Preface:
Can we saying this? it is Google Adwords design flaw? It lure the threat actors go through this service to spread malware from Google search engine.
Quick note:
Saturn ransomware found this month (Feb 2018). It looks strange that attack victim only on physical machine instead of Virtual Machine. Why? Does the threat actor concern about VMware or HyperV have quick data recovery by Snap shot backup? Security expert found the following hints:
Saturn will execute the following commands to delete shadow volume copies, disable Windows startup repair, and to clear the Windows backup catalog.
cmd.exe /C vssadmin.exe delete shadows /all /quiet & wmic.exe shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet
Perhaps hacker understand that doing ransomware targeting home user will be easier. May be enpterprise firm or cloud services provider contains full scope of SIEM system. As such, forensic investigator can be tracing them. Or this is a prototype may be there is another round of attack later on.
Status updated – 19th Feb 2018
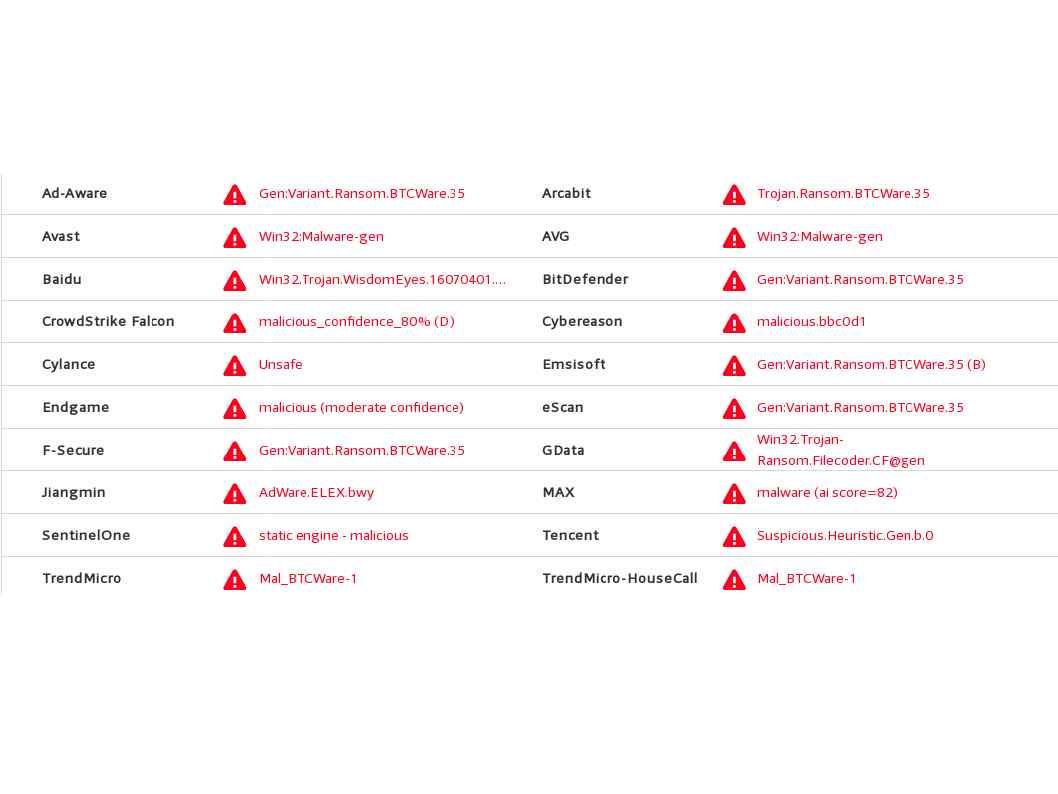
20 antivirus engines detected this ransomware. Hash shown as below:
b3040fe60ac44083ef54e0c5414135dcec3d8282f7e1662e03d24cc18e258a9c
Anyway IT world do not have key words so called permanent solution. In the mean time. The action we can execute is doing the remediation.
