
Preface: According to market survey, there are 3723 companies reportedly use Elasticsearch in their tech stacks, including Uber, Shopify, and Udemy. Perhaps part of the 3723 companies will use Kibana at the same time.
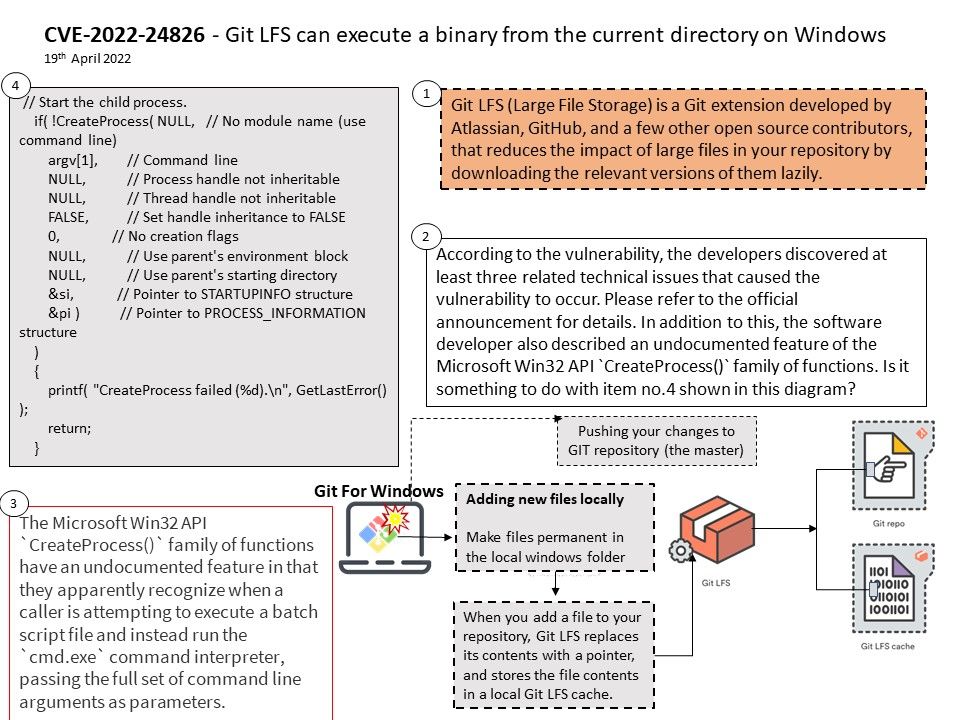
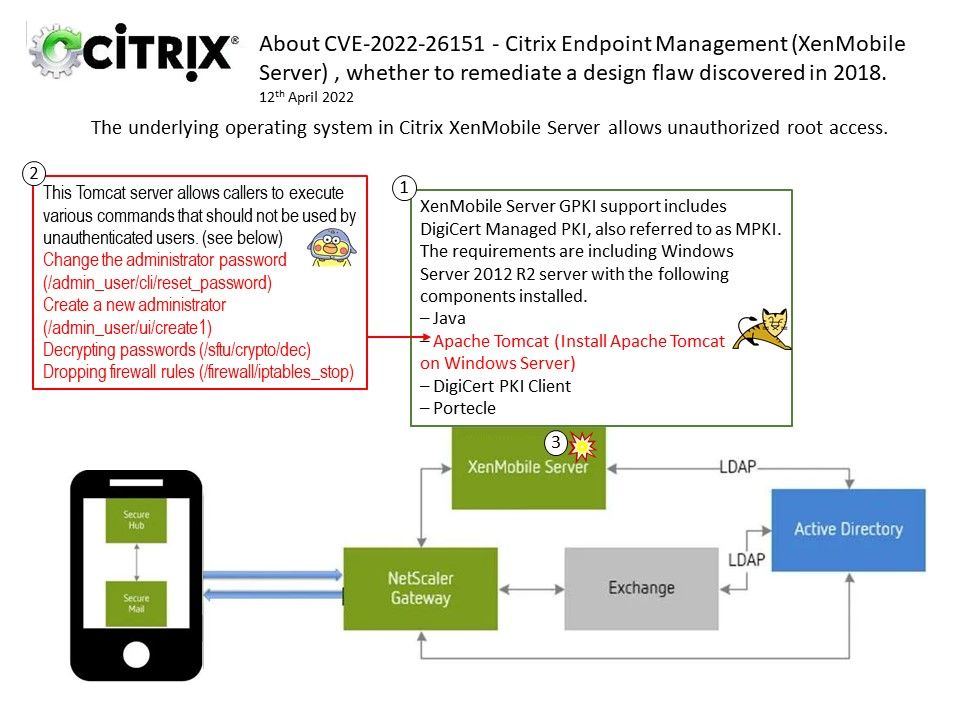
Background: As suggested by Elasticsearch, customers can install Kibana on the same server as Elasticsearch. But that’s not the only setup method that can be used.
