Preface: In computing, a segmentation fault (often shortened to segfault) or access violation is a fault, or failure condition, raised by hardware with memory protection, notifying an operating system (OS) the software has attempted to access a restricted area of memory (a memory access violation).
Background: NJS is a subset of the JavaScript language that allows extending NGINX functionality. njs is created in compliance with ECMAScript 5.1 (strict mode) with some ECMAScript 6 and later extensions.
To use njs in nginx:
- install njs scripting language
- create an njs script file
- in the nginx[.]conf file, enable ngx_http_js_module module and specify the js_import directive with the http[.]js script file.
Example: load_module modules/ngx_http_js_module.so
Vulnerability details: Nginx NJS v0.7.10 was discovered to contain a segmentation violation via the function njs_function_frame at src/njs_function[.]h.
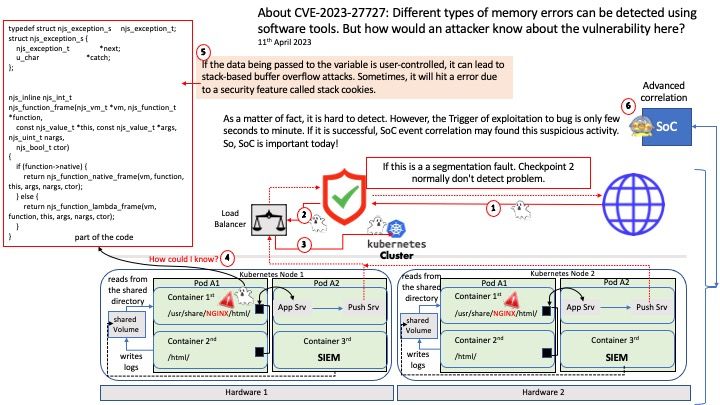
Observation: One of the possible ways. If the data being passed to the variable is user-controlled, it can lead to stack-based buffer overflow attacks. Sometimes, it will hit a error due to a security feature called stack cookies.
Official Announcement – Please refer to this link – https://nvd.nist.gov/vuln/detail/CVE-2023-27727
My comments below:
As a matter of fact, it is hard to detect. However the Trigger of exploitation to bug is only few seconds to minute. If it is successful, SoC event correlation may found this suspicious activity.
So, SoC is important today!