Step 1: Start PC in Safe Mode
Through the F8 key (for Windows 7/Vista)
- Once the computer is restarted (usually after you hear the first computer beep), continuously tap the F8 key in 1 second intervals. If successful, the Advanced Boot Options menu will appear.
- Use the arrow keys to select Safe Mode and press ENTER.
For windows 10
Use the “Shift + Restart” combination. Another way of getting into Safe Mode in Windows 10 is to use the Shift + Restart combination. Open the Start menu and click or tap on the Power button. Then, while keeping the Shift key pressed, click or tap on Restart.
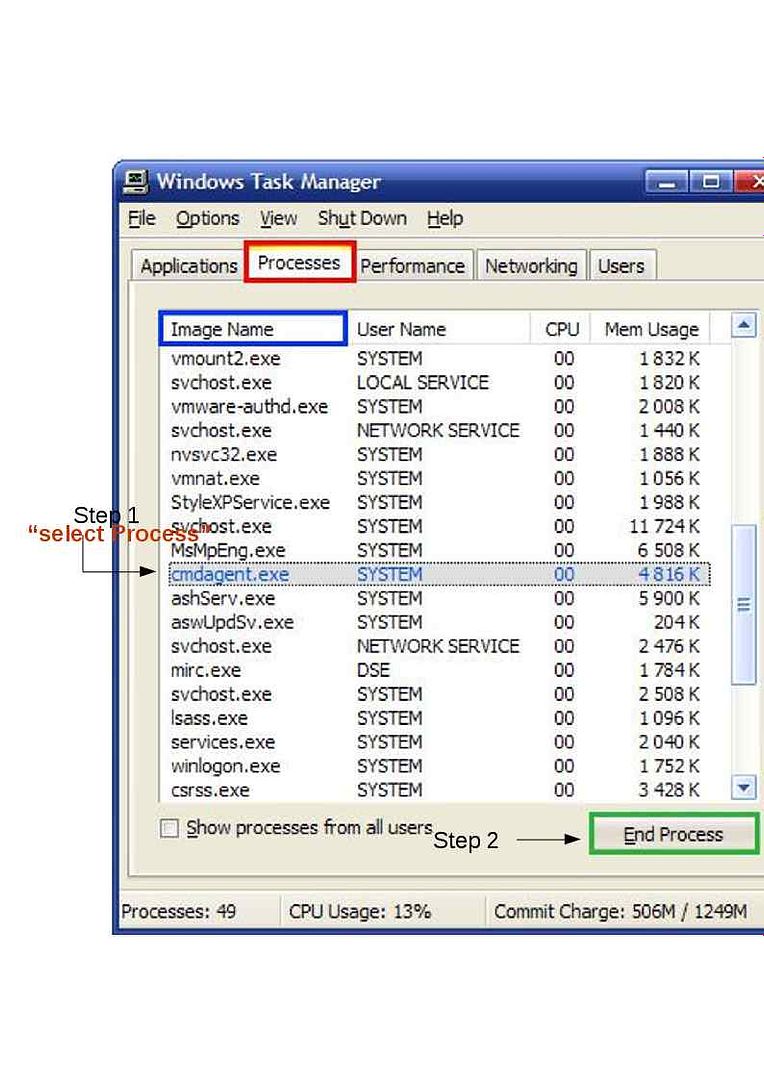
Step 2: Stop Saturn Processes From Windows Task Manager
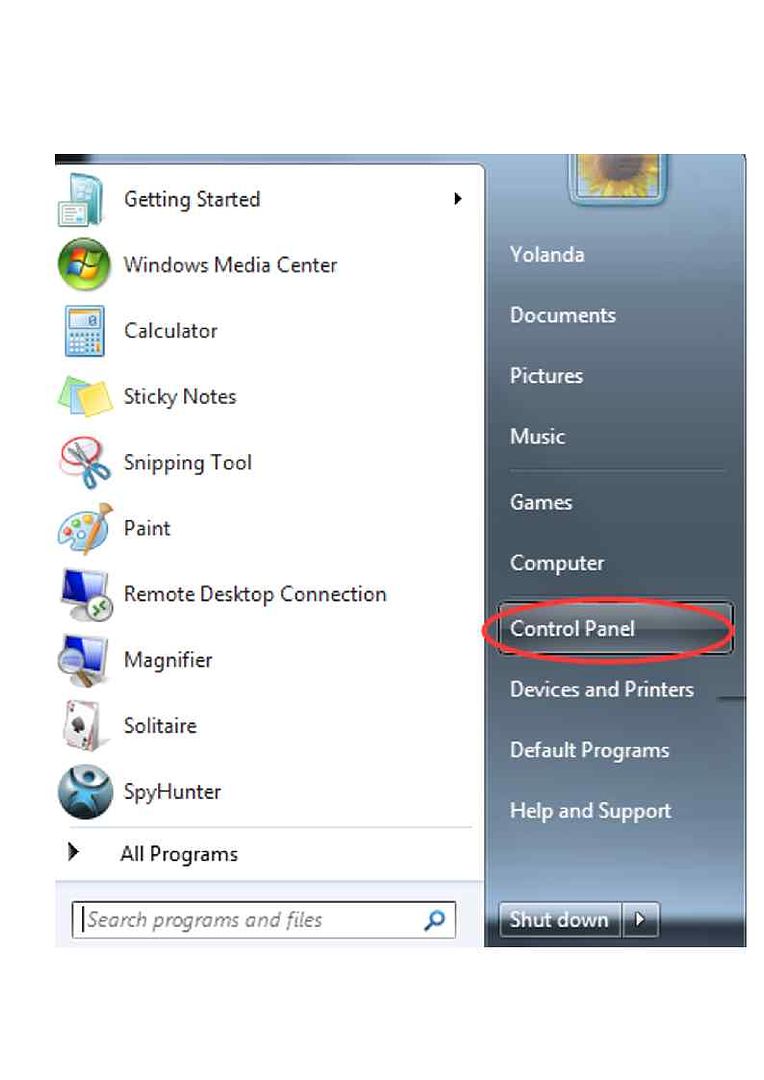
Step 3: Remove Saturn Ransomware from Control Panel
Procedure 1:
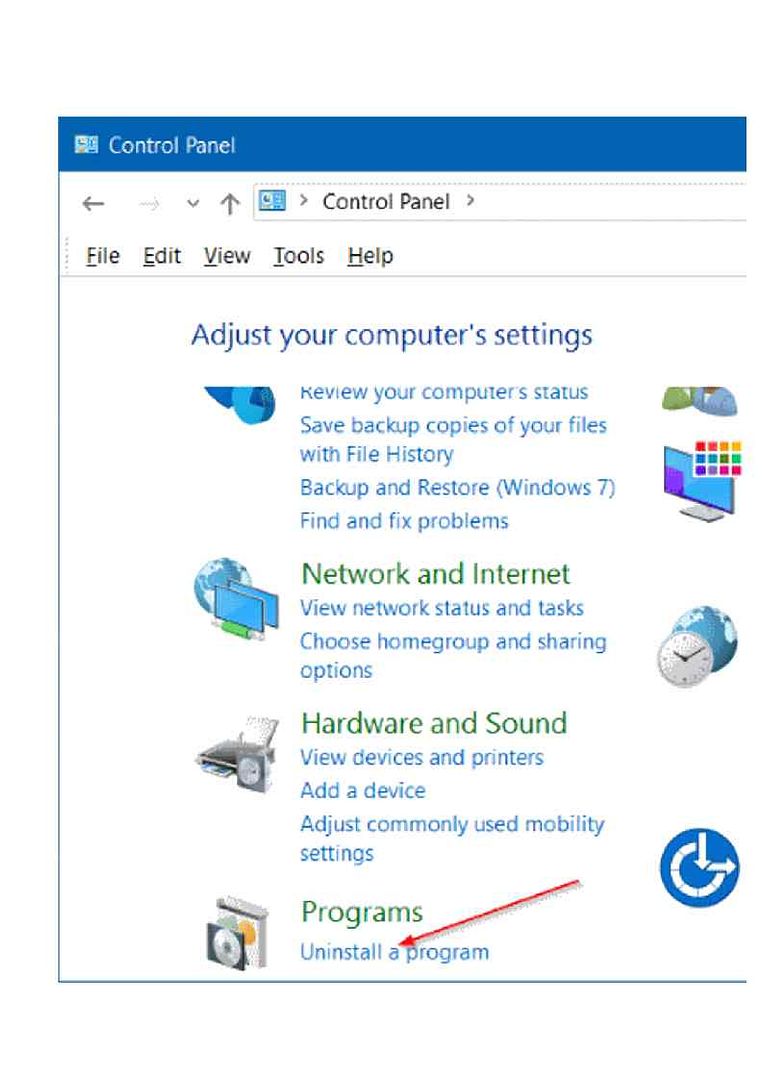
