hardware while IOS XE is a combination of a linux kernel and a (monolithic) application (IOSd) that runs on top of this kernel. Attacker executing code remotely using system vulnerabilities. It is common type of attack and hard to avoid.
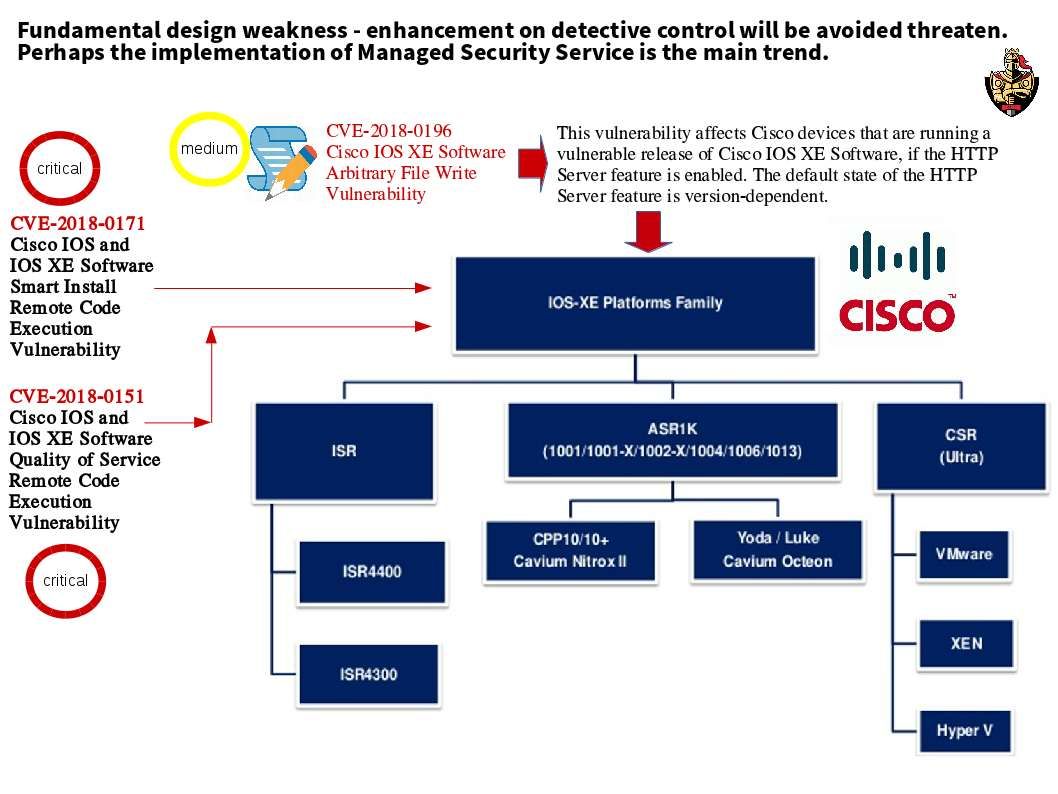
Perhaps a medium vulnerability found on IT product not a shock. However the medium vulnerability co-exists with known critical vulnerabilities created multiple vulnerabilities are unable to foreseen what is the level of damage. Cisco IOS XE fundamental design integrate to open system. The severity of vulnerability CVE-2018-0196 is medium level. End user is allow to disable the http services to avoid the vulnerability. But the default state of the HTTP Server feature is version-dependent. A significant signal alert Cisco customer that corrective control is not enough. The efficient way is enhance your preventive and detective control. That is the implementation of managed security services.

The design objective of the Command Line Parser is used to parse the command line arguments. The parser parsing a string and returns an object representing the values extracted. This is the the regular expression design objective. The Cisco IOS XE is a train of Cisco Systems’ widely deployed Internetworking Operating System (IOS), introduced with the ASR 1000 series. IOS XE is a combination of a linux kernel and a (monolithic) application (IOSd) that runs on top of this kernel. The goal of IOS SE aim to integrate the IOS feature set for routing and switching cope with modern business critical applications. The CLI command injection vulnerability has been found on CISCO IOS XE. Stay alert.
US-cert encourages users and administrators to review the following Cisco Security Advisories and apply the necessary updates. For more details, please see below:

