Preface: Das U-Boot (subtitled “the Universal Boot Loader” and often shortened to U-Boot.
Background: Das U-Boot is an open-source boot loader used in embedded devices to perform various low-level hardware initialization tasks and boot the device’s operating system kernel. It is available for a number of computer architectures, including 68k, ARM, Blackfin, MicroBlaze, MIPS, Nios, SuperH, PPC, RISC-V and x86.
Best practice: A bootloader design on the ARM platform is way different than what we have seen so far on the x86 platform. On the ARM platform, the minimalist bootloader design needs to implement the Trusted Board Boot (TBB) feature. The TBB feature allows the platform to be protected from malicious firmware attack by implementing a chain of trust (CoT) at each firmware level up to the normal world bootloader. Trusted Firmware (TF) implements a subset of the TBB requirements for ARM reference platform.
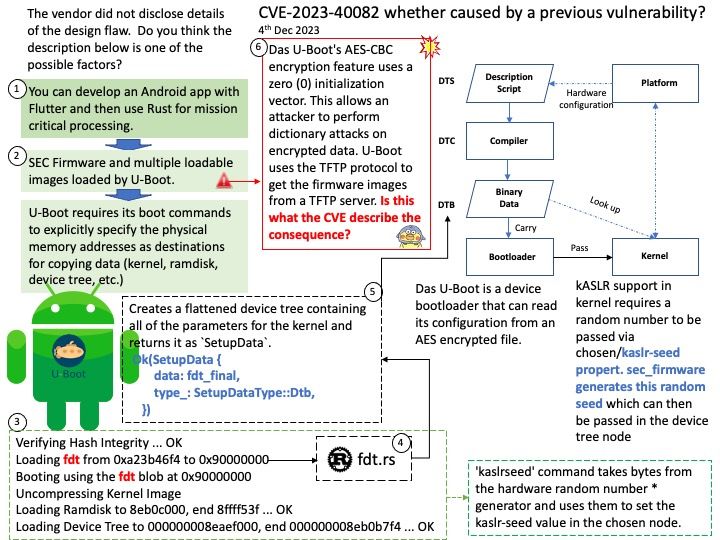
Vulnerability details: In modify for next stage of fdt.rs, there is a possible way to render KASLR ineffective due to improperly used crypto.This could lead to remote escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-40082