Procedure 2:
Procedure 3:
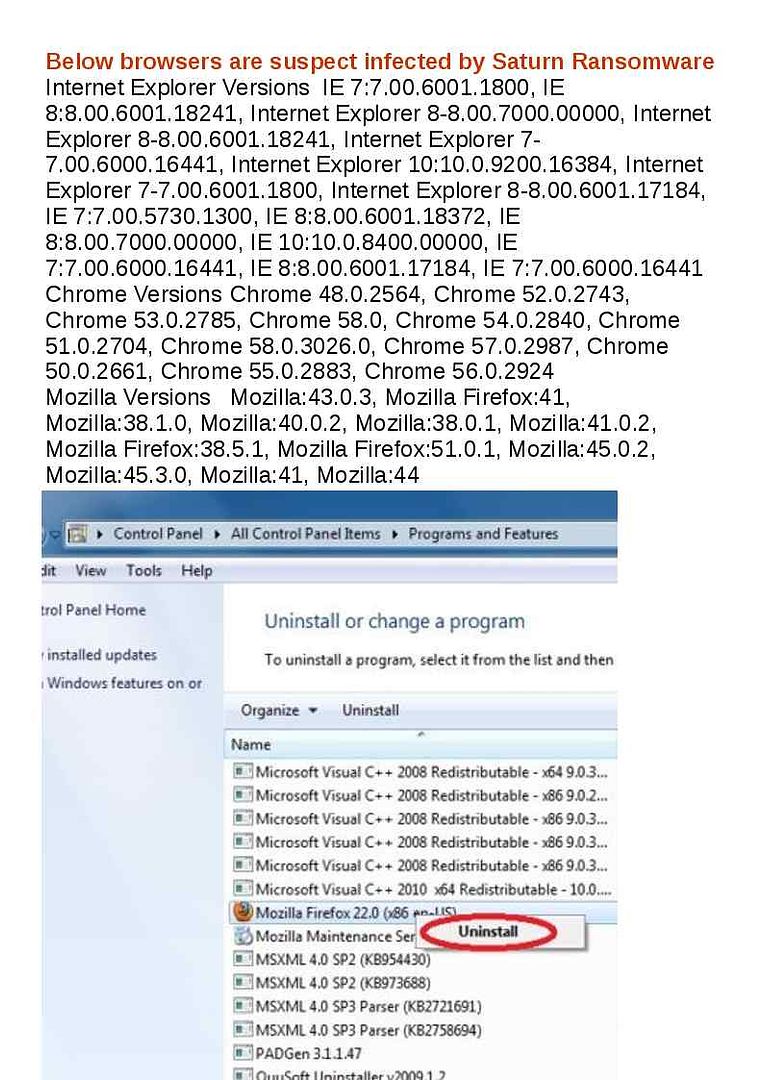
Main body of the Saturn Ransomware relies browser to work and hide himself in web browser. So we require to uninstall the web browser:
Remark: We are not allow to uninstall or delete Internet Explorer from Windows 7, 8 and 10 and therefore we are going to delete the additional web browser. Since Saturn ransomware relies on web browser for operation.