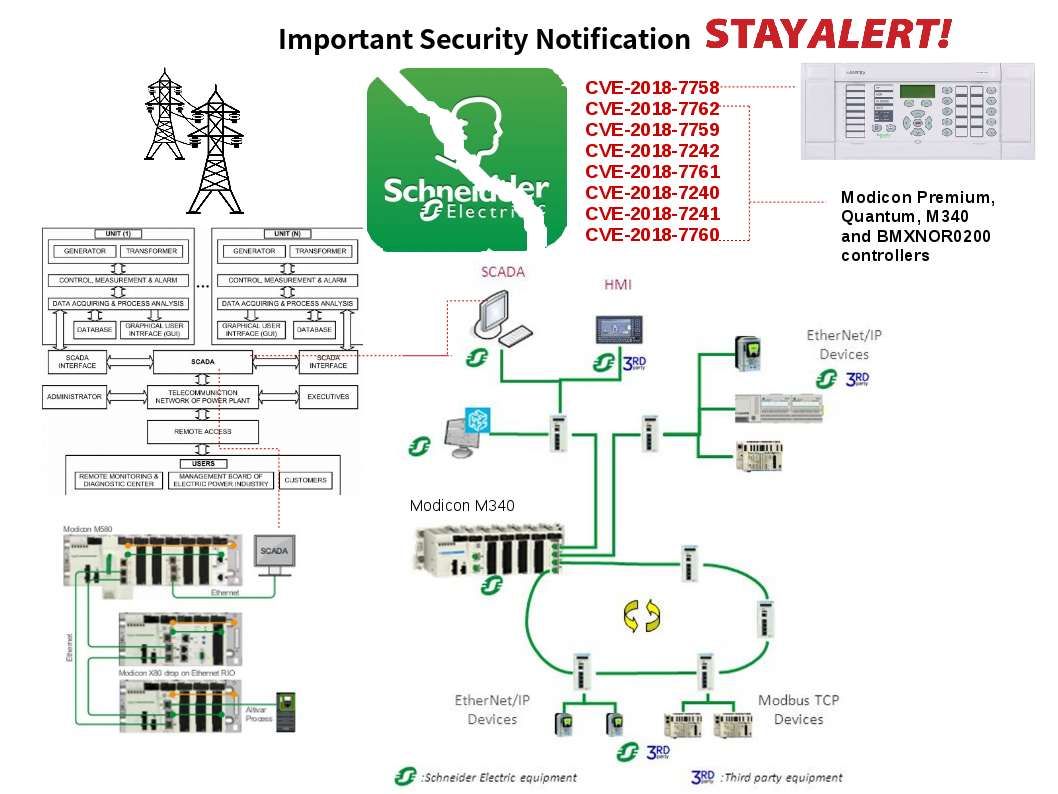
Predict the target – Electricity power facility, water supply and Gas supply facilities
SCADA system are popular and pay a major role in modern industrial automation including manufacturing production control, building facilities electricity devices control, etc. I believe that these areas do not lure the hacker interest. As usual, threat actors will remain unchanged focusing in the following critical public faciliteis.
Electricity power facility, water supply and Gas supply facilities.
In regards to vendor announcement last few month. The popular brand name of SCADA major supplier has vulnerabilities occured. Perhaps the SCADA owner applied the patch and completed the remediation. However the SCADA kernel more relies on Microsoft product based operating system. So we must consider is there any new security announcement by vendor. Below details are the vulnerabilities encountered last few months.
Allen Bradley – The design flaw of the programmable logic controller – system vulnerability

Oil refinery industry security alert! CVE-2018-4841

SCADA manufacturer security awareness awaken – ABB

Vulnerability in SCADA CODESYS Web Server CVE-2018-5440

Predict the target – logistic delivery (marine)
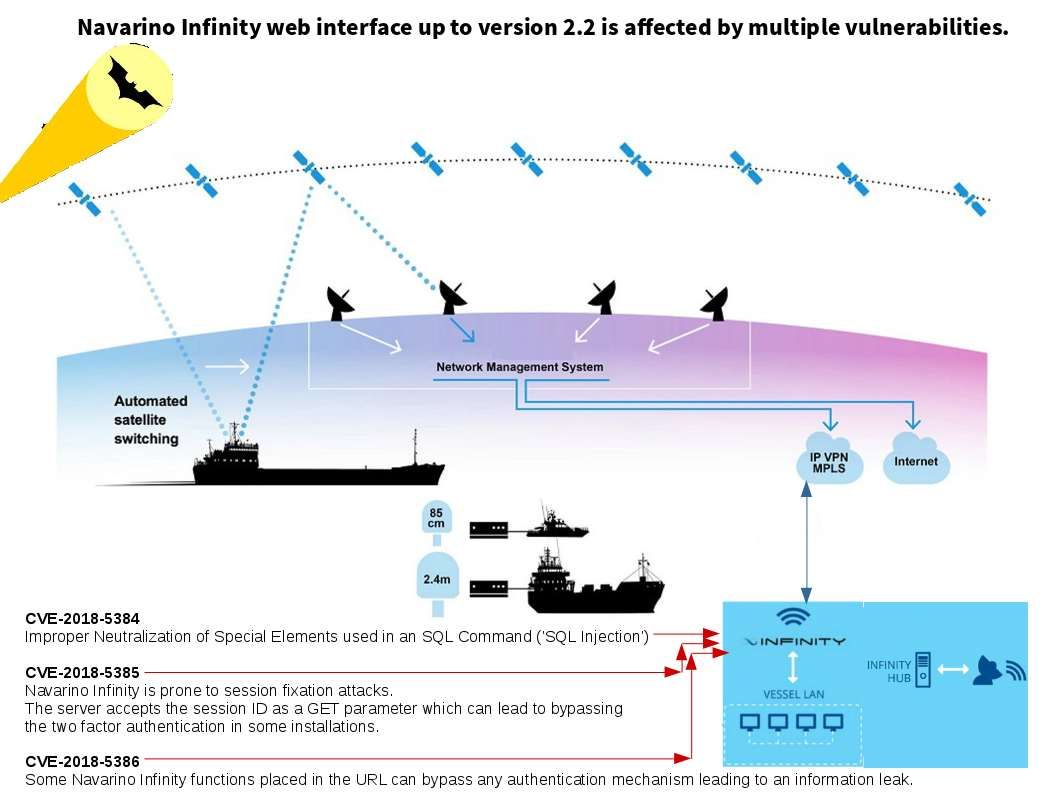
Hacker might interrupt the maritime bandwidth management system relies on vulnerabilities if it did not complete the patch. The specify vulnerability causes shipping traffic jam or suspend the logistic delivery. Whereby the marine industry especially container shipping company must stayed alert.
Navarino Infinity web interface is affected by multiple vulnerabilities
About situation of France
France under terrorist attack in frequent. The terrorist attack on 2017 are happened 8 times. The most recent of attack causes 5 people dead. Perhaps there is less hit rate of cyber attack shown on top of newspaper. Even though the overall situation is unkown. However the similar cirtical level of cyber attack will be happened in that place.
At the end, I wishing that justice will be win the battle. “In God We Trust“.
— End —