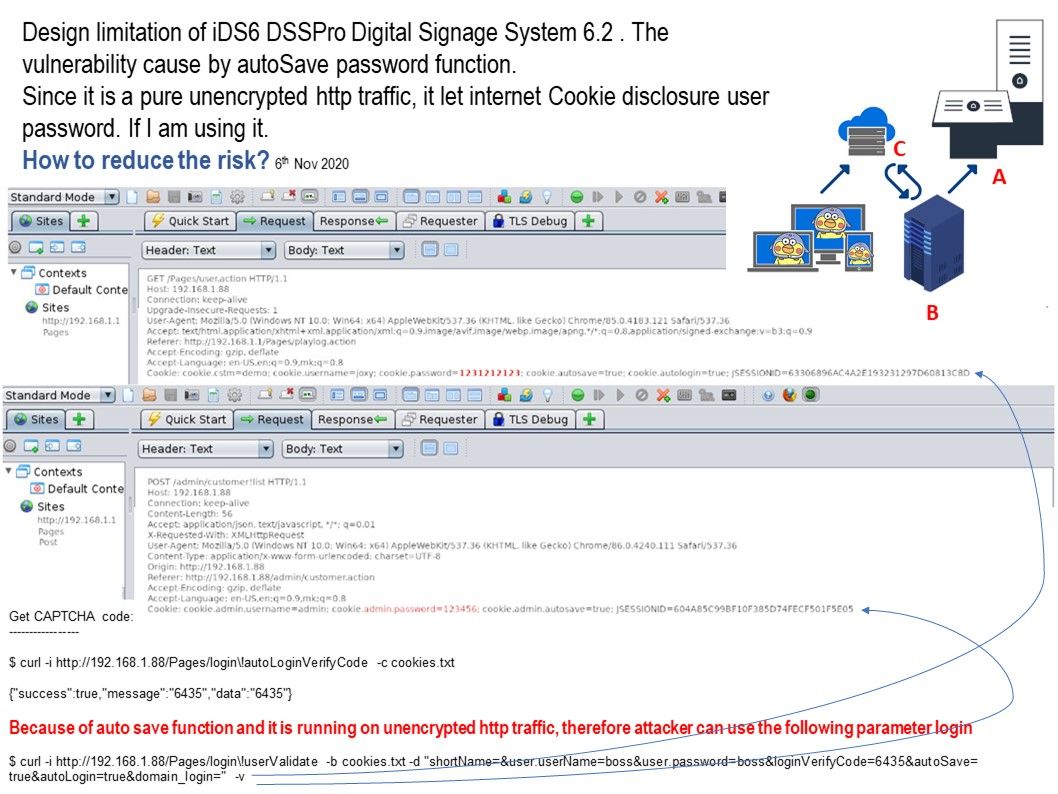
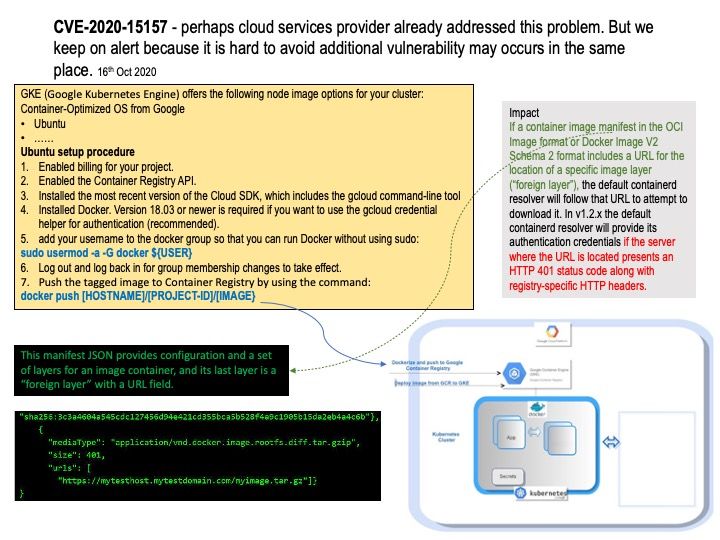
.jpg?width=1920&height=1080&fit=bounds)
Preface: With the advent of the 5G era, starting in 2019, UFS 3.0 has gradually been adopted by flagship smartphones.
UFS 3.1 is an optimized version of 3.0.
Background: The RPMB layer aims to provide in-kernel API for Trusted Execution Environment (TEE) devices that are capable to securely compute block frame signature. In case a TEE device wish to store a replay protected data, it creates an RPMB frame with requested data and computes HMAC of the frame, then it requests the storage device via RPMB layer to store the data.
A storage device registers its RPMB (eMMC) partition or RPMB
W-LUN (UFS) with the RPMB layer providing an implementation for
rpmb_cmd_seq() handler. The interface enables sending sequence of RPMB standard frames.
Vulnerability details: The RPMB protocol allows an attacker to replay stale write failure messages and write commands, leading to state confusion between a trusted component and the contents of an RPMB area. Since the impact not explicitly confirm by vendor yet. See below url for reference.
