Preface: On Dec 2022, Microsoft has warned that malicious hackers were able to get the software giant to digitally sign their code so it could be used in attacks, such as the deployment of ransomware.
Background: The newest update to AMD’s P-State EPP Linux driver hit today, offering better Ryzen & EPYC performance & better power control on CPUs.
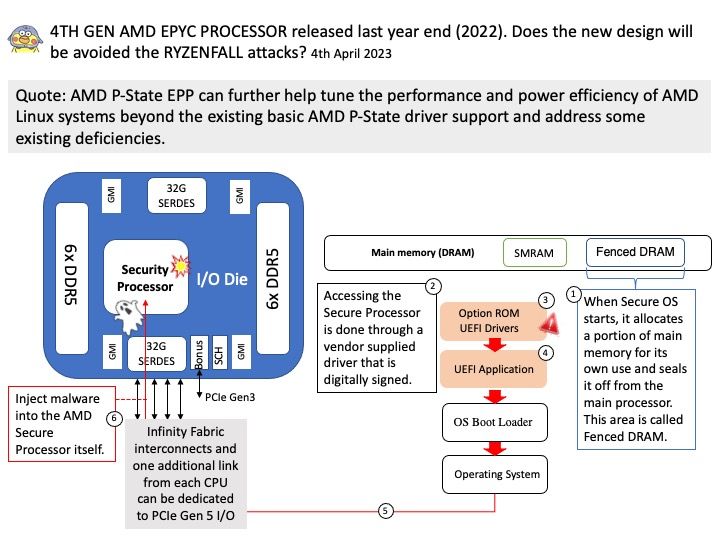
AMD P-State EPP can further help tune the performance and power efficiency of AMD Linux systems beyond the existing basic AMD P-State driver support and address some existing deficiencies.
AMD EPYC processors are the only x86 server CPUs with an integrated, embedded security processor that is “hardened at the core” to help secure customer data whether in a central data center or distributed across locations at the network edge.
Observation of the subject: AMD confirms Ryzenfall vulnerabilities, but says they’ll be fixed soon via routine BIOS updates on 2018. From earlier stage, AMD has neither confirmed nor denied whether the attacks can be executed remotely, or require local access.
AMD has recently released a BIOS update that supposedly allows users disable the Secure Processor, but this feature works only partially and does not stop the RYZENFALL attacks. But some experts say this is not an effective mitigation measure.
What do you think? Do you think the specify design weakness still valid or it has fixed by vendor?