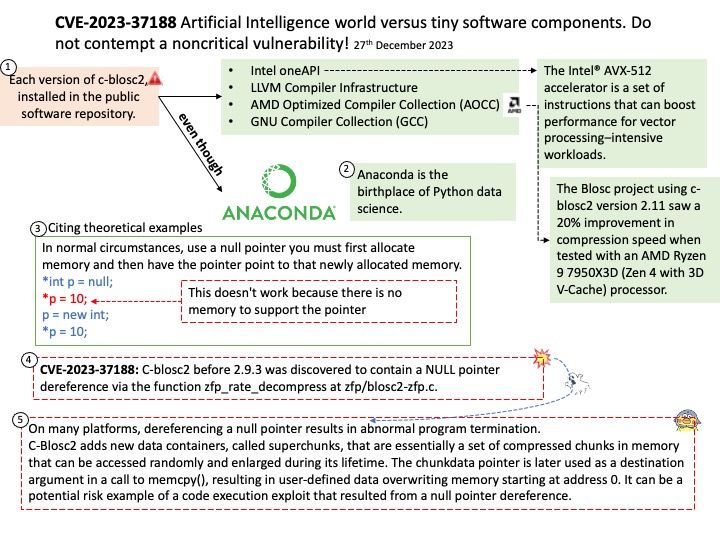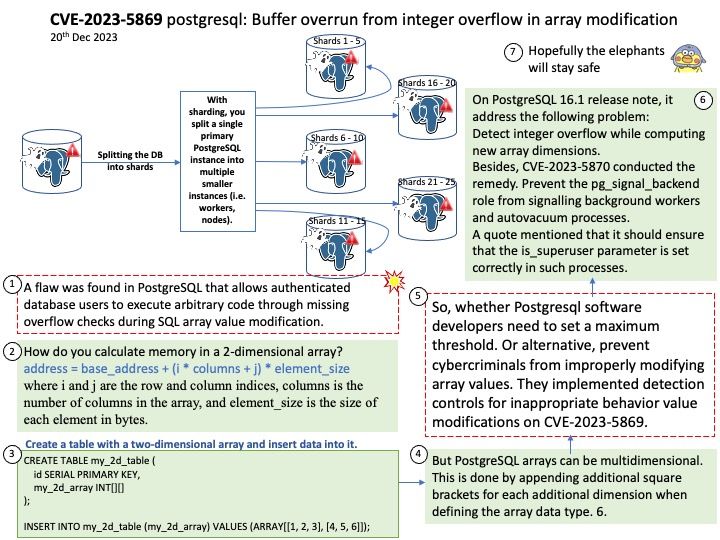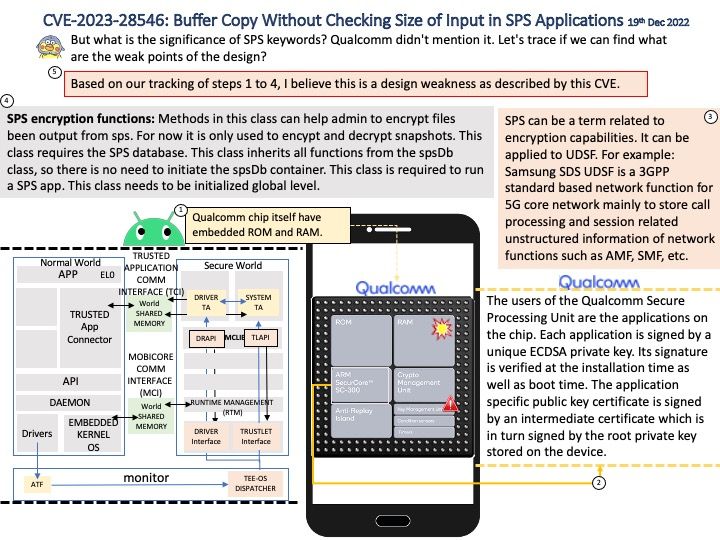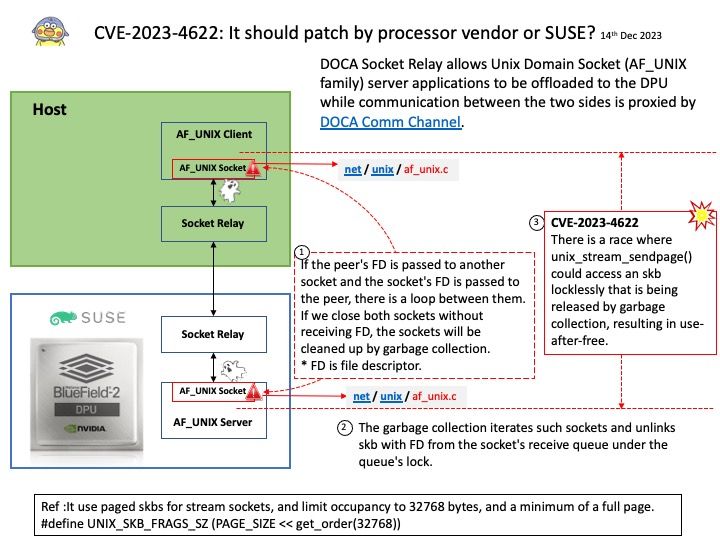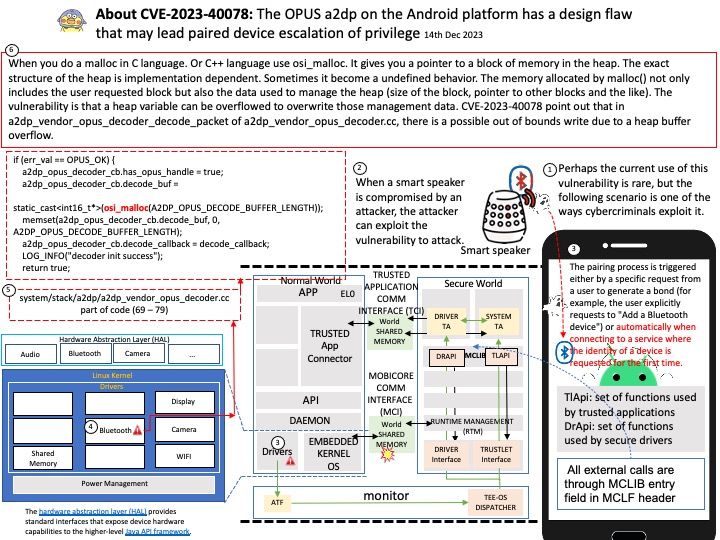
Preface: Under normal circumstances, CVEs are recorded sequentially every year. Microsoft announced CVE-2024-21318 on January 9, 2024. It’s the start of a new year, and this record let me speculated that whether there are plenty of design weakness found in 2023. But it is waiting to be verified. Due to the huge amount of data, it need to wait for the official CVE reference number. So, it carry forward to 2024. This brings the total to five figures.
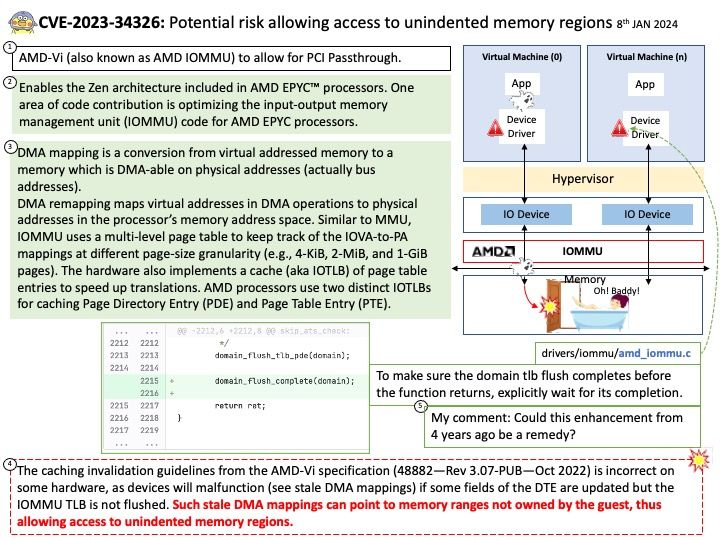
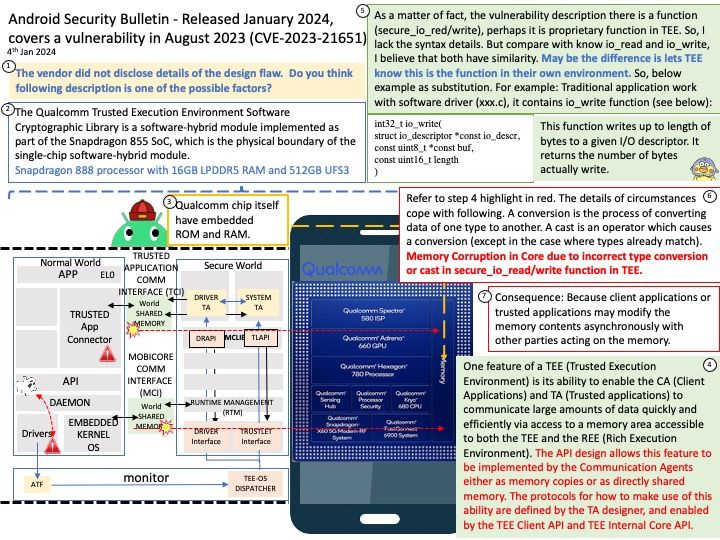
