
Cyber defense facilities today are very strong and effecive to fight against different of cyber attacks. Even though stealer deploy DNS steal technique to exfiltrate the data from a firm. Anti cyber technology have their way to quarantine and deny such activities. Perhaps you said the IoT devices attack that wreaked hovac worldwide. It is hard to avoid. But it still have resolution. Cyber security vendor deploy network discover facitiles. No matter Dot one X or non Dot one X devices they can find. So it looks perfect, no any concern any more. But why we still have cyber attack incident happens today?
The Next Cyber Battleground
Sound scary! The Next Cyber Battleground
Expert predict that digital infrastructure is the high target to receive cyber attack. That is even through smart City, manufacturing automation, geospatial data system,..etc.
Some experts believe cyber incidents go underreported in the nuclear sector. The reason is that the Nuclear Regulatory Commission only requires the reporting of incidents that affect the safety, security functions, or emergency preparedness of the plant. May be it do not want to caused a public panic.
We heard cyber attack to SCADA in frequent. Whether SCADA contains design weakness or there is other factor?
The SCADA Data Gateway (SDG) is a Windows™ application used by System Integrators and Utilities to collect data from OPC, IEC 60870-6 (TASE.2/ICCP), IEC 61850, IEC 60870-5, DNP3, or Modbus Server/Slave devices and then supplies this data to other control systems supporting OPC, IEC 60870-6 (TASE.2/ICCP) Client, IEC 60870-5, DNP3, and/or Modbus Client/Master communication protocols.
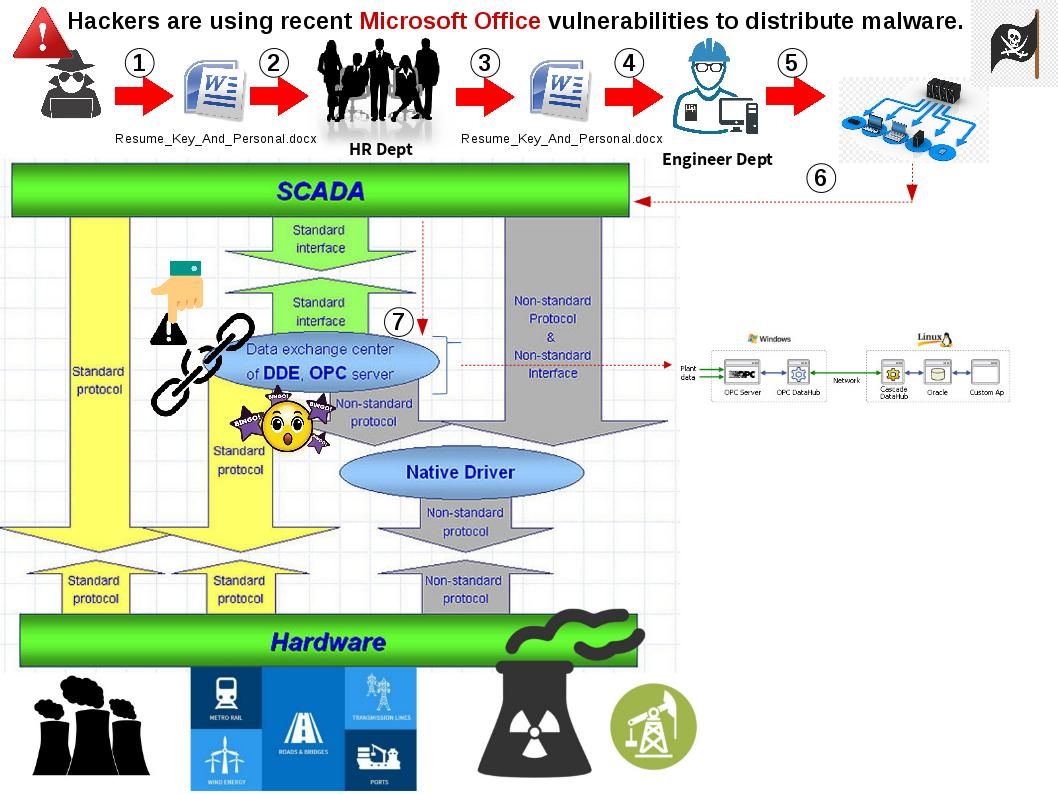
The core component supporting SCADA infrastructure build by Microsoft products in common. And therefore the attack surface will be divided in several ways. We understand that Nuclear facilties do not provided any public web portal. So direct attacks looks not possible. However Microsoft office products has full market coverage in the world. It is rare that people not using MS-Word for word processing work, right? As a matter of fact, hacker now transform MS office product become a cyber attack media. They re-use former MS office vulnerabilities. It has possibilities execute the Infiltration. From technical point of view, even though attacker send out the RTF format of file. It is also workable.
