Preface: BIND (Berkeley Internet Name Domain) is the most commonly used DNS software on the Internet today. DNS servers that use BIND as server software account for about 90% of all DNS servers.
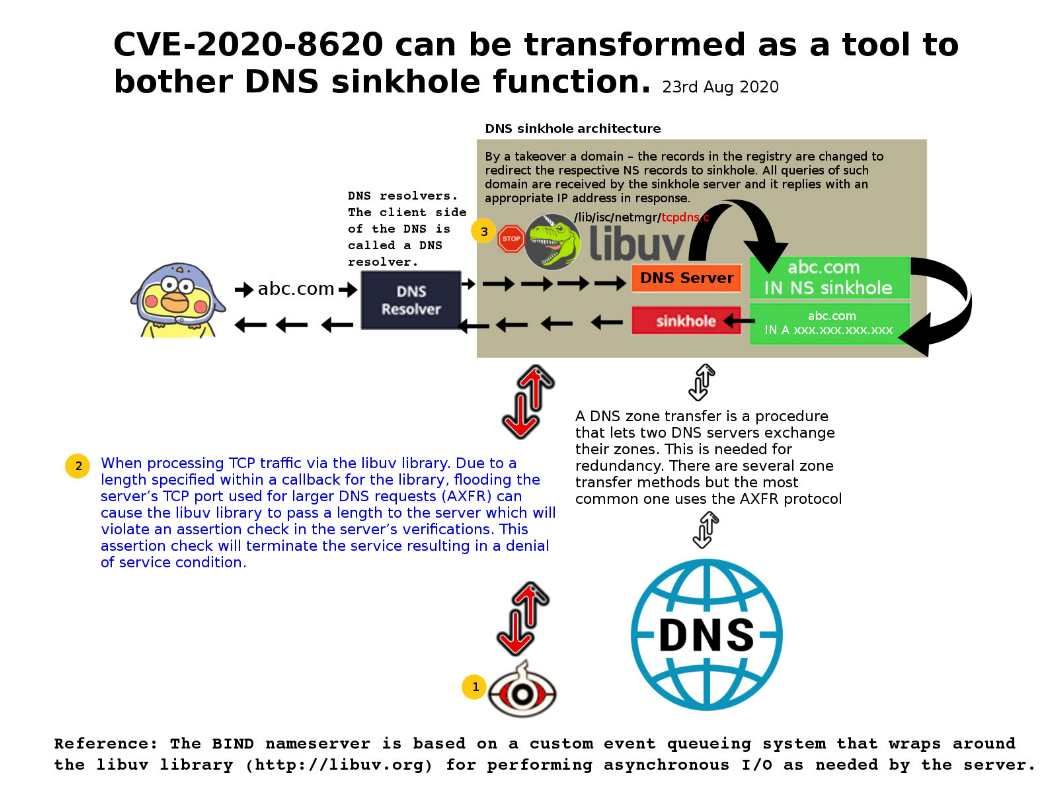
Technical background: The BIND nameserver is based on a custom event queueing system that wraps around the libuv library (http://libuv.org) for performing asynchronous I/O as needed by the server. libuv is a multi-platform support library with a focus on asynchronous I/O. It was primarily developed for use by Node.js, but it’s also used by Luvit, Julia, pyuv, and others.
Remark: A DNS zone transfer is a procedure that lets two DNS servers exchange their zones. This is needed for redundancy. There are several zone transfer methods but the most common one uses the AXFR protocol.
Vulnerability details: When handling TCP traffic through the libuv library. Due to a length specified within a callback for the library (lib/isc/netmgr/tcpdns.c), flooding the server TCP port used for larger DNS requests (AXFR) will cause the libuv library to pass the length to the server. Therefore, it will result in a violation of the assertion check in the server verification. This assertion check will terminate the service, resulting in a denial of service condition. An attacker can flood ports with unauthenticated packets to trigger this vulnerability.
For information on CVE-2020-8620, thanks to Cisco TALOS.
Official announcement: https://kb.isc.org/docs/cve-2020-8620