Preface: So far, it is difficult to detect the PendingIntent vulnerability from a tool.
Background: “PendingIntends” insecure usage can lead to server
BY exploiting vulnerable but benign applications that are in securely using PendingIntents. A malicious application without any permissions can perform many critical operations, such as sending text messages (SMS) to a premium number.
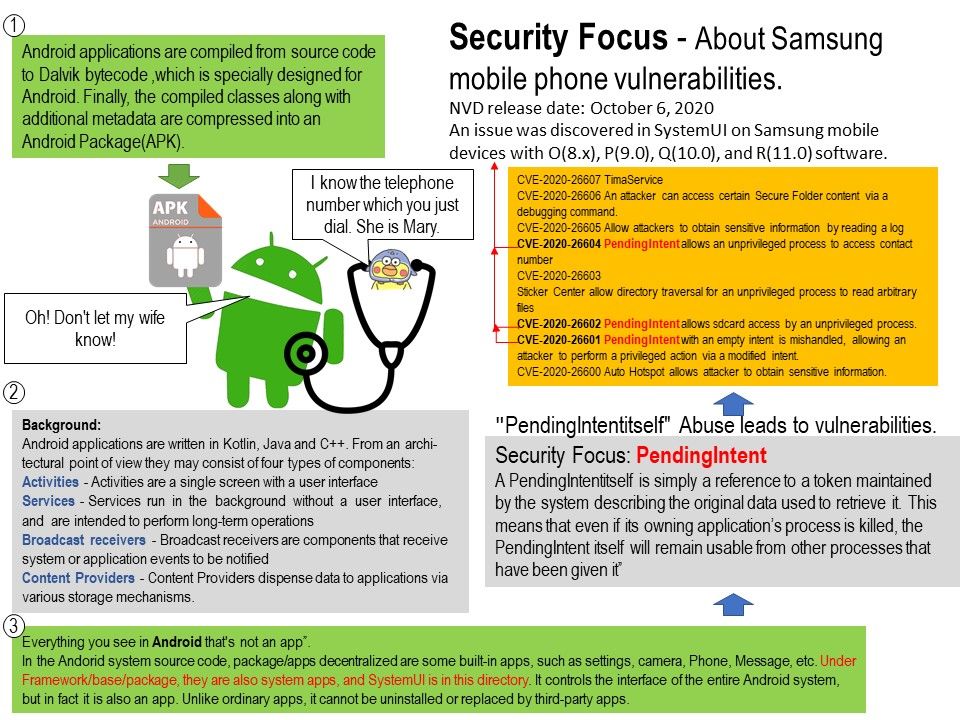
Known design weakness: A PendingIntentitself is simply a reference to a token maintained by the system describing the original data used to retrieve it. This means that even if its owning application’s process is killed, the PendingIntent itself will remain usable from other processes that have been given it.
Ref 1: An explicit intent defines a target component and thus is only delivered to the specified component.
Ref 2: Broadcast intent is broadcast to every registered component instead of only one.
Ref 3: PendingIntents – A PendingIntent is intended for another application to perform a certain action in the context of the sending application.
Vulnerability details – refer to below url:
https://nvd.nist.gov/vuln/detail/CVE-2020-26601