
Preface
Can you remember that Science fiction movies Godzilla. The sea monster dubbed Godzilla, his body empowered by nuclear radiation then become huge. However his target is attack the Tokai Nuclear Power Plant and feeding on the nuclear reactor. The Japanese government concluded that nuclear power was what attracted Godzilla.
The World in demand of electricity power
The electricity power generation scheme, like plants that burn coal, oil and natural gas, produce electricity by boiling water into steam. This steam then turns turbines to produce electricity. Nuclear power plants obtain the heat needed to produce steam through a physical process. Apart of environmental pollution and Harmful radiation. Nuclear power looks is the quick and dirty way to resolve the natural resources supply limitation in the earth.
Example: Water energy reactor located in Ukraine
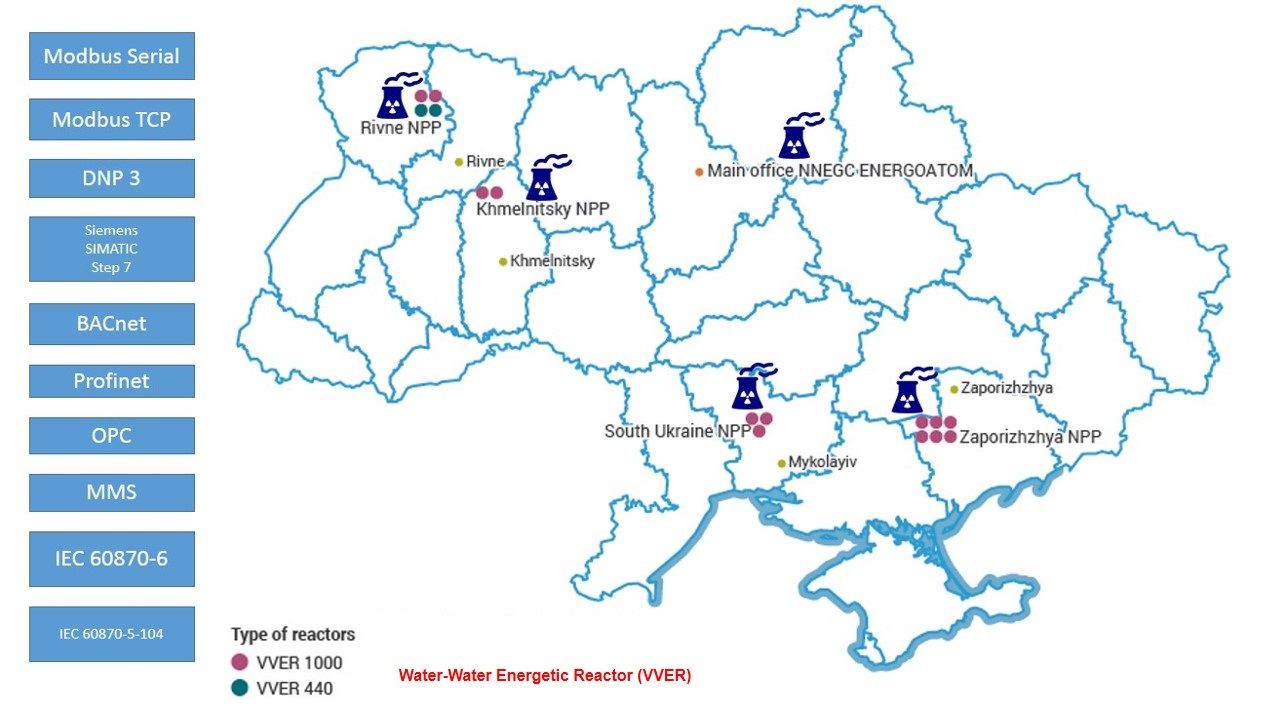
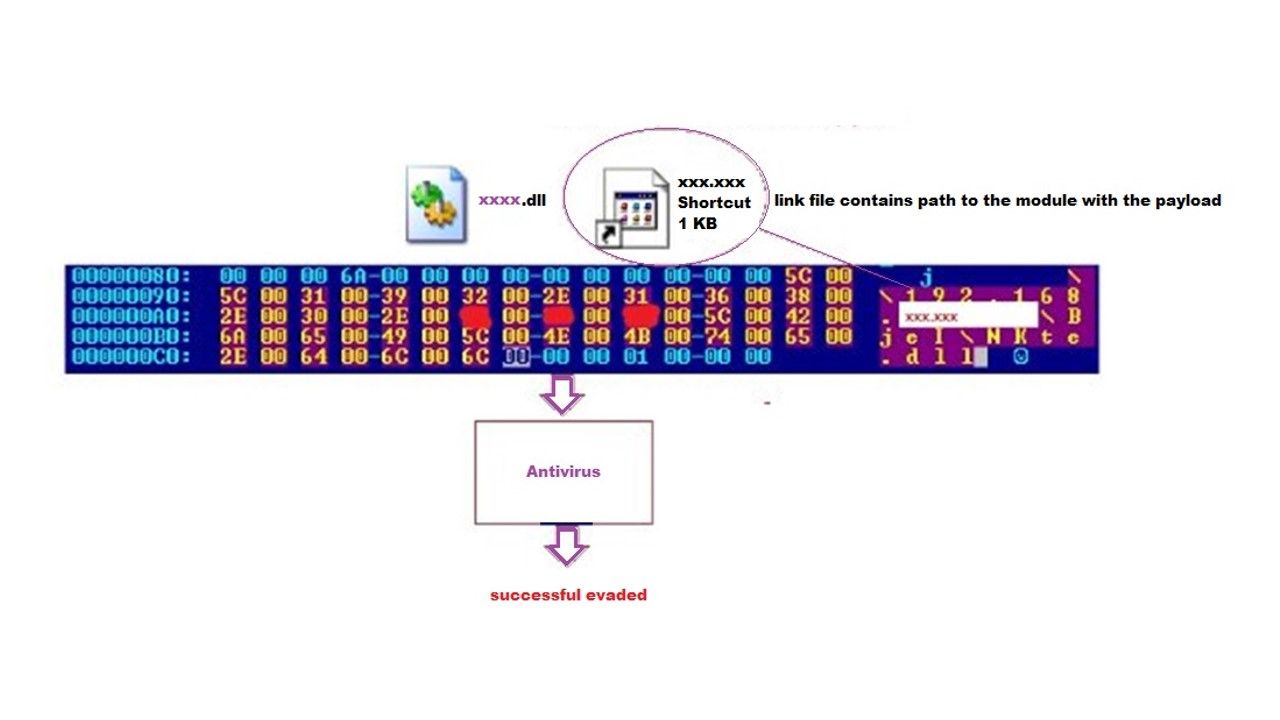
Stuxnet malware ages evolute the function to the new generation of malware
Cyber attacker follow Stuxnet objective, the group re-engineering a powerful DDOS tool on 2016. The attack target are the media outlets and electric companies in Ukraine. The new version of BlackEnergy does not contains destroy feature. It oppositely able to download and execute a binary or shell command, uninstall itself, modify internal settings, or load additional modules. The conceptual idea of the design is evade the defense mechanism detection. In short to summarize such design is that new version of black energy combined spear phishing email with embedded link file contains path to the module (.dll) .
The functionality of BlackEnergy can be extended with additional modules. These modules are stored in encrypted form in a separate file, which can be referred to as a plug-in-container. The attacker will be executed and download payload afterwards (see below diagram for reference)
We known the vulnerability known as CVE-2010-2568 and used by the Stuxnet computer worm can be weaponized to remotely execute code over a Windows computer without the user’s knowledge. It target the Siemens WinCC SCADA systems.