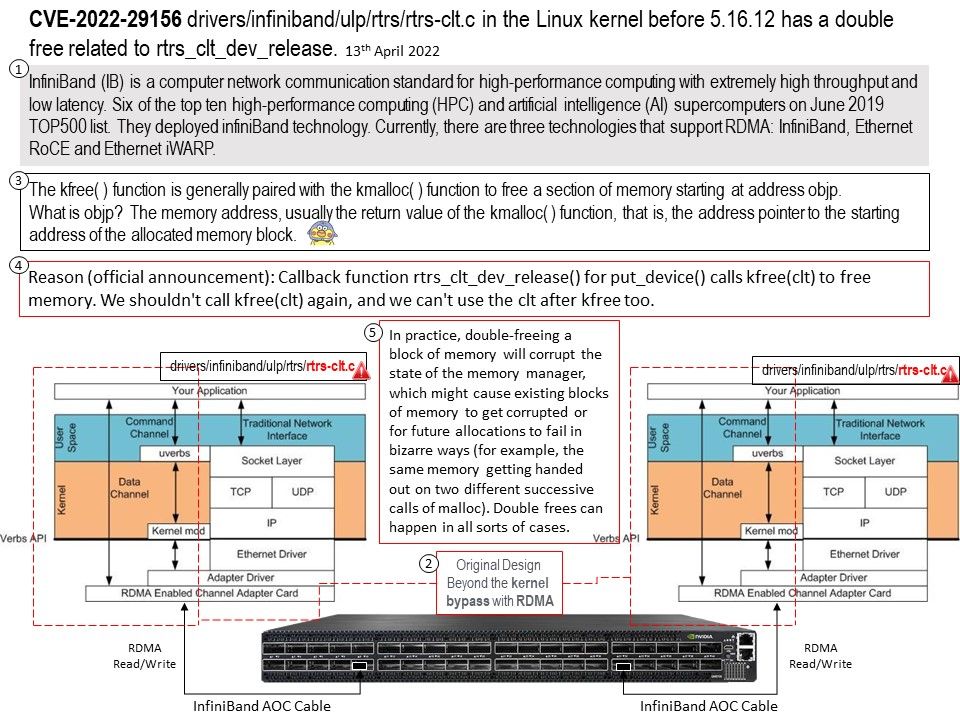
Elasticsearch allows you to store, search, and analyze huge volumes of data quickly and in near real-time and give back answers in milliseconds. It’s able to achieve fast search responses because instead of searching the text directly, it searches an index.
By default, data is retrieved from the cluster specified in the elasticsearch.hosts value in the kibana.yml file. If you want to retrieve it from a different cluster, set monitoring.ui.elasticsearch.hosts.
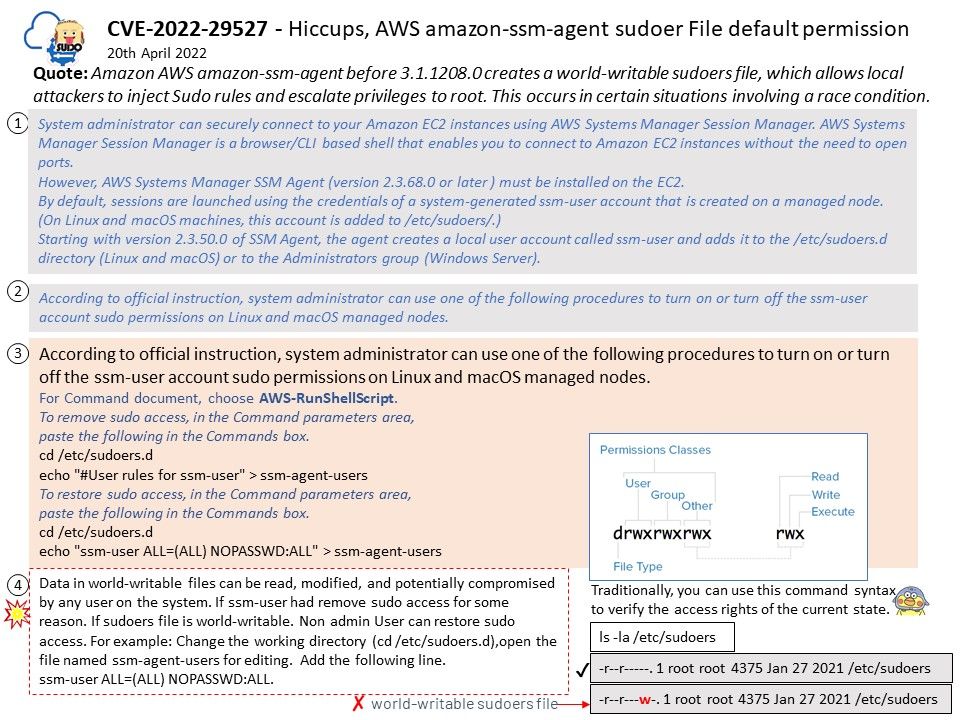
Kibana is a free and open user interface that lets you visualize your Elasticsearch data and navigate the Elastic Stack. Do anything from tracking query load to understanding the way requests flow through your apps.
Vulnerability details: A vulnerability in Kibana could expose sensitive information related to Elastic Stack monitoring in the Kibana page source. Elastic Stack monitoring features provide a way to keep a pulse on the health and performance of your Elasticsearch cluster. Authentication with a vulnerable Kibana instance is not required to view the exposed information. The Elastic Stack monitoring exposure only impacts users that have set any of the optional monitoring.ui.elasticsearch.* settings in order to configure Kibana as a remote UI for Elastic Stack Monitoring. The same vulnerability in Kibana could expose other non-sensitive application-internal information in the page source.
Doubt: Kibana can retrieve monitoring event logs. See attached diagram (item 5). User IDs and passwords are not encrypted. Since the vulnerability is not described in detail. Whether this the reason said that it expose sensitive information?
Official announcement: For official details, please refer to the link https://discuss.elastic.co/t/kibana-7-17-3-and-8-1-3-security-update/302826
.jpg)
.jpg)