Preface: On a Linux system, chmod never changes the permissions of symbolic links; the chmod system call cannot change their permissions. This is not a problem since the permissions of symbolic links are never used. However, for each symbolic link listed on the command line, chmod changes the permissions of the pointed-to file.
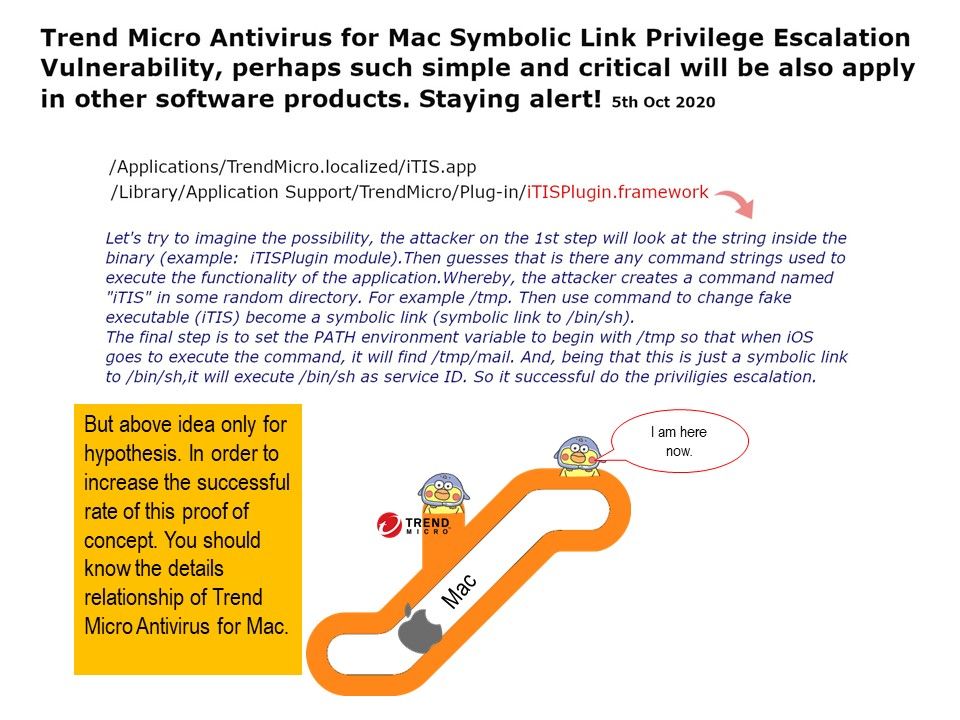
VULNERABILITY DETAILS: This vulnerability allows local attackers to escalate privileges on affected installations of Trend Micro Antivirus for Mac. The specific flaw exists within the iTISPlugin module. By creating a symbolic link, an attacker can abuse the product to loosen permissions on a local file. An attacker can leverage this vulnerability to escalate privileges and execute code in the context of root.
Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-25776.
The risk rating of this flaw set to low in CVE database. However, do not contempt this low level rating of risk. And believe that in the computer software world, the similar of flaw will be appear everywhere. So, we must staying alert.
Mitigation: Install updates from vendor’s website.
Vulnerable software versions: Antivirus for Mac: 2019 (v9.x), 2020 (v10.x)