DNP3 (Distributed Network Protocol) is a set of communications protocols used between components in process automation systems especially electric and water supply facilities. The distributed network protocol (DNP3) play a major control role in SCADA system especially used by SCADA Master Stations (Control Center). A hints in below diagram shown that programmable logic controller responsible centrifuge status control and monitoring.
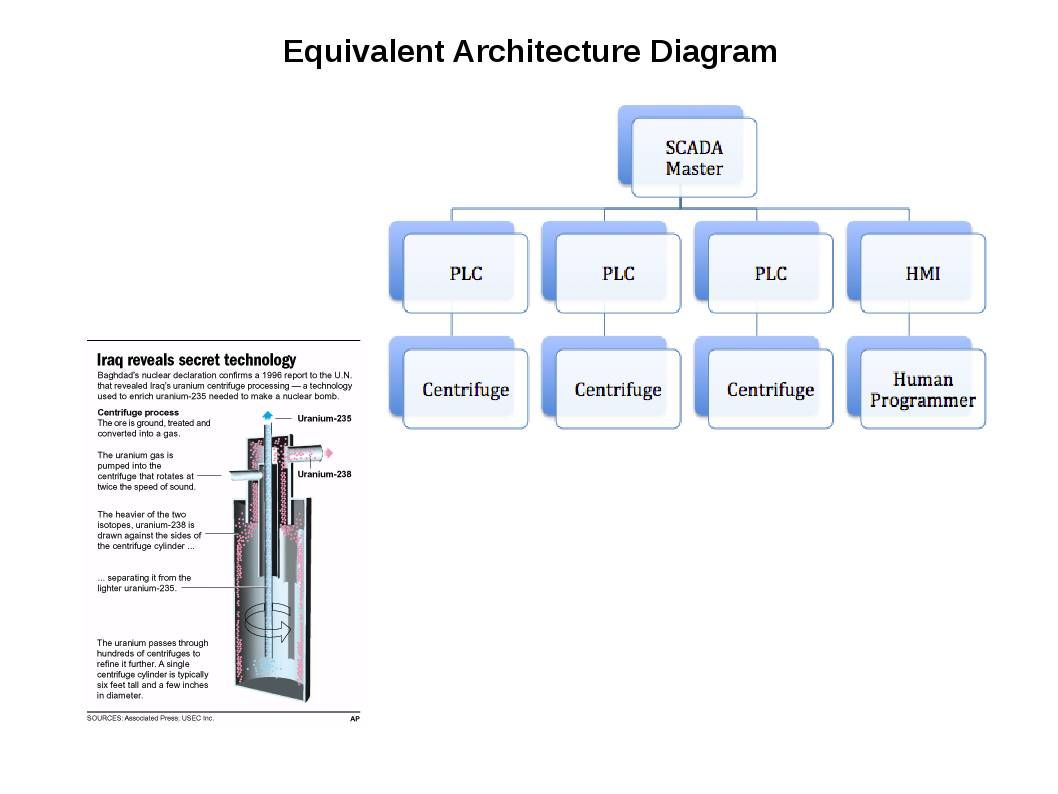
How Iran’s nuclear centrifuges facilities work?
