Preface: PostgreSQL allocates memory from the work_mem pool when a query requires sorting or hashing. If there is not enough memory available in the work_mem pool, PostgreSQL will spill to disk. temp_buffers controls the amount of memory allocated for temporary tables.
Does Postgres write to disk? To guard against unforeseen failures, PostgreSQL periodically writes full page images to permanent storage before modifying the actual page on disk. By doing this, during crash recovery PostgreSQL can restore partially-written pages.
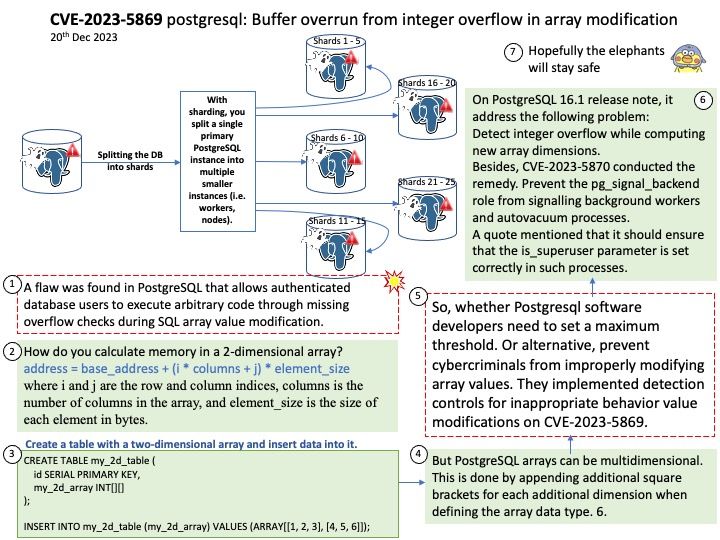
Background: Declaring an array in PostgreSQL is straightforward. An array data type is defined by appending square brackets [] to any valid data type. This could be an array of integers, text, boolean values, or even more complex data types like composite types or other arrays.
Many databases support array fields of a scalar type. SQL allows ARRAY column types. In PostgreSQL INTEGER[5] represents an array of 5 integers.
Vulnerability details: A flaw was found in PostgreSQL that allows authenticated database users to execute arbitrary code through missing overflow checks during SQL array value modification. This issue exists due to an integer overflow during array modification where a remote user can trigger the overflow by providing specially crafted data. This enables the execution of arbitrary code on the target system, allowing users to write arbitrary bytes to memory and extensively read the server’s memory.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-5869