
Preface:
Using Big Data and data mining methods to predict attacks before they happen,the Cisco Umbrella Security Research team built such detection framework.
Point of view:
a. Vulnerability routers are vulnerable to Shell Metacharacters Attack
Regarding to the observation result of Cisco Talos security team. There are group of router devices are vulnerable. They are Linksys, MikroTik, Netgear, and TP-Link, as well as QNAP network-attached storage (NAS) devices. I am not going to repeat the attack details because nobody will be describe as clear as Cisco findings (see below url for reference)
https://blog.talosintelligence.com/2018/05/VPNFilter.html
However a hints given to me that they are all vulnerable for Shell Metacharacters attack. What is Shell Metacharacters attack? A metacharacter is a character that has a special meaning (instead of a literal meaning) to a computer program, such as a shell interpreter or a regular expression engine. … Otherwise, the parenthesis, plus-sign, and asterisk will have a special meaning. In the sense that those routers containes design weakness may let the router misbehave. For instance it accept arbitrary command execution through shell metacharacters in a URL.

Botnet from earlier phase relies on workstations engage the attack convert to smartphones in last few years. Most likely the security enhancement in workstations and smartphones improved. The threat actors found the new victims today.It is a low-end wireless router.
So below items are the guidance:
- Never trust input
- Prefer rejecting data to filtering data
- Every component should validate data
Whereby the way to validate the input are:
- Indirect selection – application never directly uses user input
- Whitelist
- Blacklist
If required input, do the validation actions:
- Sanitize – Attempt to fix input by removing dangerous parts
- Refuse to use invalid input
- Record invalid input in log file
- Alert – send notification to related personnel
b. Behavioral Analysis discovered adnormal traffic pattern
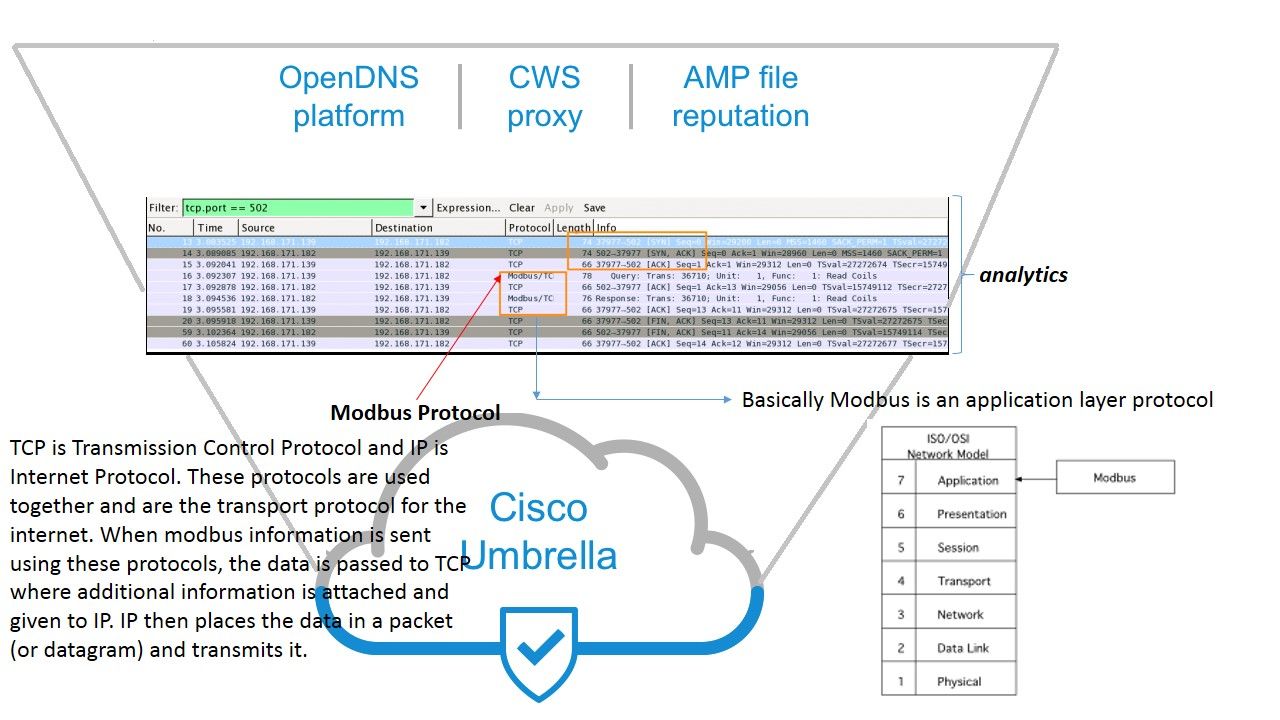
There are design weakness of modbus protocol. Basically modbus is an application layer protocol. However the MODBUS/TCP protocol implementation contains multiple vulnerabilities that could allow an attacker to perform reconnaissance activity or issue arbitrary commands.
- All MODBUS messages are transmitted in clear text across the transmission media.
- There are no integrity checks built into the MODBUS application protocol. As a result, it depends on lower layer protocols to preserve integrity.
- There is no authentication at any level of the MODBUS protocol. One possible exception is some undocumented programming commands.
- MODBUS/TCP consists of short-lived transactions where the master initiates a request to the slave that results in a single action. When combined with the lack of authentication and poor TCP initial sequence number (ISN) generation in many embedded devices, it becomes possible for attackers to inject commands with no knowledge of the existing session.
Regarding to item no.1 design weakness. The SCADA system vendor will be recommend client make use of VPN tunnel to encrypted the traffic for remediation. Whereby hacker created working directory (/var/run/vpnfilterw) in compromised router to record the modbus traffic. And therefore user credential will be found by hacker.
c. Compromised routers and NAS transform to weaponize tool
Cisco statiscally calculate there are estimated 500,000 devices has been compromised. A hints highlights by security expert that attacker creates a configuration file in /var/run/torrc and a working directory in /var/run/tord. A evasion of detection mechanism technique since it is a encrypted communication. The command and control server is able to drive the compromised router to start the cyber attack to nuclear power facilities. Refer to above four items of modbus vulnerbilities. The QNAP network-attached storage (NAS) will be transform become a attack tool. The kernel of NAS contains linux command is able to use it. For instance execute a nping command craft packet to bother the nuclear facility. Meanwhile the hacker is able to install python or php library with script to execute the attack (Reference to above item number 4).
Summary:
In the meantime, we are waiting for more information provided by Cisco.Perhaps attackers engage the attack. No news is good news, agree, Right?
Anything updating will keep you posted.
— End —
24th May 2018 – status update:
FBI take control of APT28’s. They are the suspect threat actor of this attack.
The US Federal Bureau of Investigation (FBI) has obtained court orders and has taken control of the command and control servers of a massive botnet of over 500,000 devices, known as the VPNFilter botnet.
Headline news article for reference.
Justice Department Announces Actions to Disrupt Advanced Persistent Threat 28 Botnet of Infected Routers and Network Storage Devices