Preface: Smart City look like a housekeeper. The sensor is his eye.But do you have question? He is a man or she is a woman.
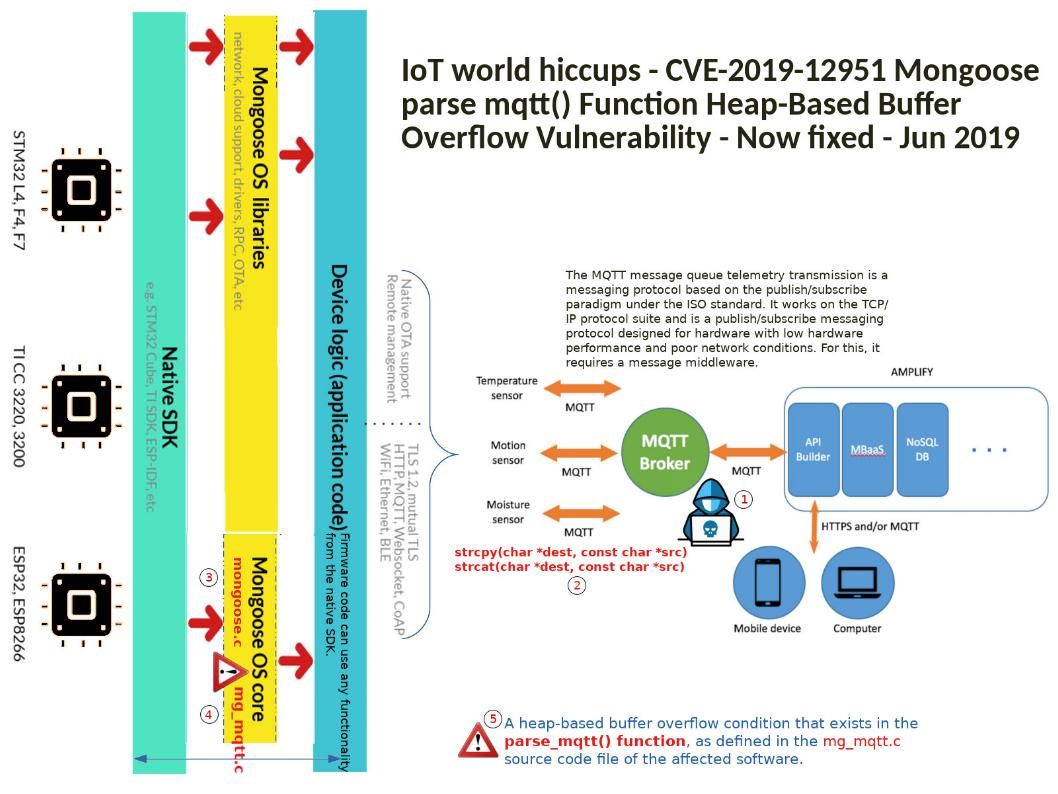
Background: Mongoose is a cross-platform embedded web server and networking library with functions including different protocol (TCP, HTTP, WebSocket, Server MQTT client and broker).
What is MQTT? MQTT is a simple messaging protocol, designed for constrained devices with low-bandwidth. It works on the TCP/IP protocol suite.
Vulnerability details: An issue was discovered in Mongoose before 6.15. The parse_mqtt() function in mg_mqtt.c has a critical heap-based buffer overflow.
Impact: It could allow an unauthenticated, remote attacker to execute arbitrary code or cause a denial of service (DoS) condition on a targeted system (see attached diagram).
Reference: Example of arbitrary code
strcpy(char *dest, const char *src) – May overflow the dest buffer
strcat(char *dest, const char *src) – May overflow the dest buffer
The vendor has released a bug fix – https://github.com/cesanta/mongoose/commit/b3e0f780c34cea88f057a62213c012aa88fe2deb