.jpg?width=1920&height=1080&fit=bounds)
Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
Background: FortiAnalyzer platforms integrate network logging, analysis, and reporting into a single system, delivering increased knowledge of security events throughout your network. FortiManager provides automation-driven centralized management of your Fortinet devices from a single console. Both devices operate in a network-based structure. Therefore, it requires a web browser or CLI (command line) for the end user to work.
Vulnerability details: An improper handling of insufficient permissions or privileges vulnerability [CWE-280] in FortiAnalyzer and FortiManager may allow an authenticated attacker to bypass the device policy and force the password-change action for its user.
My observation My observation (one of the possibilities): Authentication bypass vulnerabilities exist when authentication state is not consistently enforced on the devices (FortiAnalyzer and FortiManager). As a result, it can be tampered by clients.
The vulnerability risk level is not high (CVSS v3=3.9). But it will let you know more. The client can arbitrarily change the GET parameters sent with the request. Nothing prevents the client from simply changing the parameter value. It effectively bypassing policy. Since this vulnerability in low risk (enforce password change to its user). Whether there will be unknown problems, we do not know.
Official announcement – For details, please refer to the link – https://www.fortiguard.com/psirt/FG-IR-21-255
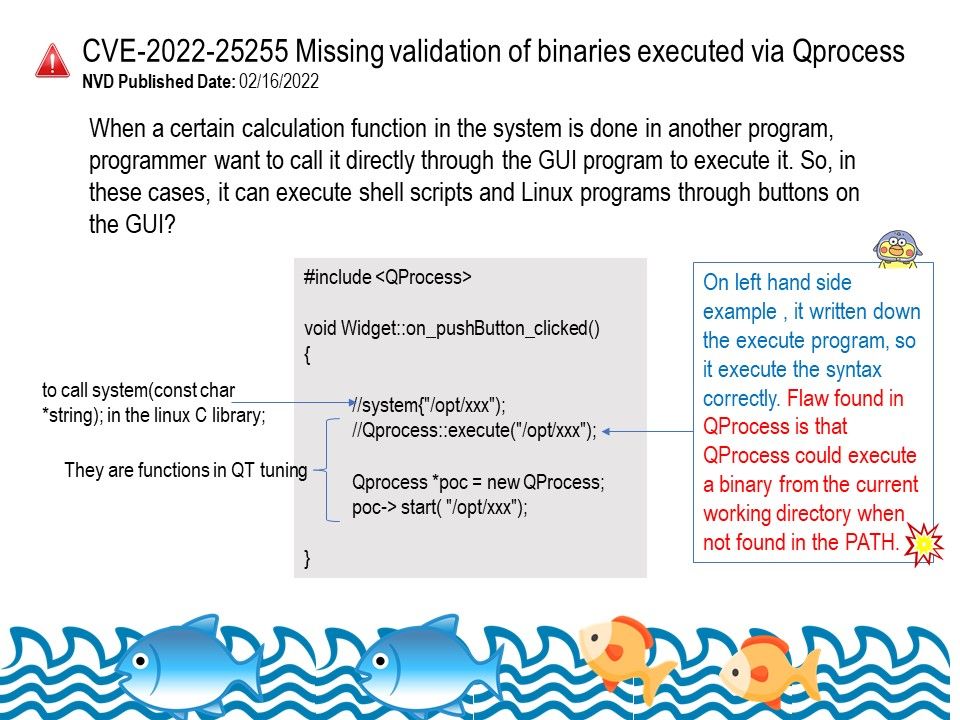
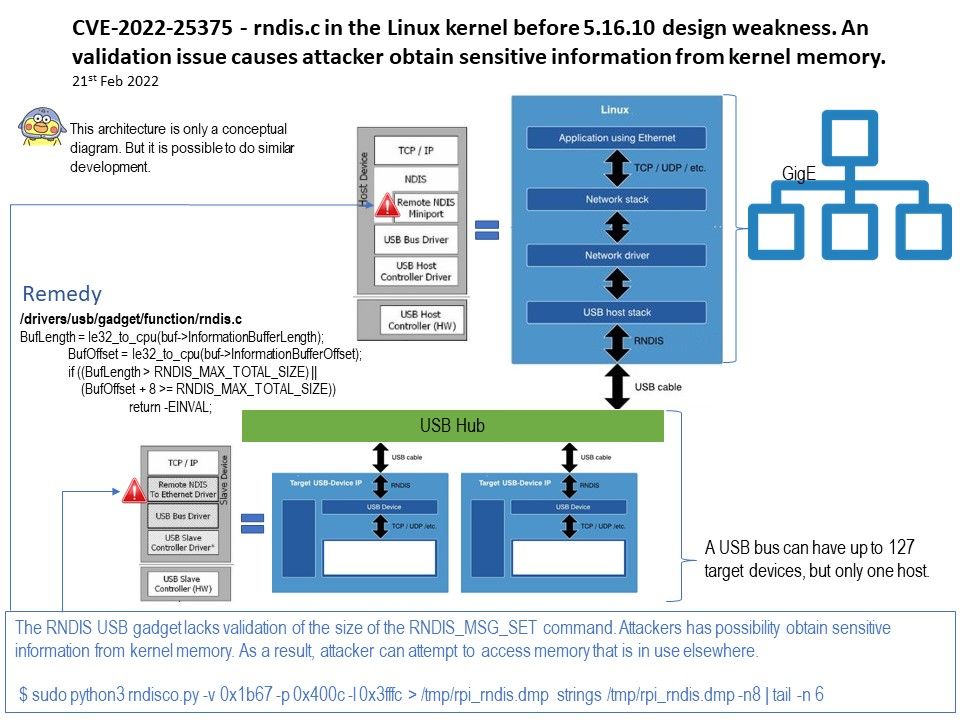
.jpg?width=1920&height=1080&fit=bounds)
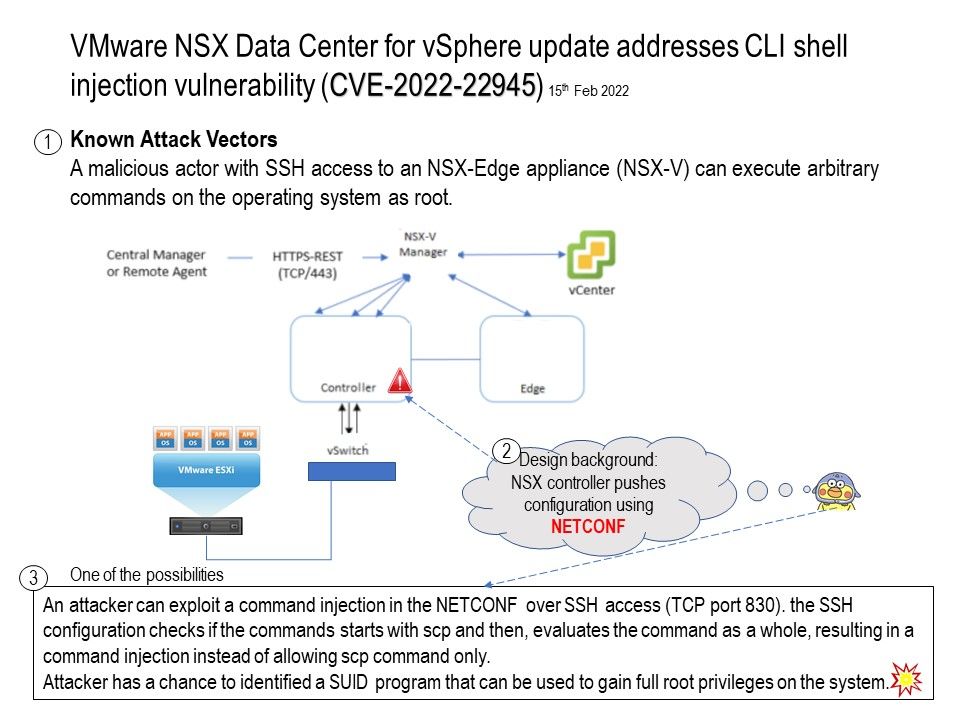
.jpg?width=1920&height=1080&fit=bounds)