Preface: Combining kTLS and sendfile() means data is encrypted directly in kernel space, before being passed to the network stack for transmission.
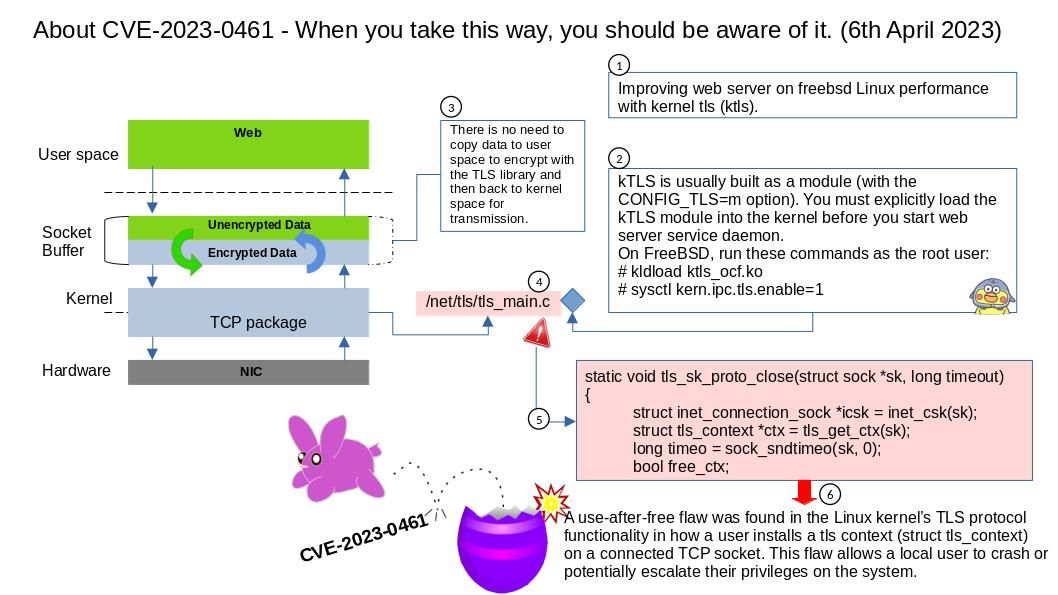
Background: improving web server on freebsd Linux performance with kernel tls (ktls).
Kernel TLS operation – Linux kernel provides TLS connection offload infrastructure. Once a TCP connection is in ESTABLISHED state user space can enable the TLS Upper Layer Protocol (ULP) and install the cryptographic connection state.
ktls can operate in three modes:
– Software crypto mode (TLS_SW)
– Packet-based NIC offload mode (TLS_HW)
– Full TCP NIC offload mode (TLS_HW_RECORD)
Vulnerability details: A use-after-free flaw was found in the Linux kernel’s TLS protocol functionality in how a user installs a tls context (struct tls_context) on a connected TCP socket. This flaw allows a local user to crash or potentially escalate their privileges on the system.
Resolution
– In order to prevent kernel modules loading during boot, the module name must be added to a configuration file for the “modprobe” utility. This file must reside in /etc/modprobe[.]d .
– Ensure the module is not configured to get loaded in either /etc/modprobe[.]conf, /etc/modprobe[.]d/*, /etc/rc[.]modules, or /etc/sysconfig/modules/* before making the following modifications.
For details, please refer to the link – https://access.redhat.com/solutions/41278