Preface: If the supplier does not provide details. It’s hard to avoid that it’s not the exact answer.
Abuse code signing
-key compromise
-use of revoked or expired certificates
-code errors
-Systems compromise
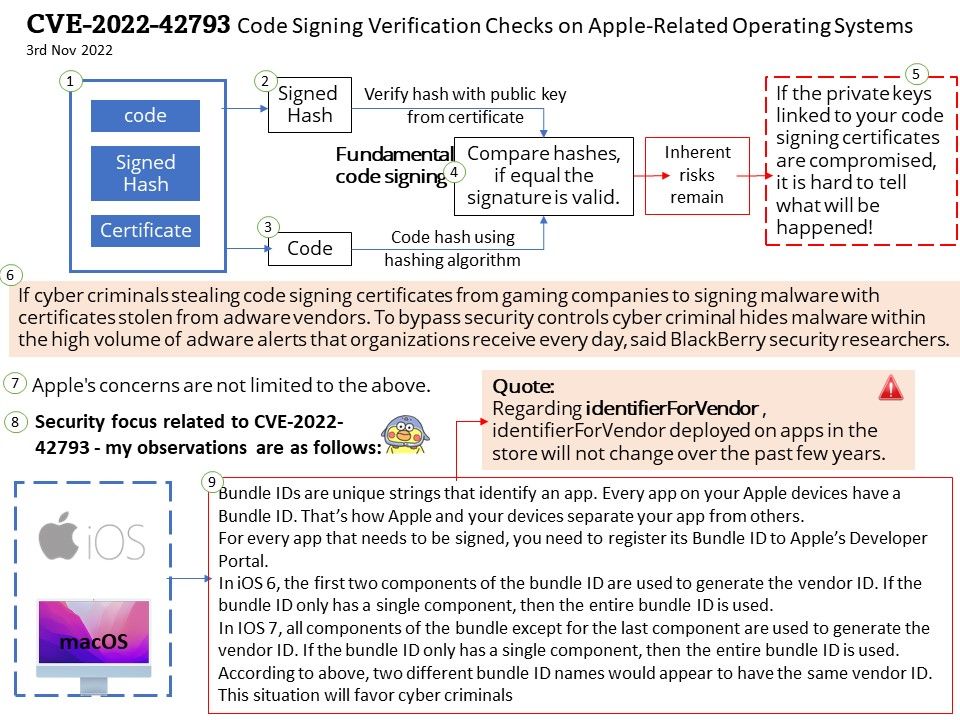
Background: If you’re developing apps for iOS, you need to sign your builds in order to send them to the App Store. However, iOS code signing can be challenging for many. Code Signing is a way for iOS devices to know that the app to be install on the device is from a known source. There are 3 key components in code signing:
1) Certificates
2) Bundle IDs
3) Provisioning Profiles
Bundle IDs are unique strings that identify an app. Every app on your Apple devices have a Bundle ID. That’s how Apple and your devices separate your app from others.
For every app that needs to be signed, you need to register its Bundle ID to Apple’s Developer Portal.
In iOS 6, the first two components of the bundle ID are used to generate the vendor ID. If the bundle ID only has a single component, then the entire bundle ID is used.
In IOS 7, all components of the bundle except for the last component are used to generate the vendor ID. If the bundle ID only has a single component, then the entire bundle ID is used.
According to above, two different bundle ID names would appear to have the same vendor ID. This situation will favor cyber criminals, please refer to point no.6 shown on diagram.
Vulnerability details: An issue in code signature validation was addressed with improved checks. This issue is fixed in macOS Big Sur 11.7, macOS Ventura 13, iOS 16, iOS 15.7 and iPadOS 15.7, macOS Monterey 12.6. An app may be able to bypass code signing checks.
Please refer to the link for details – https://developer.apple.com/documentation/uikit/uidevice/1620059-identifierforvendor