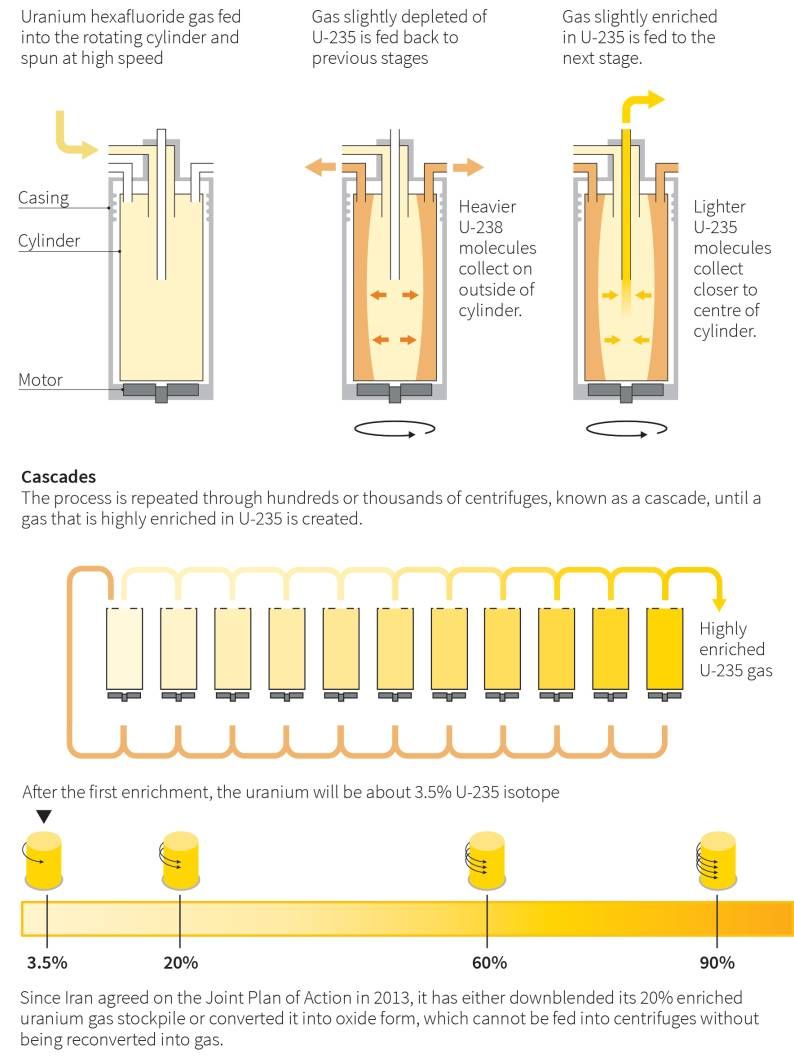
As times go by, more and more manufacturer involves to nuclear facilities hardware re-engineering and installations. The well known vendor not limit to Siemens, it now have Schneider Electric, Allen-Bradley, General Electric (GE)…. But another 0-day vulnerability found few months ago.
The Modbus is a serial communications protocol originally published by Modicon (now Schneider Electric) in 1979 for use with its programmable logic controllers (PLCs). The Modbus protocol is the major communication protocol communicates with programmable logic controller. However it is a UN-encrypted data traffic. And therefore sensitive information is run in clear text (see below diagram for reference).
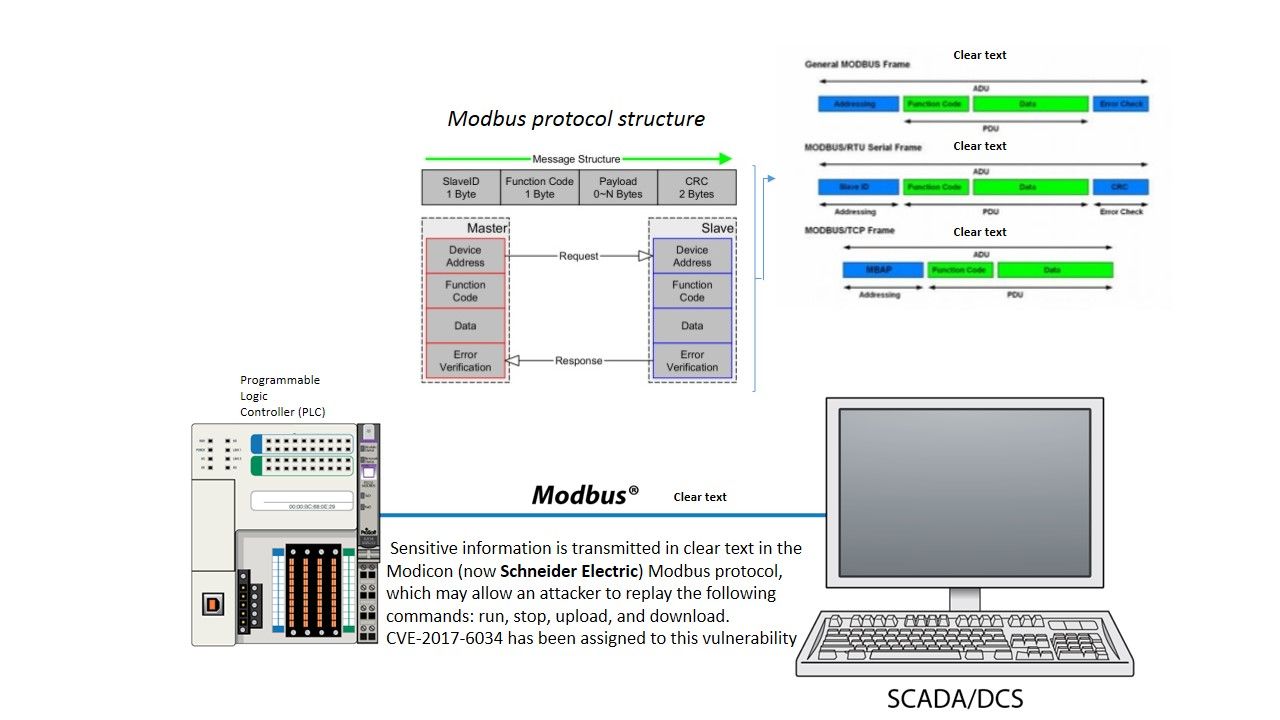
Remark: Both DCS and SCADA are monitoring and control systems used in industrial applications. The systems monitor equipment and processes to ensure all processes and equipment are performing within the required tolerances and specifications.
A design weakness was discovered in Schneider Electric Modicon Modbus Protocol. Sensitive information is transmitted in cleartext in the Modicon Modbus protocol, which may allow an attacker to replay the following commands: run, stop, upload, and download (CVE-2017-6034). Besides, the Modicon Modbus protocol has a session-related weakness making it susceptible to brute-force attacks.
Quote:
UMAS is a Kernel level protocol and an administrative control layer used in Unity series PLC and Unity OS from 2.6. It relies on the Modicon Modbus protocol, a common protocol in Critical Infrastructure, SCADA and industrial control systems and used to access both unallocated and allocated Memory from PLC to SCADA system said CTO and founder of CRITIFENCE.
* It may not be entirely patched within the coming years, since it affects a wide range of hardware and vendors.”
December 14, 2017 announcement by FireEye – Found Triton Malware
It looks critical that Schneider programming logical controller could soft patch not issue yet. The expertise by FireEye found security alert on Triconex cotroller. The expert believe that Fireye believe that this masqueraded trilog application was deployed by Sandworm Team. This team engage cyber attack to Ukraine nuclear power facilities in 2016.
