Preface: But what is the significance of SPS keywords? Qualcomm didn’t mention it. Let’s trace if we can find what are the weak points of the design?
Background: The Qualcomm Secure Processing Unit is an isolated hardware security core implemented in the Snapdragon 8cx Gen 3 Mobile Compute Platform SoC. As such, this security core incorporates standalone ROM, RAM, CPU, cryptographic acceleration units, countermeasure sensors, one-time programmable memory, etc. Key generation, signing and verification utilizing RSA and ECC cryptosystems across a range of modes.
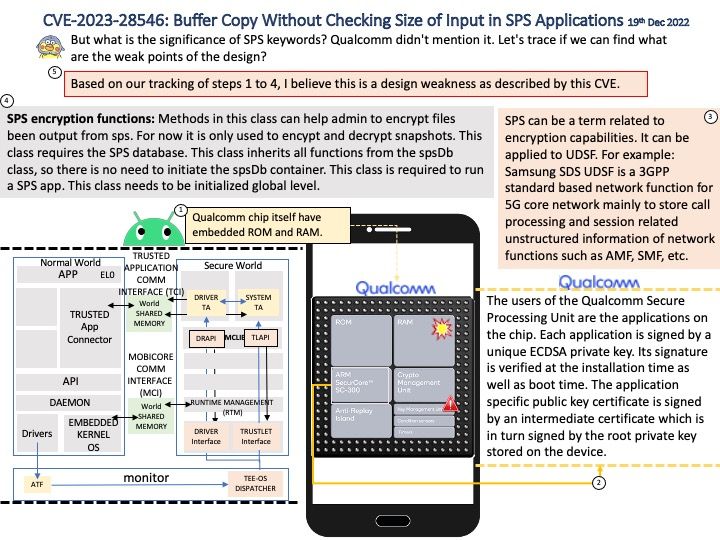
Ref: SPS can be a term related to encryption capabilities. It can be applied to UDSF. For example: Samsung SDS UDSF is a 3GPP standard based network function for 5G core network mainly to store call processing and session related unstructured information of network functions such as AMF, SMF, etc.
SPS encryption functions: Methods in this class can help admin to encrypt files been output from sps. For now it is only used to encypt and decrypt snapshots. This class requires the SPS database. This class inherits all functions from the spsDb class, so there is no need to initiate the spsDb container. This class is required to run a SPS app. This class needs to be initialized global level.
Vulnerability details: Memory Corruption in SPS Application while exporting public key in sorter TA.
Official announcement: Please refer to the link for details –
https://nvd.nist.gov/vuln/detail/CVE-2023-28546
https://docs.qualcomm.com/product/publicresources/securitybulletin/december-2023-bulletin.html