Preface: HTTP request smuggling exploits the inconsistency in parsing non-RFC-compliant HTTP requests via two HTTP devices (backend server and afront-end proxy). When attacker successful inject a malicious HTTP request into the web server, bypassing internal security controls. This can allow the attacker to:
- Gain access to protected resources, such as admin consoles
- Gain access to sensitive data
- Hijack sessions of web users
- Launch cross-site scripting (XSS) attacks without requiring any action from the user
- Perform credential hijacking
Background: RDP Proxy is capable providing RDP features. Users can access the remote desktops through the Citrix Gateway appliance.The design consists of the following:
- Deployment through clientless VPN: In this mode the RDP links are published on the Gateway home page or portal, as bookmarks, through the add vpn url configuration or through an external portal. The user can click these links to get access to the Remote Desktop.
- Deployment through ICA Proxy: In this mode a custom home page is configured on the Gateway VIP by using the wihome parameter.This home page can be customized with the list of Remote desktop resources that the user is allowed to access. This custom page can be hosted on Citrix ADC, or if external, it can be an iFrame in the existing Gateway portal page.
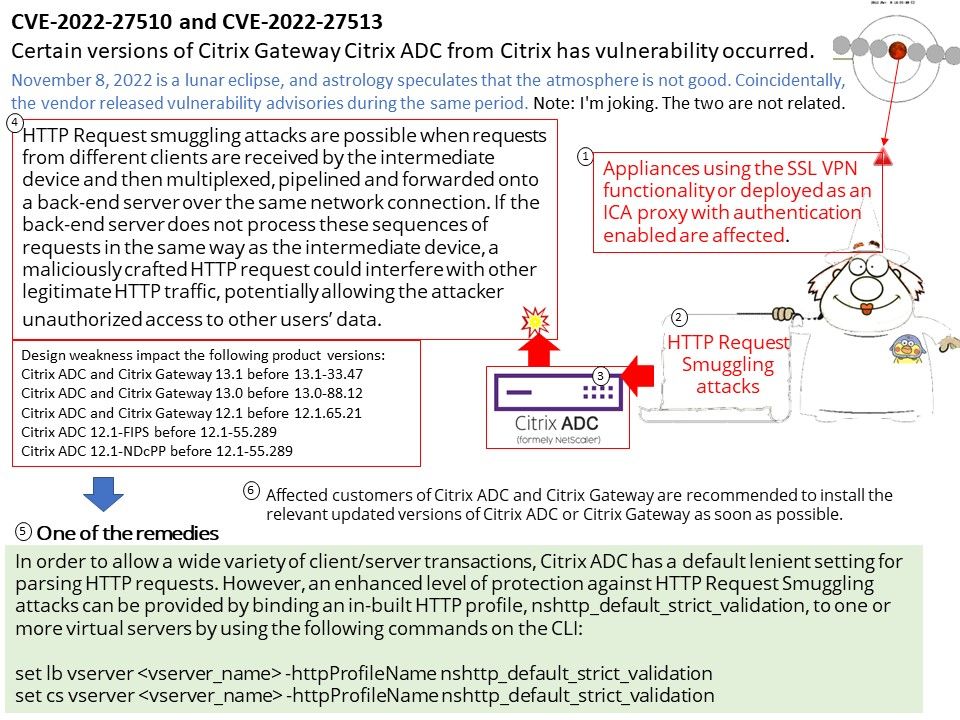
Affected customers of Citrix ADC and Citrix Gateway are recommended to install the relevant updated versions of Citrix ADC or Citrix Gateway as soon as possible.Design weakness impact the following product versions:
- Citrix ADC and Citrix Gateway 13.1 before 13.1-33.47
- Citrix ADC and Citrix Gateway 13.0 before 13.0-88.12
- Citrix ADC and Citrix Gateway 12.1 before 12.1.65.21
- Citrix ADC 12.1-FIPS before 12.1-55.289
- Citrix ADC 12.1-NDcPP before 12.1-55.289
Reference: The following are possible ways to mitigate the vulnerability (HTTP Request Smuggling Vulnerability)
- Ensuring that front-end and back-end servers only communicate using the HTTP/2 protocol can prevent most variants of this attack.
- Interpret HTTP headers consistently on front-end and back-end servers.
Official announcement: Please refer to the link for details – https://support.citrix.com/article/CTX463706/citrix-gateway-and-citrix-adc-security-bulletin-for-cve202227510-cve202227513-and-cve202227516