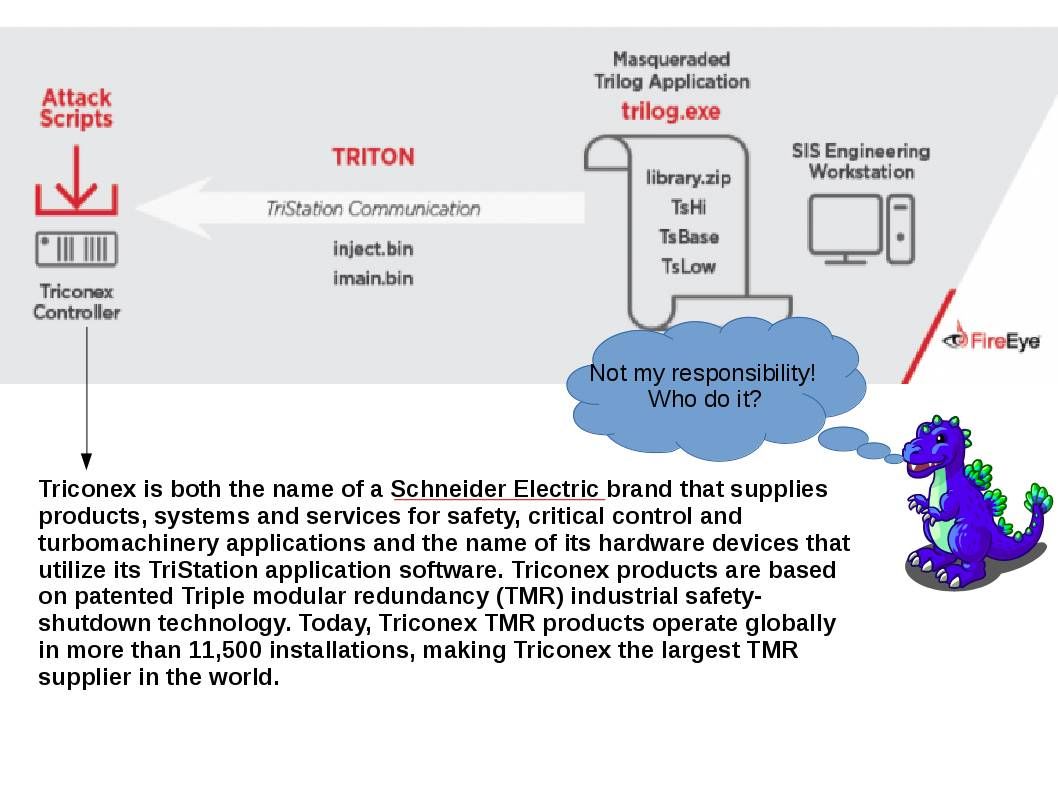
Information Supplement
Supervisory control and data acquisition (SCADA) is a control system architecture that uses computers, networked data communications and graphical user interfaces for high-level process supervisory management. How does this function to operate? Below diagram provides hints for reference.
Conclusion:
The suspicious attack found on Schneider Electric brand this time. It is hard to tell that similar attack will be happen on other brand name soon.
Information appending on 3rd Feb 2018 : related SCADA information for your reference
I know this if off topic but I’m looking into starting my own blog and was wondering what all is needed to get set up? I’m assuming having a blog like yours would cost a pretty penny? I’m not very internet savvy so I’m not 100 positive. Any suggestions or advice would be greatly appreciated. Thanks|
I just want to tell you that I am all new to blogging and definitely enjoyed this web-site. Almost certainly I’m planning to bookmark your website . You certainly come with superb article content. Cheers for sharing with us your website page.
I am really enjoying the theme/design of your blog. Do you ever run into any browser compatibility issues? A few of my blog readers have complained about my website not operating correctly in Explorer but looks great in Firefox. Do you have any advice to help fix this problem?
I just want to mention I’m new to blogging and seriously savored your website. Probably I’m going to bookmark your blog post . You surely have exceptional well written articles. Thank you for sharing with us your blog site.
I just want to mention I’m beginner to blogs and certainly savored this blog. Very likely I’m going to bookmark your blog post . You actually have awesome articles. Appreciate it for sharing with us your website.
I simply want to tell you that I am just new to blogging and site-building and really liked your page. Most likely I’m planning to bookmark your blog . You certainly have remarkable articles. Regards for revealing your blog site.
I hope you all are having a great weekend. I added a new list. This one is smaller, but still useful. I think the next one will be bigger.
I’ve been researching this subject for about 3 weeks now and this is actually the 1st article that truly is practical. Why is it so hard to locate effective data when it comes to protection today? Surely understand the time you invested placing your concepts into words so newbies like me personally can take a step. Could there be a part two to your blog? Thank you again!
I just updated my site with a new list. I hope you all are having a great week.