Preface: About 4 years ago, it was a hot topic for enterprise companies to develop the Hyperledger system framework for their business operations.
Multiple industries are willing to develop or undergo digital transformation. It includes huge fund investment companies, insurance companies and banking environments. The blockchain system architecture is the ancestor of Hyperledger. But cryptocurrencies have concerns about potential economic risks in the countries where the financial world belongs.
So it drawn down the development force of this technology. If National Vulnerability Database not alert Hyperledger Fabric 2.3 have bug last week. I think it will lost in my mind.
In fact, the Japanese financial industry was the first to develop and integrate Hyperledger Fabric into their business. In addition, the logistics industry is also involved in this advanced distributed development technology platform. Because their business operation keen to enhance fault tolerance level and high system resilience comparing to traditional design. Perhaps an unintended vulnerability factor gave the technology momentum. It keeps running and doesn’t stop.
Background: What is a Hyperledger channel?
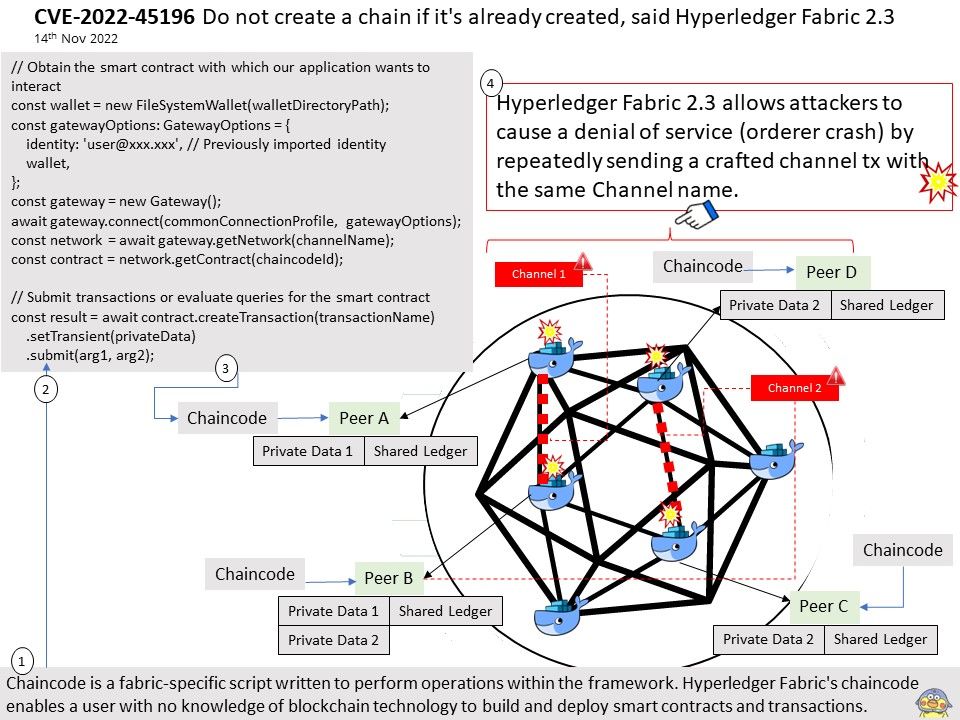
A Hyperledger Fabric channel is a private “subnet” of communication between two or more specific network members, for the purpose of conducting private and confidential transactions.
Chaincode is a fabric-specific script written to perform operations within the framework. Hyperledger Fabric’s chaincode enables a user with no knowledge of blockchain technology to build and deploy smart contracts and transactions.
Vulnerability details: Hyperledger Fabric 2.3 allows attackers to cause a denial of service (orderer crash) by repeatedly sending a crafted channel tx with the same Channel name. NOTE: the official Fabric with Raft prevents exploitation via a locking mechanism and a check for names that already exist.Raft (recommended) New as of v1. 4.1, Raft is a crash fault tolerant (CFT) ordering service based on an implementation of Raft protocol in etcd .Raft is a protocol with which a cluster of nodes can maintain a replicated state machine. The state machine is kept in sync through the use of a replicated log.
Perhaps Raft will be resolve this matter. However…..
Raft is a well-known and widely used distributed consensus algorithm, but as it has a built-in purpose of comprehensibility, it is always compromised in terms of performance as a trade-off.
For example: The Raft protocol is implemented based on the state machine of log replication. However, in actual systems, the log could not allow unlimited growth. As time increases, the continuous growth of logs will take up more log transmission overhead, as well as more recovery time for node downtime.
Suggestion: Patch (go to Hyperledger Fabric 2.4). In order to avoid such vulnerability. Hyperledger Fabric 2.4 calculate package ID of a packaged chaincode.
Official announcement: Please refer to the link for details – https://github.com/hyperledger/fabric/pull/2934