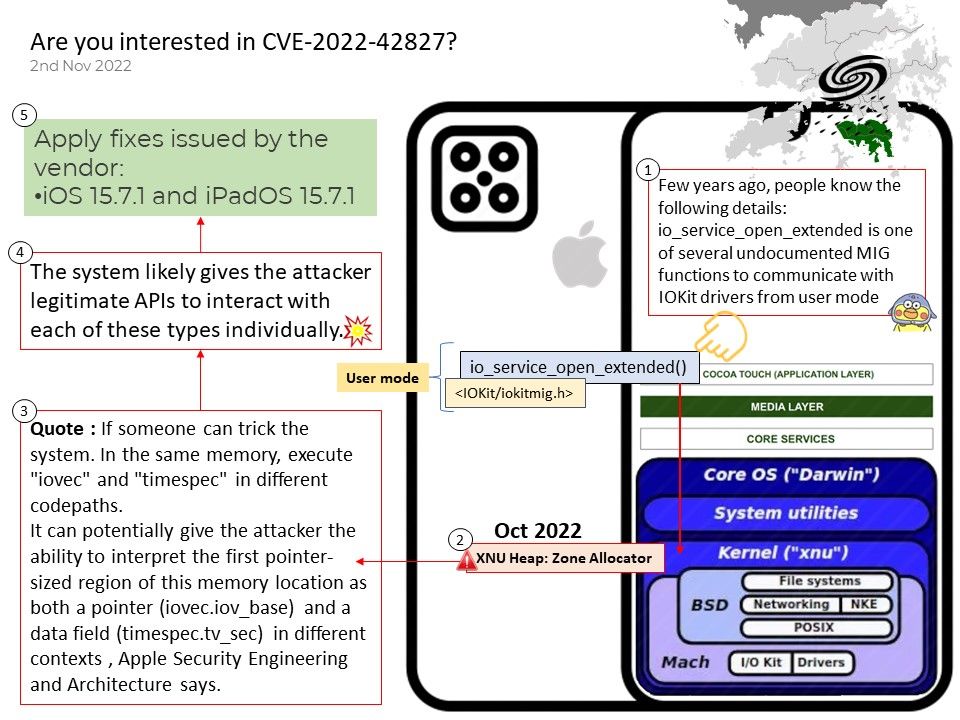
Preface: Few years ago, people know the following details:
io_service_open_extended is one of several undocumented MIG functions to communicate with IOKit drivers from user mode. This approach provides an opportunity for an attacker to perform kernel exploitation. Code writing in C-like languages can accidentally affect memory safety.
Background: Memory Tagging Extension (MTE) is designed to provide robustness against attacks attempting to subvert code processing malicious, attacker-provided, data. It does not address algorithmic vulnerabilities or malicious software. The core principle of type isolation is that after any particular address has been used for a given “type” of object, only objects of that type can ever exist at that address for the lifetime of the program.
Memory can broadly be categorized either as “control” or as “data.” Control is what lets a program structure and organize data. It includes things such as pointers, reference counts, lengths, and typing information like union tags. Almost everything else is data.
Apple also rarely shared the core technology of XNU, mainly the security upgrade of XNU memory, the first topic is the memory allocator kalloc_type.
Vulnerability details: A vulnerability classified as critical has been found in Apple iOS and iPadOS (Smartphone Operating System) (version unknown). Affected is an unknown function of the component Kernel. The manipulation with an unknown input leads to a memory corruption vulnerability. CWE is classifying the issue as CWE-787. The software writes data past the end, or before the beginning, of the intended buffer. This is going to have an impact on confidentiality, integrity, and availability.
Affected: Versions prior to iOS 15.7.1 and iPadOS 15.7.1
Solutions: Apply fixes issued by the vendor: iOS 15.7.1 and iPadOS 15.7.1
Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-42827