Remark: RTF is a text file format used by Microsoft products, such as Word and Office. RTF, or Rich Text Format, files were developed by Microsoft in 1987 for use in their products and for cross-platform document interchange. RTF is readable by most word processors.
Quote:
Hackers are using Microsoft Word documents (or more specifically, RTF files listed with a “.doc” extension) to trick people into opening the files.
On this discussion objective, I am not going to drill into any technical details. But our aim would like to provides hints see whether it can enrich the security awareness.
Below details common bad mailicious MS-word documents checklist for reference.
| 722154A36F32BA10E98020A8AD758A7A | MD5 | FILENAME:CV Controls Engineer.docx |
| 243511A51088D57E6DF08D5EF52D5499 | MD5 | FILENAME:CV Control Engeneer.docx |
| 277256F905D7CB07CDCD096CECC27E76 | MD5 | FILENAME:CV Jon Patrick.docx |
| 4909DB36F71106379832C8CA57BA5BE8 | MD5 | FILENAME:Controls Engineer.docx |
| 4E4E9AAC289F1C55E50227E2DE66463B | MD5 | FILENAME:Controls Engineer.docx |
| 5C6A887A91B18289A70BDD29CC86EBDB | MD5 | FILENAME:High R-Value Energy.docx |
| 6C3C58F168E883AF1294BBCEA33B03E6 | MD5 | FILENAME:CV_Jon_Patrick.docx |
| 78E90308FF107CE38089DFF16A929431 | MD5 | FILENAME:CV Jon Patrick.docx |
| 90514DEE65CAF923E829F1E0094D2585 | MD5 | FILENAME:CV_Jon_Patrick.docx |
| C1529353E33FD3C0D2802BB558414F11 | MD5 | FILENAME:Build Hydroelectric Turbine.docx |
| CDA0B7FBDBDCEF1777657182A504283D | MD5 | FILENAME:Resume_Key_And_Personal.docx |
| DDE2A6AC540643E2428976B778C43D39 | MD5 | FILENAME:CV_Jon_Patrick.docx |
| E9A906082DF6383AA8D5DE60F6EF830E | MD5 | FILENAME:CV_Jon_Patrick.docx |
| 038A97B4E2F37F34B255F0643E49FC9D | MD5 | FILENAME:Controls Engineer (2).docx |
| 31008DE622CA9526F5F4A1DD3F16F4EA | MD5 | FILENAME:Controls Engineer (4).docx |
| 5ACC56C93C5BA1318DD2FA9C3509D60B | MD5 | FILENAME:Controls Engineer (7).docx |
| 65A1A73253F04354886F375B59550B46 | MD5 | FILENAME:Controls Engineer (3).docx |
| 8341E48A6B91750D99A8295C97FD55D5 | MD5 | FILENAME:Controls Engineer (5).docx |
| 99AA0D0ECEEFCE4C0856532181B449B1 | MD5 | FILENAME:Controls Engineer (8).docx |
| A6D36749EEBBBC51B552E5803ED1FD58 | MD5 | FILENAME:Controls Engineeer.docx |
| 3C432A21CFD05F976AF8C47A007928F7 | MD5 | FILENAME:Report03-23-2017.docx |
| 34A11F3D68FD6CDEF04B6DF17BBE8F4D | MD5 | FILENAME:corp_rules(2016).docx |
| 141E78D16456A072C9697454FC6D5F58 | MD5 | FILENAME:corp_rules(2016).docx |
| BFA54CCC770DCCE8FD4929B7C1176470 | MD5 | FILENAME:invite.docx |
| 848775BAB0801E5BB15B33FA4FCA573C | MD5 | FILENAME:Controls Engineer.docx |
| MD5 | FILENAME:corp_rules(2016).docx | |
| MD5 | FILENAME:corp_rules(2016).docx | |
| MD5 | FILENAME:invite.docx |
Happy hunting – bye!