Prefect: The Lord taught Enoch that those who build their lives upon the Savior would never fall.
Don’t mind about it was really had Lord or advanced civilization, human being go to digitization. In bible it mention about Lucifer. It is similar to cyber threat actor.
Background: Technology trends from on-premises to cloud. Cloud-based attack most likely through below ways
– Compromised Laptop via Phishing Emails – The RansomCloud attack is a relatively new type of ransomware that targets cloud-based email services such as Office 365.
– Compromised Server via Unpatched Vulnerabilities
Based on cyber defense capabilities, we believe that major cloud service providers will have effective ways to deal with disruptions caused by cyber attacks.
However , more and more native applications rely on CSPs’ API. For example: Push notification, push messages, or notifications, through its cloud messaging service. However Applications running on mobile devices, browsers or IoT devices can use push technology. For example: application-to-application (A2A) and application-to-person (A2P) communication.
A2A provides high-throughput, push-based, many-to-many messaging between distributed systems, microservices, and event-driven serverless applications.
Push notifications can be cloud-based or app-based, and are built to work with a server that provides the notification. An API can enable push notifications from cloud services as app and web push services. Once an organization requests a push notification, an API calls this service and sets the message in place to be delivered.
Push API can use these capabilities in order to spread fake or deceptive messages, flood the user’s device with spam, and trick people into installing malicious apps.
Remark: Push API is the general term for all push APIs.
Ref: Push notifications can be cloud-based or app-based, and are built to work with a server that provides the notification. An API can enable push notifications from cloud services as app and web push services. Once an organization requests a push notification, an API calls this service and sets the message in place to be delivered.
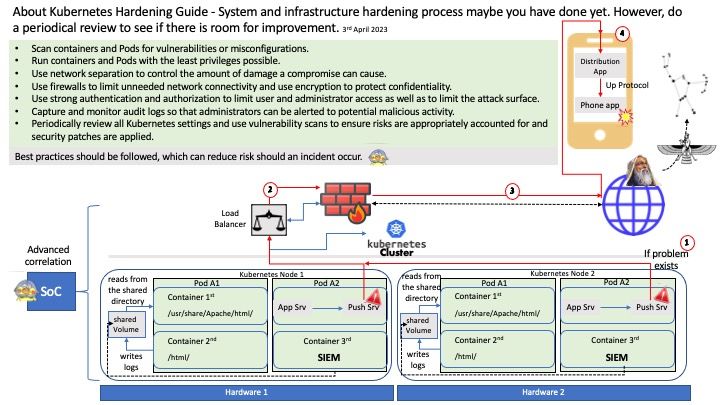
Technical details: My friend Enoch (CCIE) recommend Kubernetes Hardening Guide last week. In my view that it is good for preventive control. Since it is a lot of uncertainty in digital world. Be my guest, you can download on this official link.