Preface: To cope with Industrial automation and control system. The technology difference in between IT and OT are small. Perhaps they are close. For cyber security protection matters, seems they are no any difference.
Product background: Formerly known as RSLinx® Enterprise, FactoryTalk® Linx is included with most FactoryTalk software and functions as the premier data server
to deliver information from Allen‑Bradley control products to the control system. While FactoryTalk Linx interfaces with PLC-5®, SLC™ 500 and Micro800™ controllers, it is optimized to communicate with Logix 5000™ controllers using EtherNet/IP.
This gives the fastest data rates and capacity possible, while minimizing the impact on your automation networks and control system operation.
FactoryTalk Linx delivers a solution from small applications running on a single computer with a single controller, to large distributed and
even redundant data server configurations communicating with large automation systems.
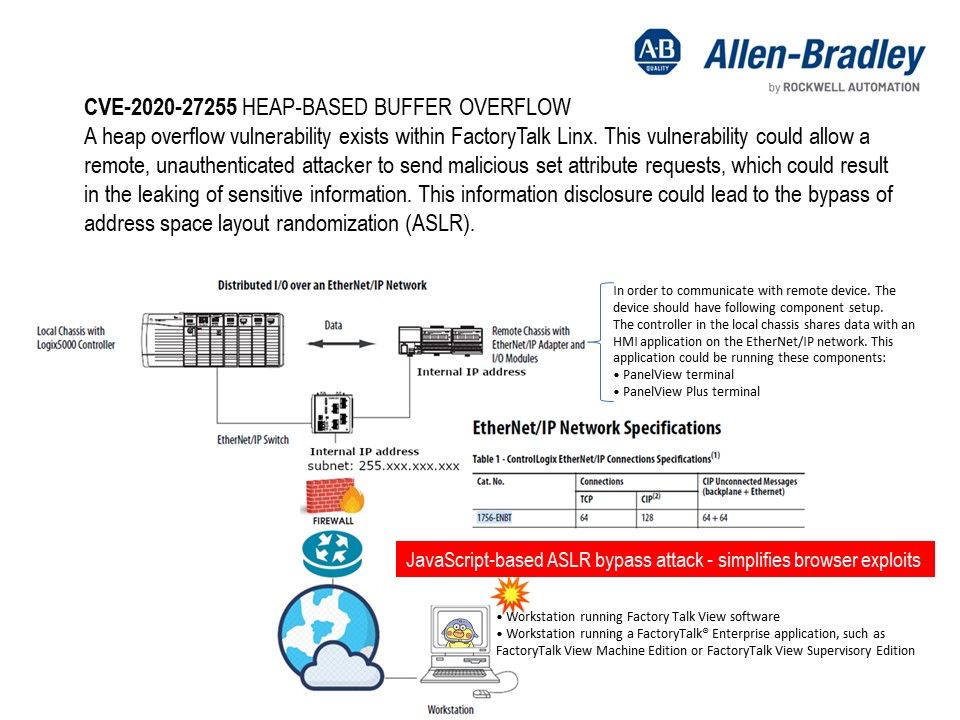
Vulnerability details: A heap overflow vulnerability exists within FactoryTalk Linx. This vulnerability could allow a remote, unauthenticated attacker to send malicious set attribute requests, which could result in the leaking of sensitive information. This information disclosure could lead to the bypass of address space layout randomization (ASLR).
Observation: Vendor do not explicitly disclose the facts of the vulnerability. But most likely the vulnerability cause by java script based ASLR bypass attack.
Vendor announcement and remedy: https://us-cert.cisa.gov/ics/advisories/icsa-20-329-01