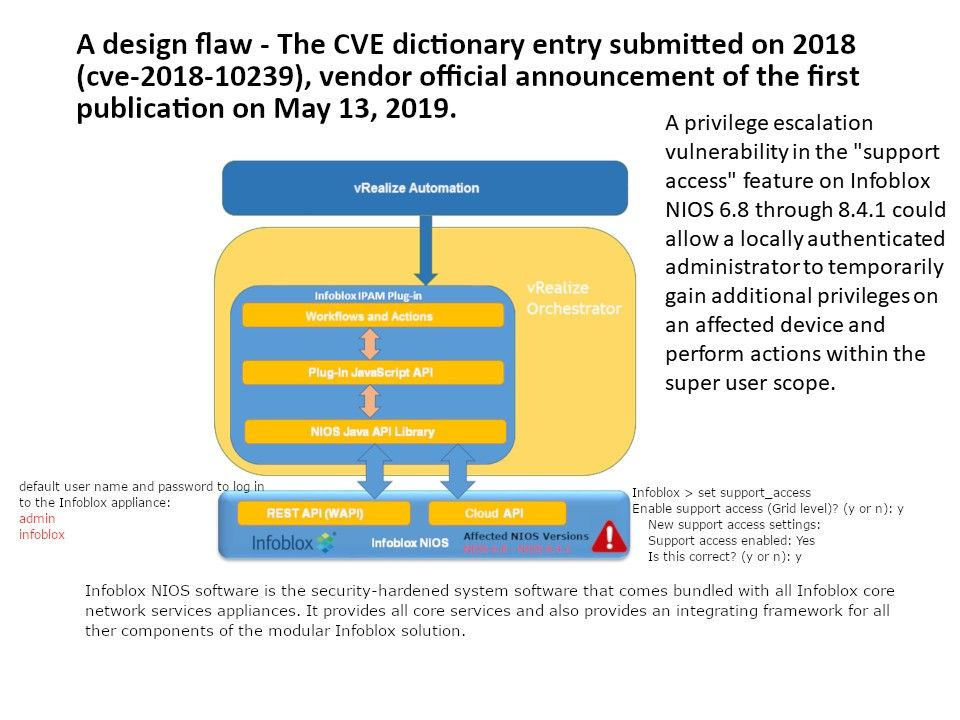
Preface: You can still find the default username and password on your computer today! Coincidentally, they share common characteristics. They have super user capabilities.
Synopsis: Infoblox delivers essential technology to enable customers to manage, control and optimize DNS, DHCP, IPAM .
Vulnerability Details: A privilege escalation vulnerability in the “support access” feature on Infoblox NIOS 6.8 through 8.4.1 could allow a locally authenticated administrator to temporarily gain additional privileges on an affected device and perform actions within the super user scope.
Enabling this feature allows Infoblox Support (Tier 3 access) to perform root level diagnostics on an appliance that is in severe distress. A special key is required to access the appliance at root level, and only Infoblox Support (Tier 3) can generate this key.
But do you think the following details need attention? Only superusers can access the CLI. To ensure security, access to the CLI is permitted through a direct console connection only. Note that activating the option Enable Remote Console Access in the Grid or Member Properties editor will result in a non-compliant system.
Use the following default user name and password to login.
admin
infoblox
Remark: Default password can be changed.
Remedy: Issue has been resolved in NIOS 8.4.2.