Preface: IKE phase 1 in the sense that an attacker can perform a denial of service.
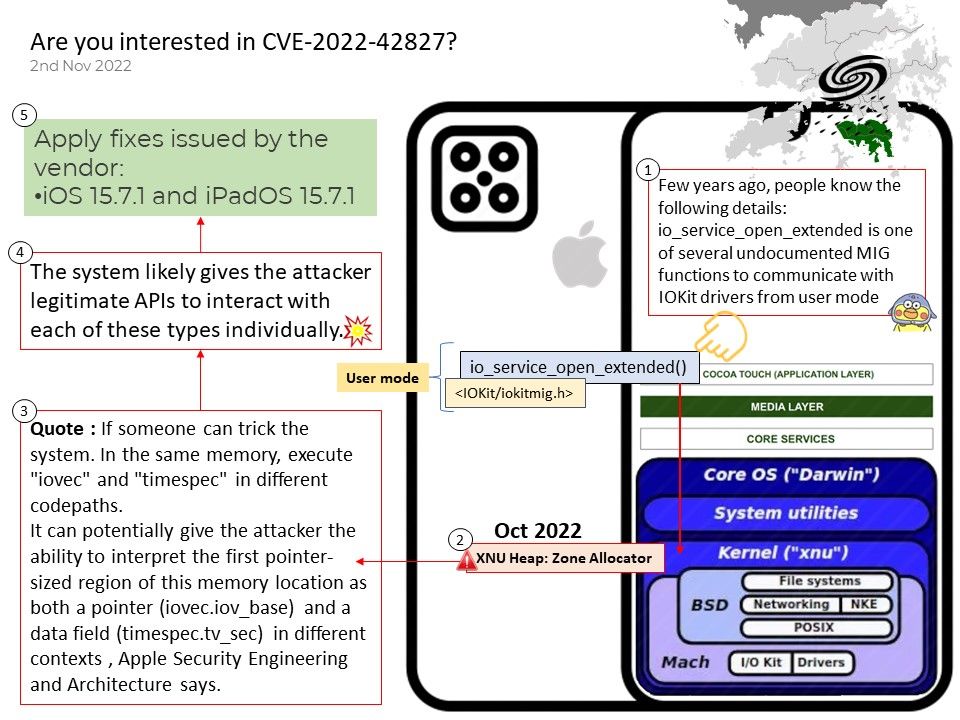
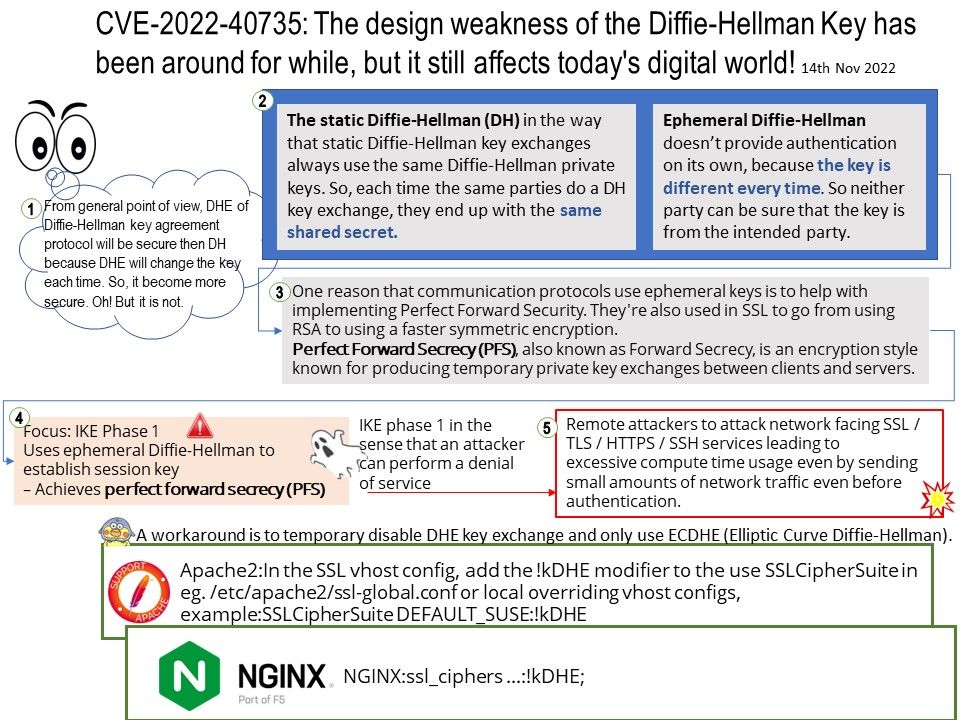
Background: Why use Ephemeral Diffie-Hellman? Ephemeral Diffie-Hellman (DHE in the context of TLS) differs from the static Diffie-Hellman (DH) in the way that static Diffie-Hellman key exchanges always use the same Diffie-Hellman private keys. So, each time the same parties do a DH key exchange, they end up with the same shared secret.
Ephemeral Diffie-Hellman doesn’t provide authentication on its own, because the key is different every time. So neither party can be sure that the key is from the intended party.
