Preface: In Kernel mode, the executing code has complete and unrestricted access to the underlying hardware. It can execute any CPU instruction and reference any memory address. Kernel mode is generally reserved for the lowest-level, most trusted functions of the operating system.
Background: NVIDIA vGPU software enables multiple virtual machines (VMs) to have simultaneous, direct access to a single physical GPU, using the same NVIDIA graphics drivers that are deployed on non-virtualized operating systems.
NVIDIA Virtual GPU (vGPU) enables multiple virtual machines (VMs) to have simultaneous, direct access to a single physical GPU, using the same NVIDIA graphics drivers that are deployed on non-virtualized operating systems. By doing this, NVIDIA vGPU provides VMs with unparalleled graphics performance, compute performance, and application compatibility, together with the cost-effectiveness and scalability brought about by sharing a GPU among multiple workloads.
Vulnerability details: NVIDIA GPU Display Driver for Windows and Linux contains a vulnerability in the kernel mode layer, where a local user with basic capabilities can cause a null-pointer dereference, which may lead to denial of service.
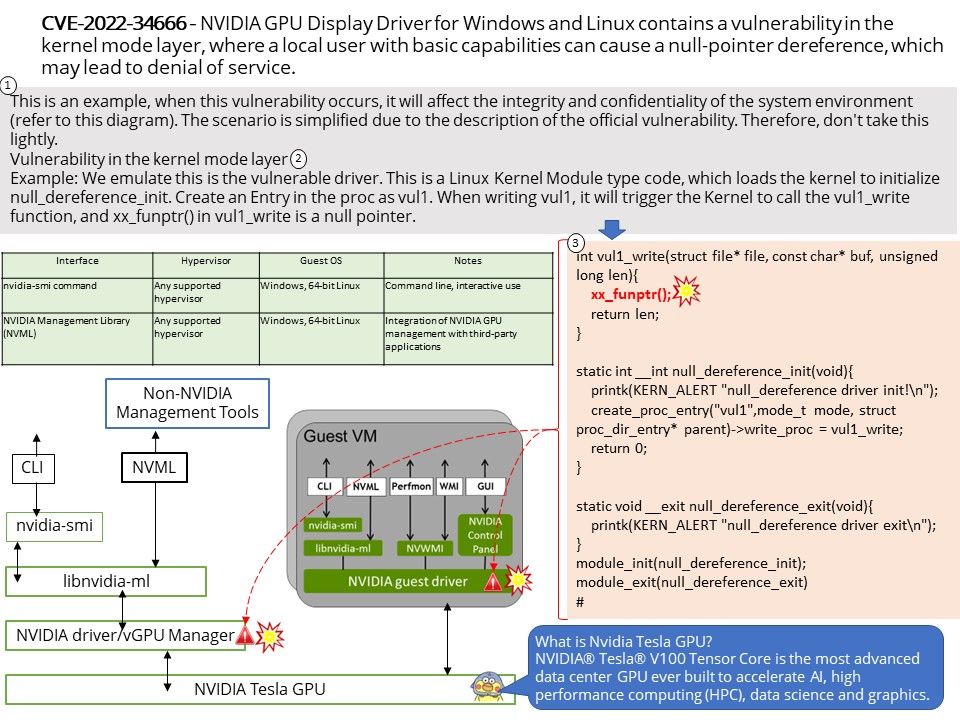
When this vulnerability occurs, it will affect the integrity and confidentiality of the system environment (refer to this diagram). The scenario is simplified due to the description of the official vulnerability.But do not contempt this matter.
Impact software products:
- vGPU software (Virtual GPU Manager) Citrix Hypervisor,VMware vSphere and Red Hat Enterprise Linux KVM
- vGPU software (guest driver) Linux
- vGPU software (guest driver) Windows
Official announcement: Please refer to the link for details – https://nvidia.custhelp.com/app/answers/detail/a_id/5383