Preface: Is cloud computing in demand in 2022? Their latest forecast predicts the spending on public cloud services to jump from $257.5 billion in 2020 to $304.9 billion in 2022 as cloud services play a central role in helping businesses recover from the onslaughts of the pandemic.
The current version of NFS is also called NFS v4 but was implemented through RFC 3530. In 2003, it was published. Since then, compared to early NFS v4, NFS v4 has improved a lot in terms of optional features, such as protection, caching, locking, and message communication performance. While NFS has PC capabilities, it has often been treated as a file-oriented protocol rather than the PC environment for UNIX and Linux operating systems. Microsoft Azure, a popular public cloud service, offers Azure Files, a cloud-based distributed file which supports NFS 4.1 since September 2020, in the Azure Files premium tier only.
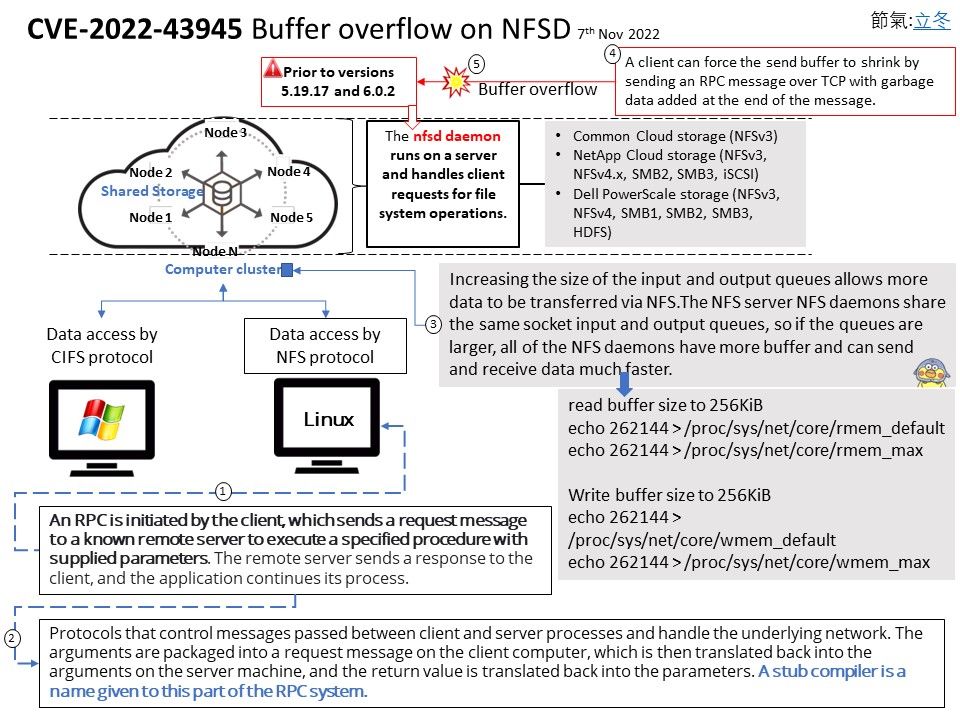
Background: NFS is an RPC-based protocol, with a client-server relationship between the machine having the filesystem to be distributed and the machine wanting access to that filesystem. Each version of the NFS RPC protocol contains several procedures. The basic procedures performed on an NFS server can be grouped into directory operations, file operations, link operations, and filesystem operations. The nfsd daemon runs on a server and handles client requests for file system operations. Each daemon handles one request at a time. Assign the maximum number of threads based on the load you expect the server to handle.
- NFS version 3 (NFSv3) supports safe asynchronous writes and is more robust at error handling than the previous NFSv2; it also supports 64-bit file sizes and offsets, allowing clients to access more than 2 GB of file data.
- NFS version 4 (NFSv4) works through firewalls and on the Internet, no longer requires an rpcbind service, supports Access Control Lists (ACLs), and utilizes stateful operations.
Vulnerability details:
CVE-2022-43945 – The Linux kernel NFSD implementation prior to versions 5.19.17 and 6.0.2 are vulnerable to buffer overflow. NFSD tracks the number of pages held by each NFSD thread by combining the receive and send buffers of a remote procedure call (RPC) into a single array of pages. A client can force the send buffer to shrink by sending an RPC message over TCP with garbage data added at the end of the message. The RPC message with garbage data is still correctly formed according to the specification and is passed forward to handlers. Vulnerable code in NFSD is not expecting the oversized request and writes beyond the allocated buffer space.
Cause: One notable set of fixes addresses a subtle buffer overflow issue that occurs if a small RPC Call message arrives in an oversized RPC record. This is only possible on a framed RPC transport such as TCP. Because NFSD shares the receive and send buffers in one set of pages, an oversized RPC record steals pages from the send buffer that will be used to construct the RPC Reply message. NFSD must not assume that a full-sized buffer is always available to it; otherwise, it will walk off the end of the send buffer while constructing its reply.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-43945