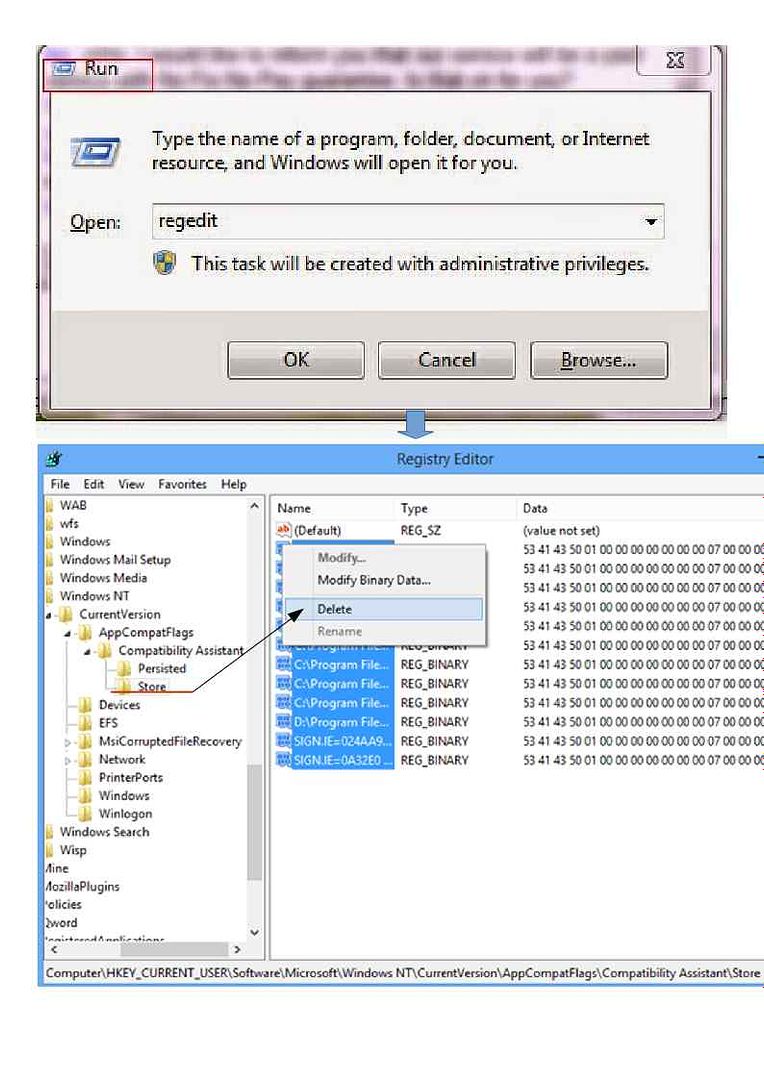
Step 4: remove Malicious Registry Entries Created by Saturn Ransomware
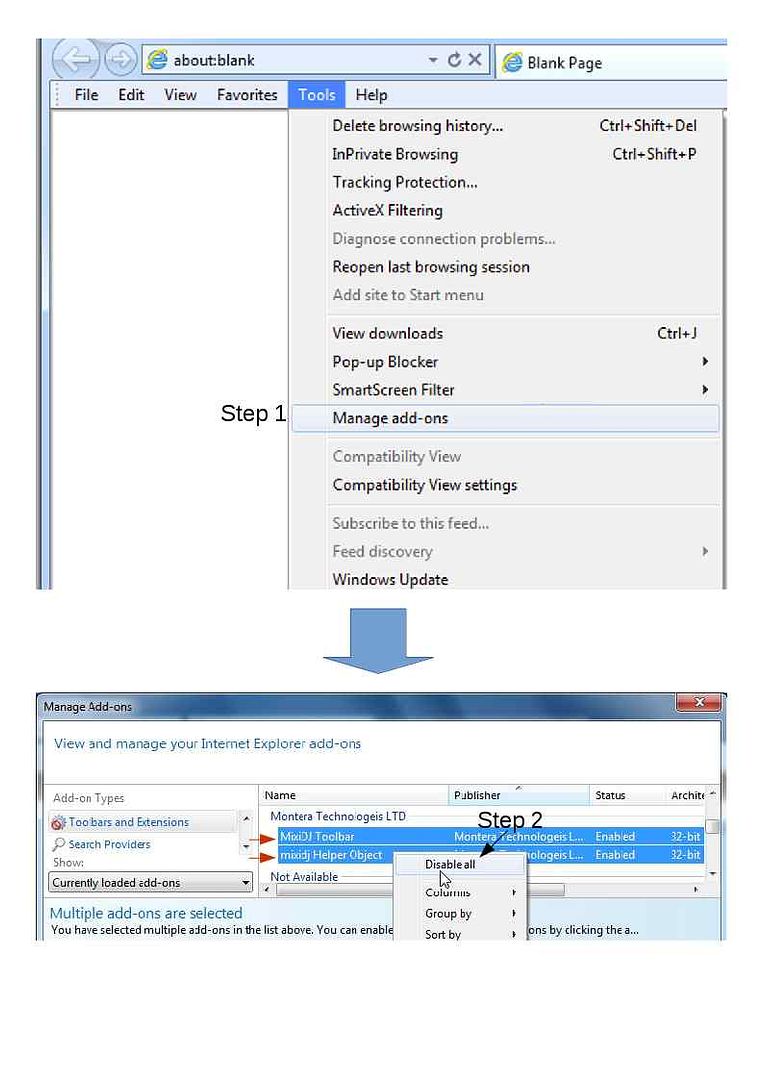
Step 5: Remove Saturn Ransomware From Infected Internet Explorer
Take Down Saturn Ransomware From Internet