One reason that communication protocols use ephemeral keys is to help with implementing Perfect Forward Security. They’re also used in SSL to go from using RSA to using a faster symmetric encryption.
Perfect Forward Secrecy (PFS), also known as Forward Secrecy, is an encryption style known for producing temporary private key exchanges between clients and servers.
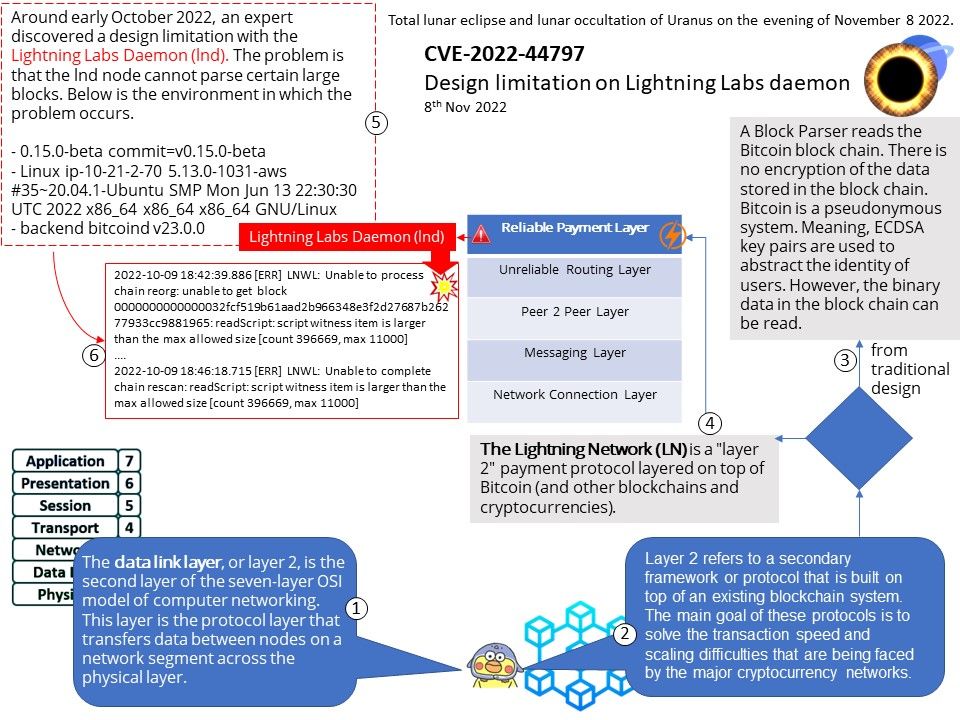
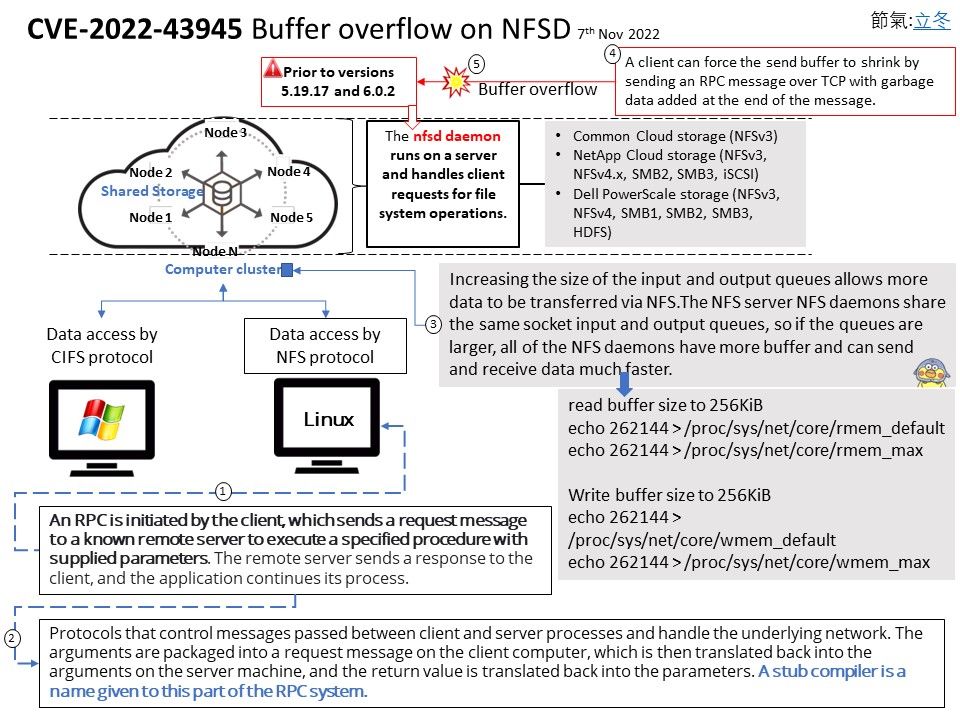
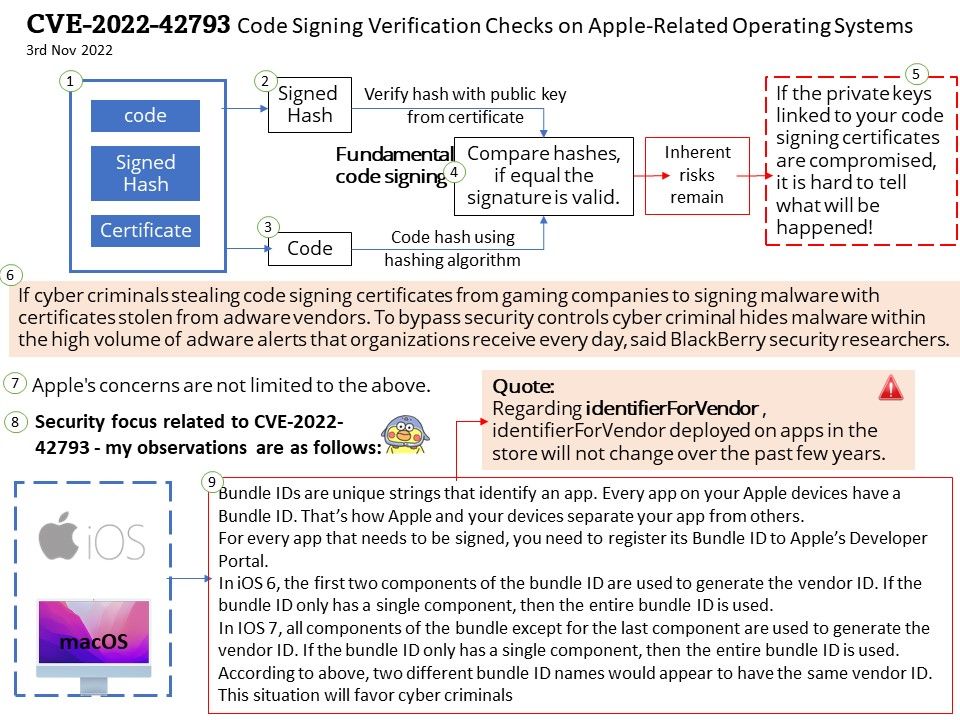
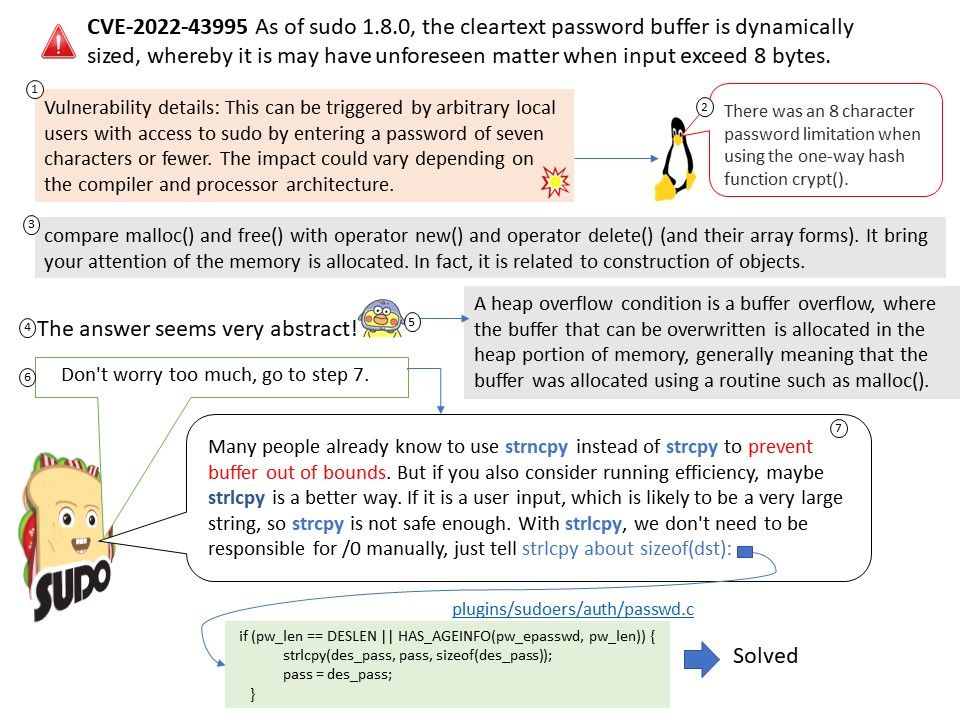
Vulnerability details: Using long exponents in the Diffie-Hellman Key Agreement Protocol allows remote attackers (from the client side) to trigger unnecessarily expensive server-side DHE modular-exponentiation calculations.
An attacker may cause asymmetric resource consumption with any common client application which uses a DHE implementation that applies short exponents. The attack may be more disruptive in cases where a client sends arbitrary numbers that are actually not DH public keys (aka the D(HE)ater attack) or can require a server to select its largest supported key size. The basic attack scenario is that the client must claim that it can only communicate with DHE, and the server must be configured to allow DHE. This can affect TLS, SSH, and IKE.
Workaround: A workaround is to temporary disable DHE key exchange and only use ECDHE (Elliptic Curve Diffie-Hellman), in SSL / TLS / HTTPS using network services.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-40735