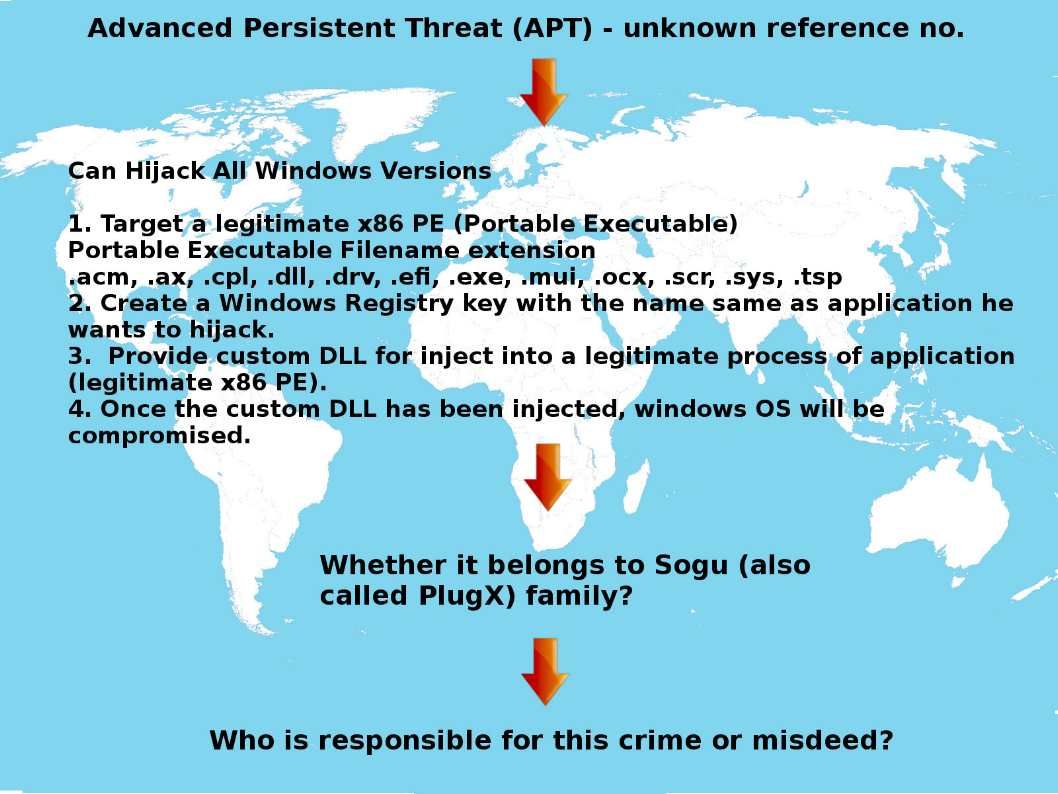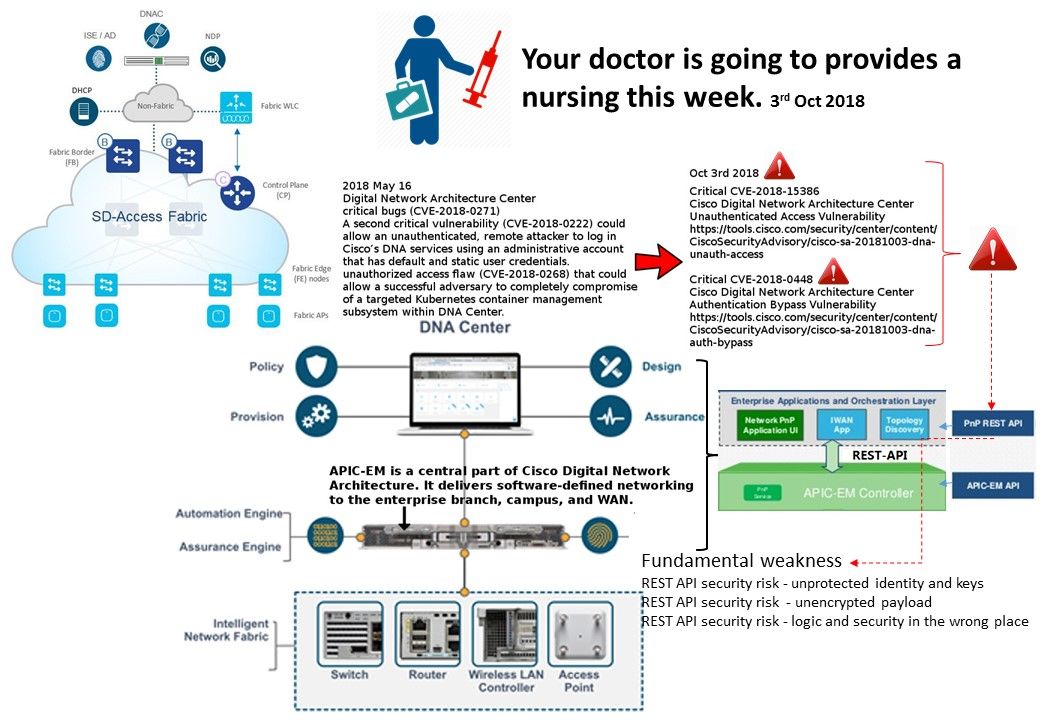
Preface:
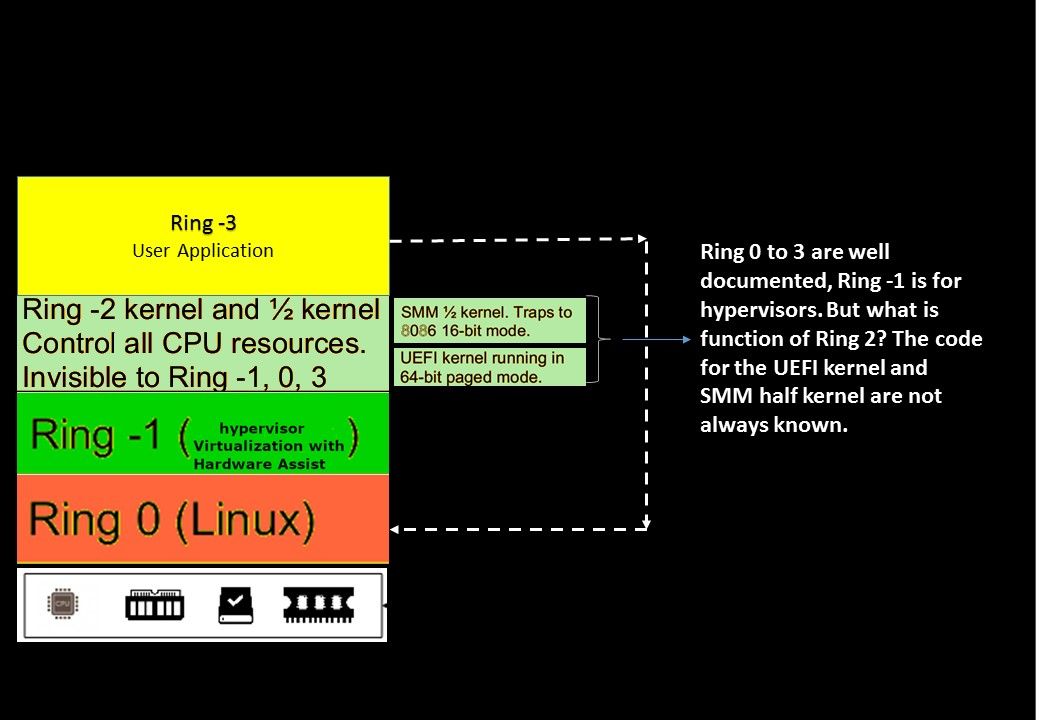
In x86 protected mode, the CPU is always in one of 4 rings. The Linux kernel only uses 0 and 3:
Hidden janitor living in your computer
SMM is triggered through a System Management Interrupt (SMI), a signal sent from the chipset to the CPU. During platform initialization, the firmware configures the chipset to cause a System Management Interrupt for various events that the firmware developer would like the firmware to be made aware of.
Whether you remember the Intel chipsets for some years have included a Management Engine?
On May 2017, an official announcement by Intel, design found a design limitation on their product. The problem is that Intel Active Management Technology, Intel Small Business Technology, and Intel Standard Manageability encountered vulnerability (escalation of Privilege). Reference url shown as below:
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00075.html
If we are not talking about conspiracy, it looks that backdoor appear in the chipset not a rumour. It is a true statement.
Why Ring 2 isn’t used?
Rings 1 and 2 is for the OS to put device drivers at that level, so they are privileged, but somewhat separated from the rest of the kernel code.