Western Digital – https://www.westerndigital.com/support/productsecurity/wdc-20008-replay-attack-vulnerabilities-rpmb-protocol-applications
Netapp – https://security.netapp.com/advisory/ntap-20201113-0005/
CERT Coordination Center – https://kb.cert.org/vuls/id/231329
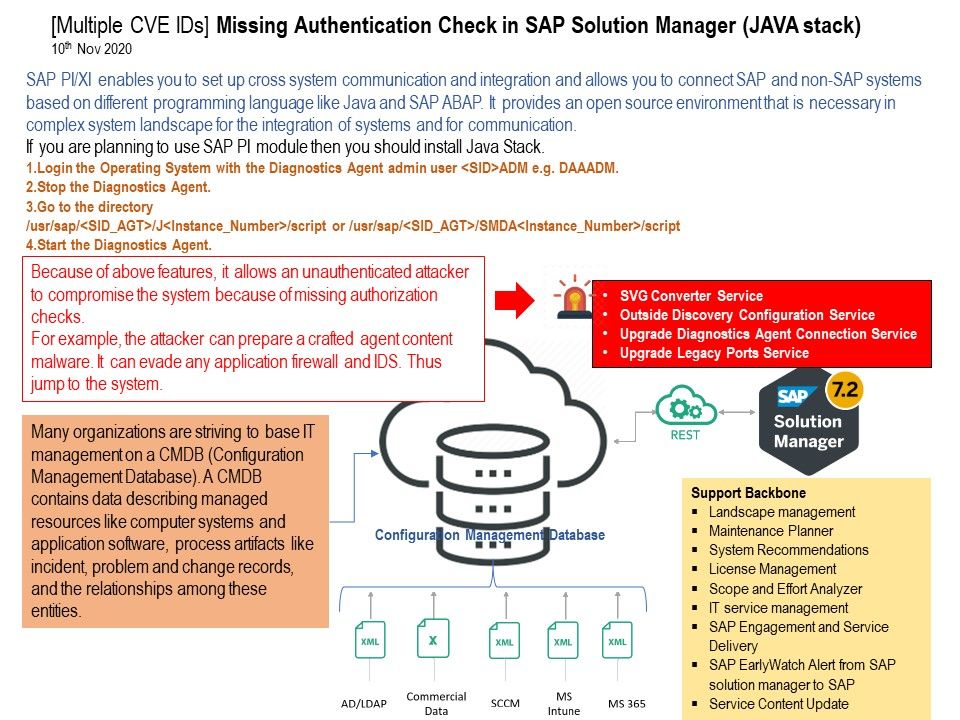
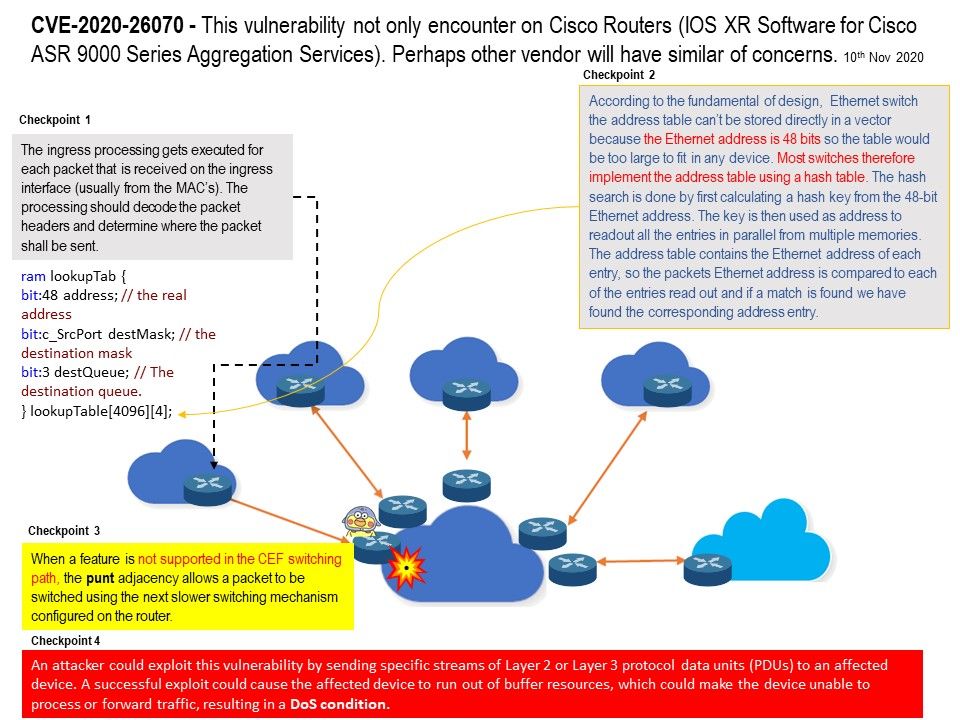
.jpg?width=1920&height=1080&fit=bounds)