Preface: Null pointer dereference vulnerability can be exploited by hackers to maliciously crash a process to cause a denial of service. Can null pointer cause memory leak? This memory leak is caused by overwriting a pointer to allocated memory with either another valid pointer, or with a NULL pointer.
Background:
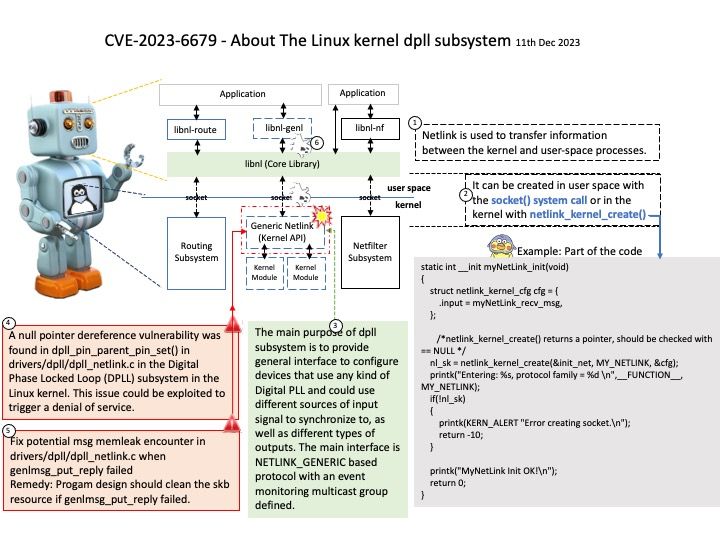
PLL – Phase Locked Loop is an electronic circuit which syntonizes clock signal of a device with an external clock signal. Effectively enabling device to run on the same clock signal beat as provided on a PLL input.
DPLL – Digital Phase Locked Loop is an integrated circuit which in addition to plain PLL behavior incorporates a digital phase detector and may have digital divider in the loop. As a result, the frequency on DPLL’s input and output may be configurable.
The main purpose of dpll subsystem is to provide general interface to configure devices that use any kind of Digital PLL and could use different sources of input signal to synchronize to, as well as different types of outputs. The main interface is NETLINK_GENERIC based protocol with an event monitoring multicast group defined.
Vulnerability details: A null pointer dereference vulnerability was found in dpll_pin_parent_pin_set() in drivers/dpll/dpll_netlink[.]c in the Digital Phase Locked Loop (DPLL) subsystem in the Linux kernel. This issue could be exploited to trigger a denial of service.
Additional: Fix potential msg memleak encounter in drivers/dpll/dpll_netlink[.]c when genlmsg_put_reply failed
Remedy: Progam design should clean the skb resource if genlmsg_put_reply failed.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-6679