Explorer. Open IE and click on Gear Icon from right-top corner in order to open the Tools. Tap on Manage Add-ons option.
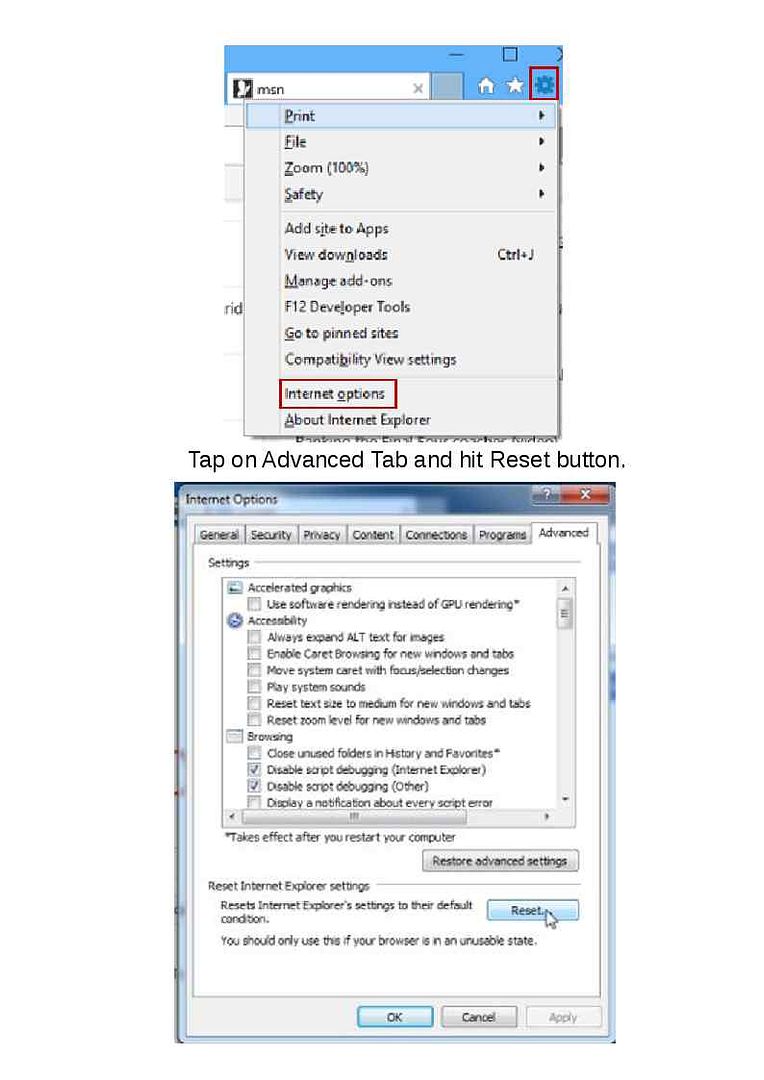
Step 6: Reset Internet Explorer Settings
Open IE and click on Tools menu and then select Internet options.