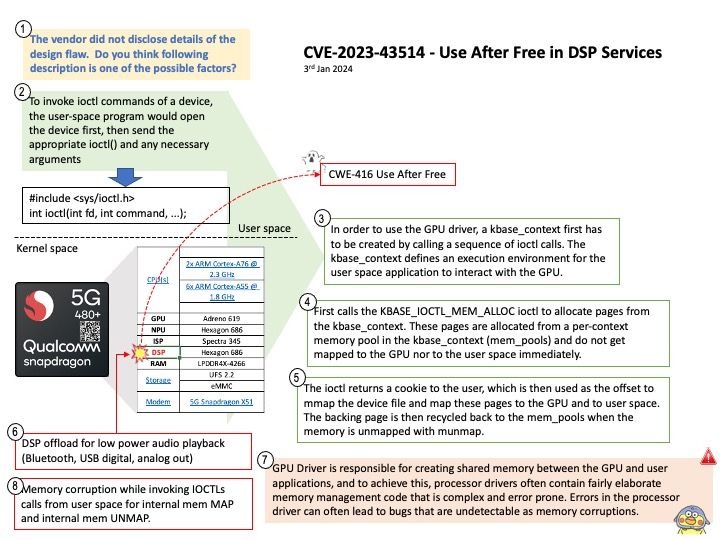
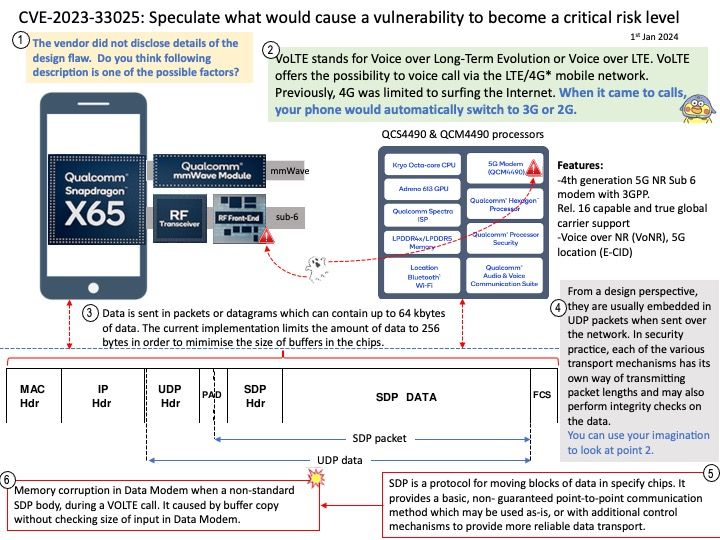
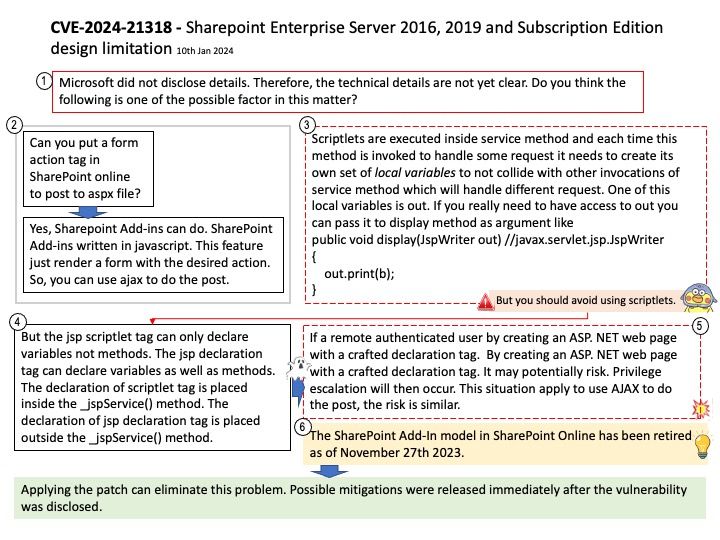
Background: Microsoft did not disclose details. Therefore, the technical details are not yet clear. Do you think SharePoint Add-in is one of the possible factor in this matter?
A SharePoint Add-in is a self-contained piece of functionality that extends the capabilities of SharePoint websites to solve a well-defined business problem. Add-ins don’t have custom code that runs on SharePoint servers. Instead, all custom logic moves “up” to the cloud, or “down” to client computers, or “over” to an on-premises server that is outside the SharePoint farm or SharePoint Online subscription. Keeping custom code off SharePoint servers provides reassurance to SharePoint administrators that the add-in can’t harm their servers or reduce the performance of their SharePoint Online websites.
Business logic in a SharePoint Add-in can access SharePoint data through one of the several client APIs included in SharePoint. Which API you use for your add-in depends on certain other design decisions you make.
Vulnerability details: Microsoft SharePoint Server Remote Code Execution Vulnerability. Technical details unknown.
Remedy: Applying the patch can eliminate this problem. Possible mitigations were released immediately after the vulnerability was disclosed.
Official announcement: Please refer to the link for details –
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-21318