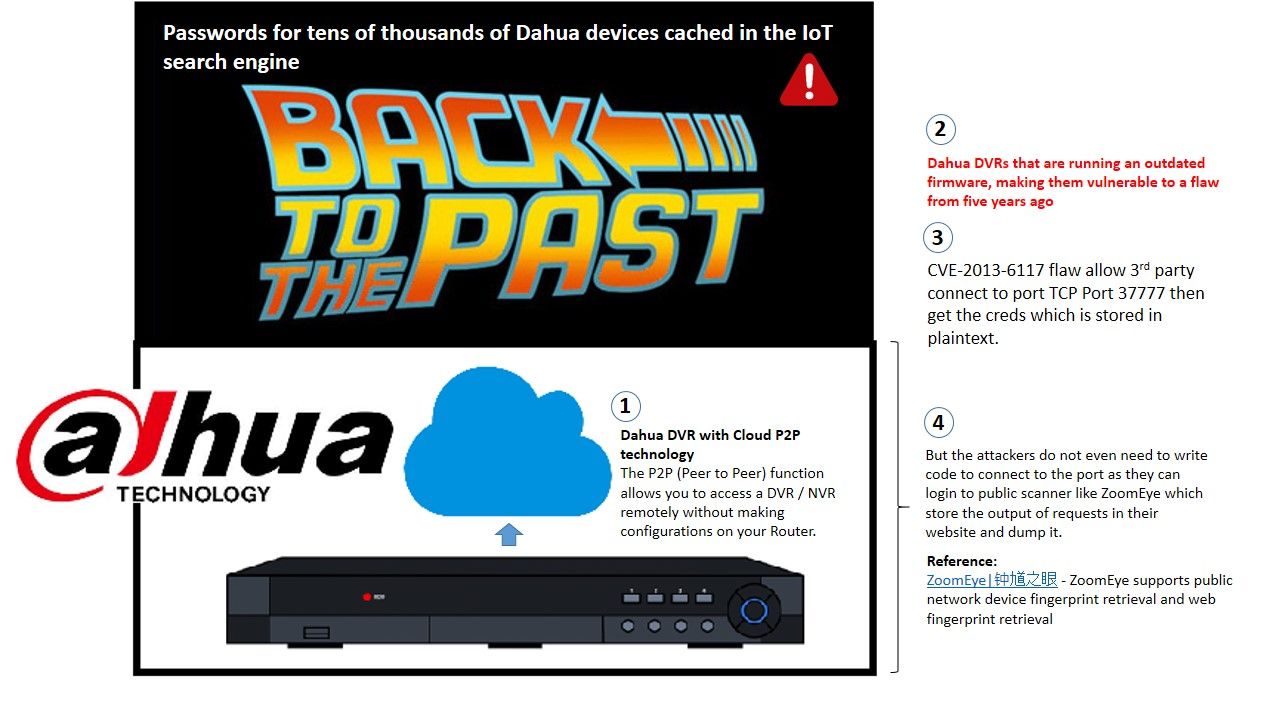
The P2P (Peer to Peer) function is common function for the operation support for Internet of things devices. It aim to simplify the operation and increasing flexibility. We now focusing on data personal privacy but the fundamental of user friendly functions looks contained contradiction with secure operation. The firm (NewSky security) found password for tens of thousands of Dahua devices cached in the IoT search engine. In the meantime the hardware manufacturer not provides any responses in regard to this incident. Stay tuned! And see whether what is the reply by hardware vendor.
Should you have interested to know the details, please refer to attached diagram and url for references.
Passwords for tens of thousands of Dahua devices cached in the IoT search engine – https://amazingreveal.com/2018/07/15/passwords-for-tens-of-thousands-of-dahua-devices-cached-in-the-iot-search-engine/
Official Announcement/Notice – https://www.dahuasecurity.com/support/cybersecurity/annoucementNotice
Vulnerability found recently
Have you ever considered publishing an e-book or guest authoring on other
blogs? I have a blog centered on the same subjects you discuss and would really like
to have you share some stories/information. I know my viewers would value your work.
If you are even remotely interested, feel free to shoot me an e
mail.
It is perfect time to make some plans for the future and it is time to be happy.
I’ve read this post and if I could I want to suggest you some
interesting things or suggestions. Maybe you can write next articles referring to this article.
I wish to read more things about it!