Step 7: Download decryption tool
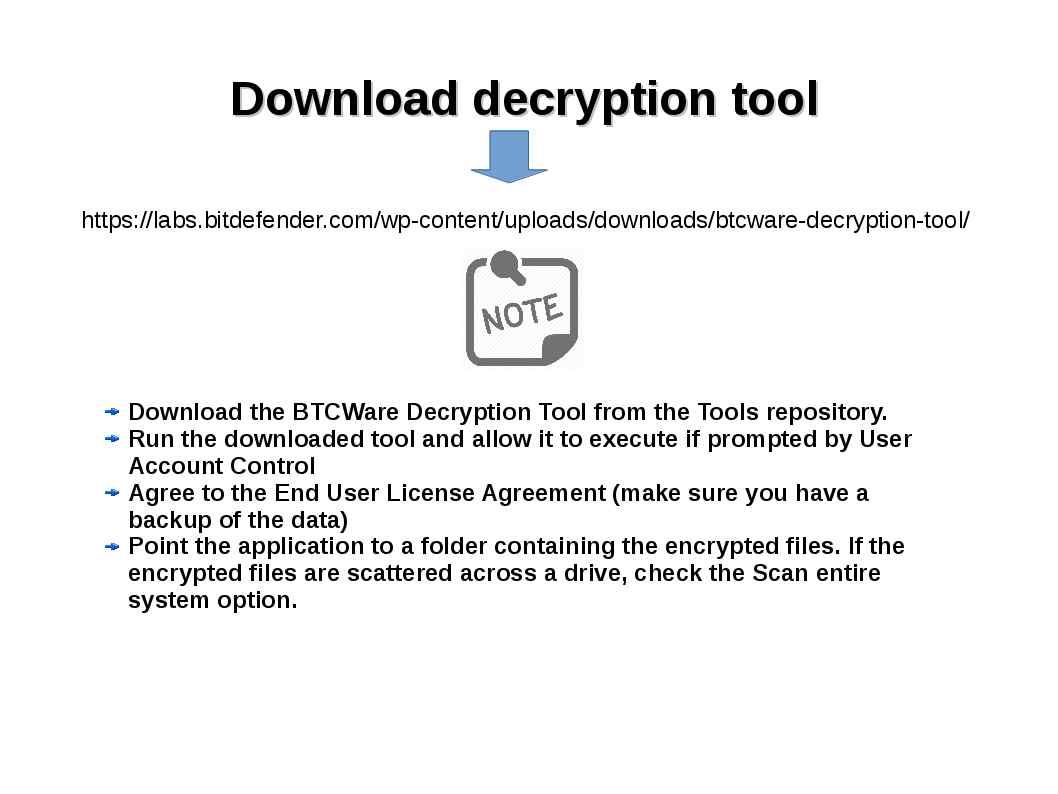
The decryption tool will not run if:
- It can’t find a valid ransom note
- It cannot find a valid encrypted file (i.e a file that is not corrupted)
- It can’t decrypt the User ID field in the ransom note
End, Thank you.
Additional comment: New ransomware nickname Saturn was born this month. This ransomware provides a hints to me that it is the 1st phase of attack. Or it is a prototype. Perhaps we seen cyber attack, virus, malware and ransomware daily. The cyber world added one more member of bad guy we could not surprised!