An exploitation on Ring 2
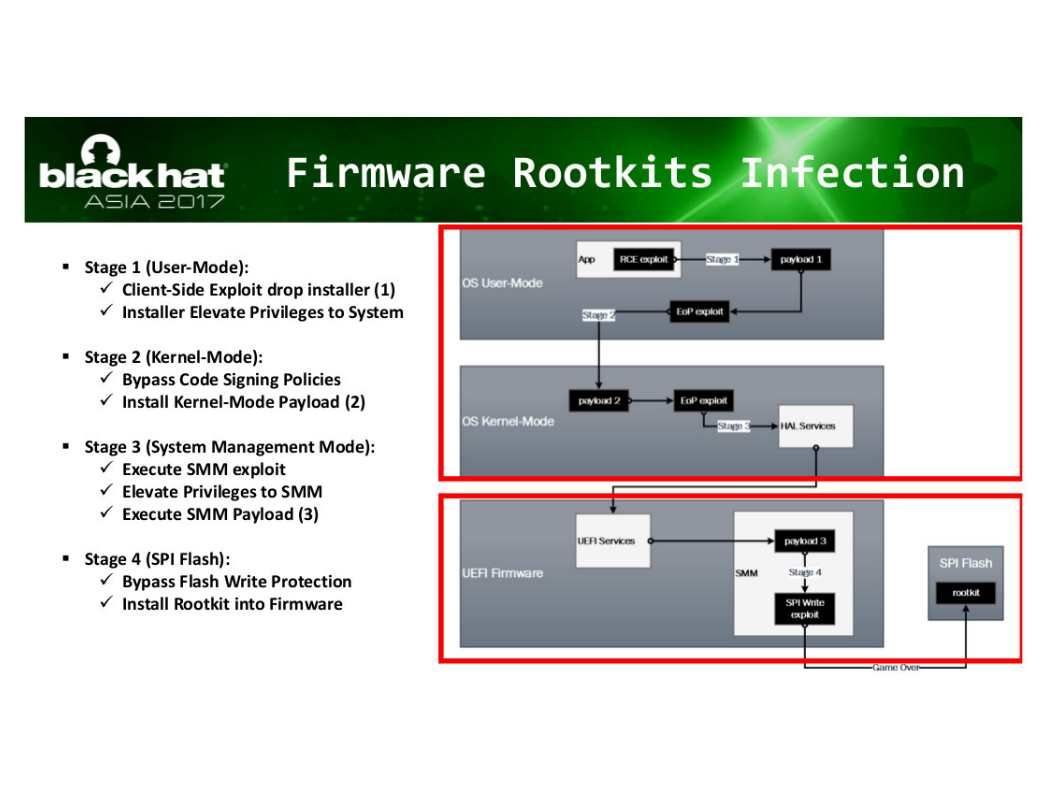
We strongly believe that the person who familiar of code for the UEFI kernel and SMM half kernel is the CPU manufacturer. Both components are run on Ring 2. Above mentioned Intel design flaw run in Ring -2 OS (UEFI). UEFI can run in 32-bit or 64-bit mode and has more addressable address space than BIOS, which means your boot process is faster. Unified Extensible Firmware Interface (UEFI) is a specification for a software program that connects a computer’s firmware to its operating system (OS). UEFI is expected to eventually replace BIOS. Like BIOS, UEFI is installed at the time of manufacturing and is the first program that runs when a computer is turned on. Dual boot computer with Windows and Linux conducted by UEFI firmware. But UEFI firmware has become a target for hackers.
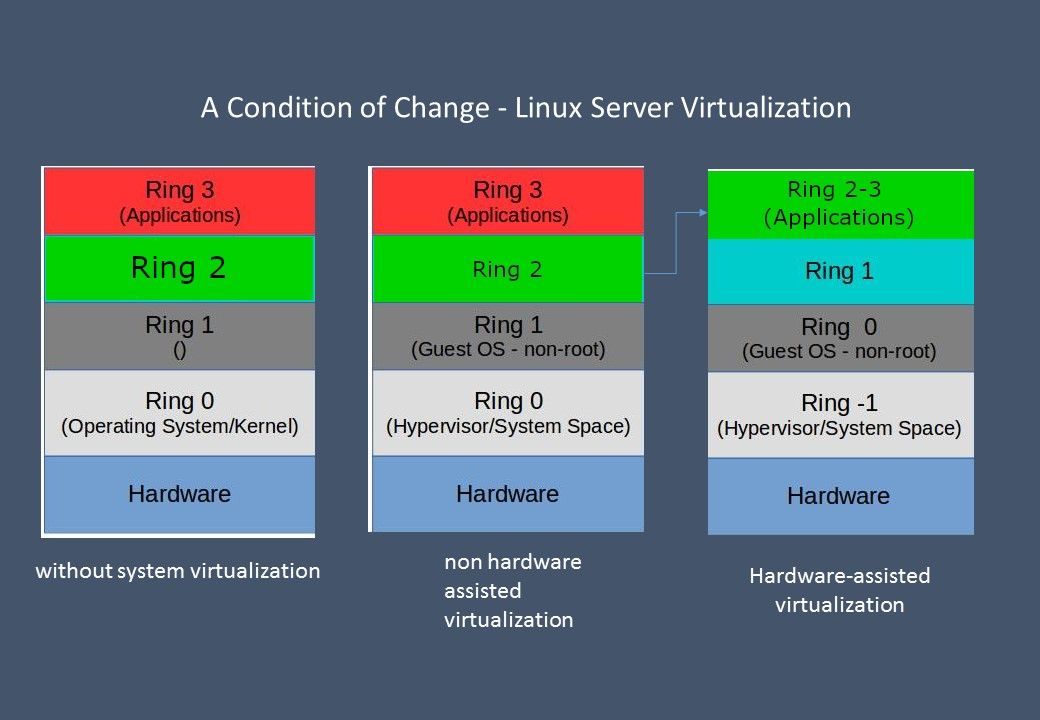
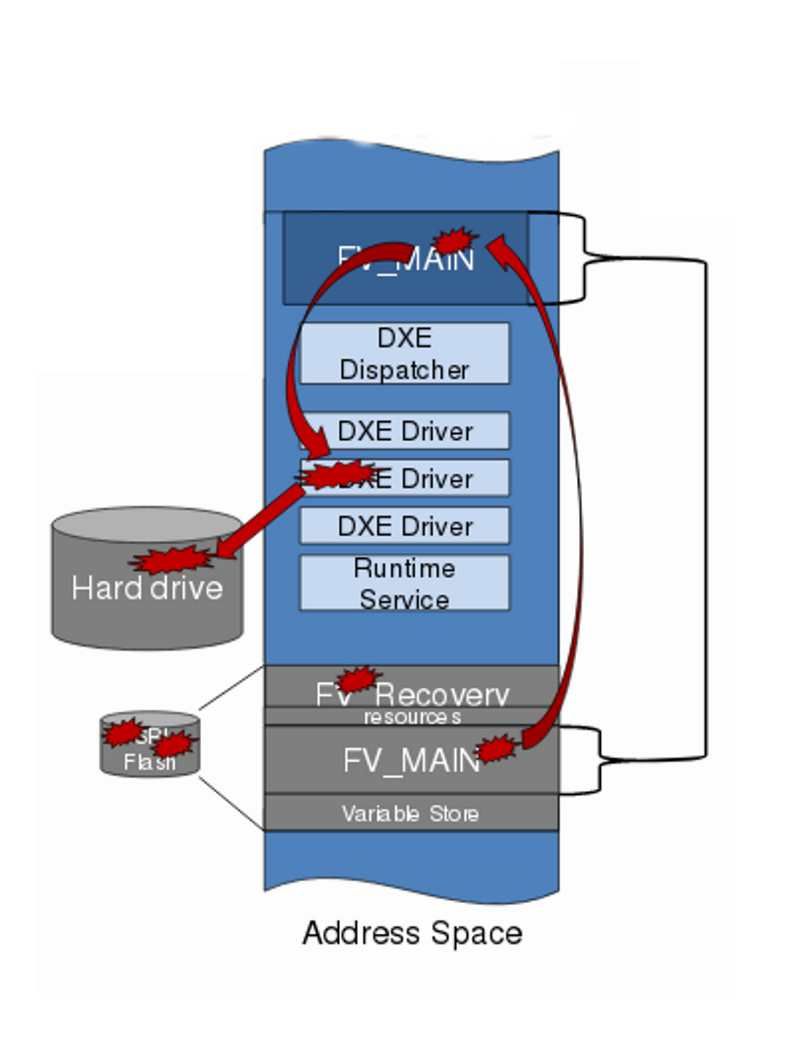
Refer to above diagram, we notice that the condition of Ring 2 will be depends on operation mode. So, if virtualization assist by hardware will let Ring 2 and Ring 3 work together. As a result, an attacker with write access to flash can inject malware into the firmware.
Remark: Malware injected into the firmware flash regions is persistent and will run on every subsequent boot.
SPI Flash Exploit – Malicious DXE drivers can disable security settings and install malicious code into the OS.
Additional:
Refer to above information. When a computer was installed and switched on, the microchip altered the operating system’s core so it could accept modifications. The chip could also contact computers controlled by the attackers in search of further instructions and code.
But who is the culprit, no further indicator proof. Perhaps it can shift the blame onto someone else. If you do not mind to read the articles announced by Bloomberg once more. Please refer below:
https://www.bloomberg.com/news/features/2018-10-04/the-big-hack-how-china-used-a-tiny-chip-to-infiltrate-america-s-top-companies