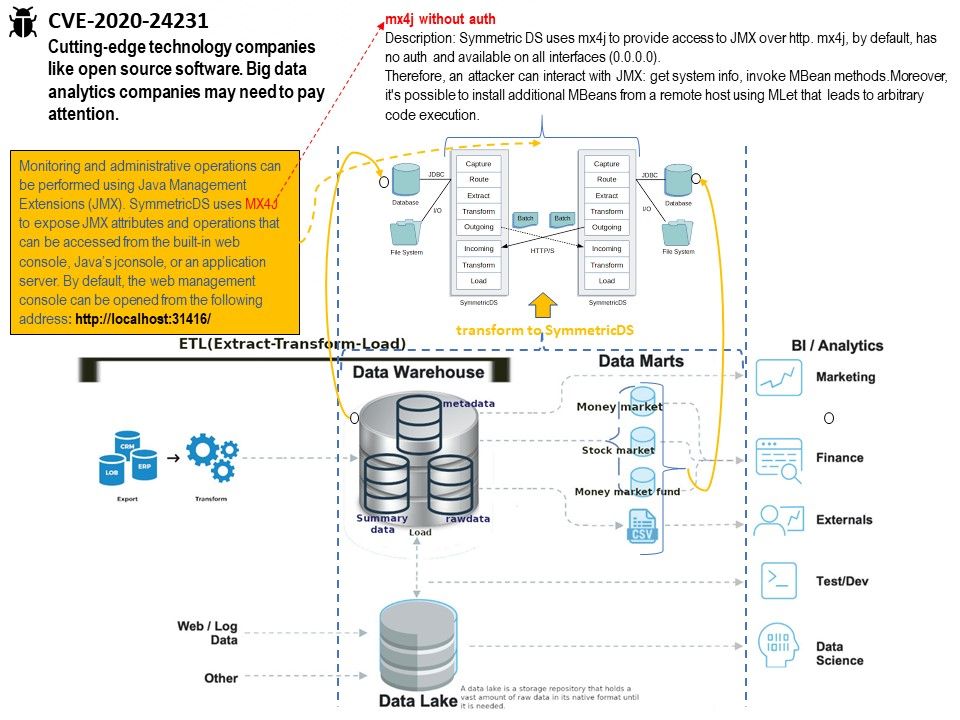
Preface: Cutting-edge technology companies like open source software. Big data analytics companies may need to pay attention.
Observation: According to our observation for advanced technology development firm. No matter they are small size or it is a enterprise firm. They do not mind to use the opensource software application. From business point of view, since they are the business unit and therefore they must have pay for license fees once vendor acknowledge. However, before their new services or products roll out to the market. The software developers are not hesitate to use open source software. And therefore the open source software vulnerability is the key factor they should be alert. Otherwise, the risk carry the impact to your services or products are unpredictable.
Techincal Background: For monitoring and administrative operations of SymmetricDS can be performed using Java Management Extensions (JMX). SymmetricDS uses MX4J to expose JMX attributes and operations that can be accessed from the built-in web console, Java’s jconsole, or an application server. By default, the web management console can be opened from the following address:
http://localhost:31416/
Vulnerability found on SymmetricDS: Symmetric DS uses mx4j to provide access to JMX over http. mx4j, by default, has no auth and available on all interfaces (0.0.0.0). Therefore, an attacker can interact with JMX: get system info, invoke MBean methods.Moreover, it’s possible to install additional MBeans from a remote host using MLet that leads to arbitrary code execution. For more details, please refer to attached picture.
Remedial Status: https://www.symmetricds.org/issues/view.php?id=4263