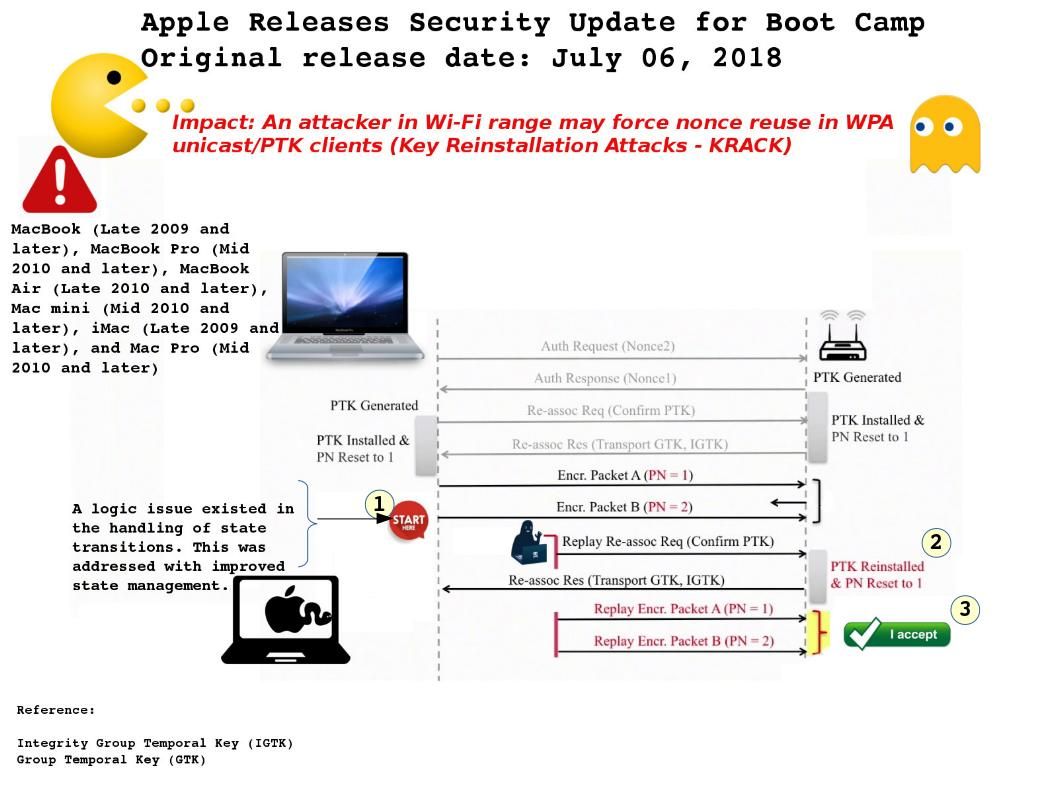
WiFi connection seems secure when IT Department authenticating wifi users with windows active directory. A know issue told the world that WPA is not secure and therefore the WiFi authentication best practices jump to WPA2. From general point of view, we all focusing to WiFi access point, authentication protocol and encryption method. It looks that we forget endpoint itself is our missing area. A design weakness found on Apple Mac book products. The explanation by Apple is that a logic issue existed in the handling of state transitions. See attached diagram, when endpoint enforce packet number (PN) reset to 1. Then the attacker possible to engage the replay attack.
Impact: An attacker in Wi-Fi range may force nonce reuse in WPA unicast/PTK clients (Key Reinstallation Attacks – KRACK)
Comment: With WPA/WPA2, rekeying of both unicast and global encryption keys is required. Seems WPA2 is the main trend today. So WPA looks ignore by manufacturer. And therefore is going to fix the bug in WPA now!
Official announcement – https://support.apple.com/en-us/HT208847