Preface: A growing number of Chinese chip design firms have adopted open-source RISC-V in their chip designs as an alternative to Intel’s proprietary X86 and Arm’s architecture, in a bid to minimise potential damage from US sanctions and to save on licensing fees.
Background: If you still remember? The RISC System/6000 (RS/6000) is a family of RISC-based Unix servers, workstations and supercomputers made by IBM in the 1990s.
Who uses RISC-V today? The organization has grown to 2,000+ members from more than 70 countries over the span of just a few years. Members of RISC-V International include founding partners Google, Qualcomm and Western Digital, to name a few, as well as Arduino, Hitachi and Samsung.
What is PMP RISC-V? Physical Memory Protection (PMP) is a part of the RISC-V Privileged Architecture Specification which discribes the interface for a standard RISC-V memory protection unit. The PMP defines a finite number of PMP regions which can be individually configured to enforce access permissions to a range of addresses in memory.
What is a load access fault? Access faults happen as a result of failing a PMP check. Roughly speaking, it means that the processor is trying to use memory that it does not have permission to use. This can only occur in machines with at least User mode, since in Machine mode the processor is always allowed to access everything.
The machine level has the highest privileges and is the only mandatory privilege level for a RISC-V hardware platform. Code run in machine-mode (M-mode) is usually inherently trusted, as it has low-level access to the machine implementation. M-mode can be used to manage secure execution environments on RISC-V.
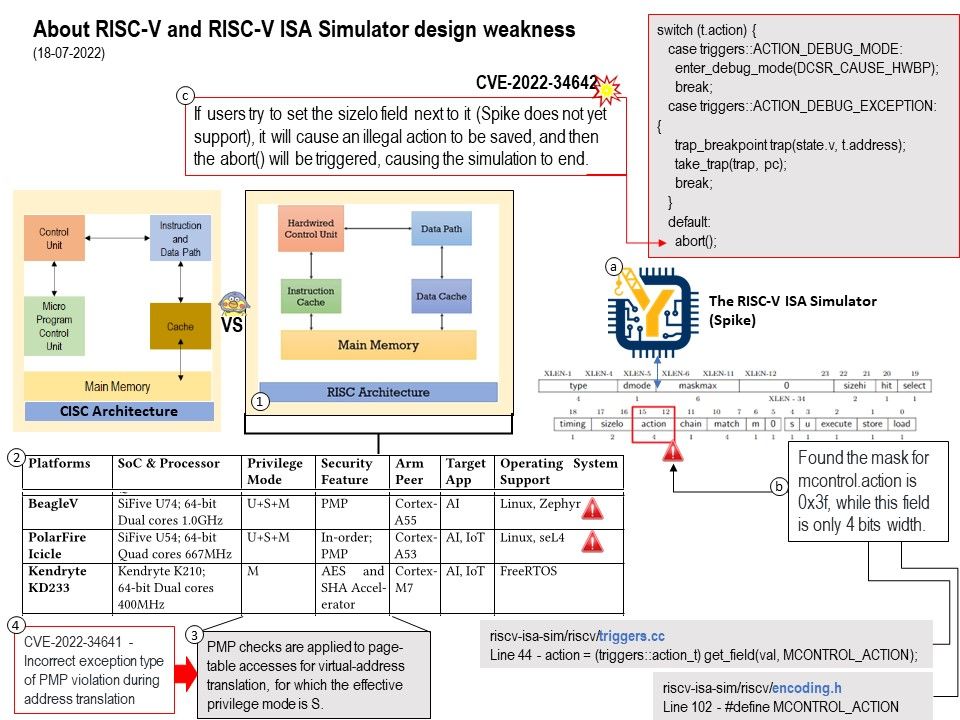
Vulnerability details:
CVE-2022-34642 – The component mcontrol.action in RISCV ISA Sim commit ac466a21df442c59962589ba296c702631e041b5 contains the incorrect mask which can cause a Denial of Service (DoS).
Reference: https://github.com/riscv-software-src/riscv-isa-sim/issues/1032
CVE-2022-34641 – CVA6 commit d315ddd0f1be27c1b3f27eb0b8daf471a952299a and RISCV-Boom commit ad64c5419151e5e886daee7084d8399713b46b4b implements the incorrect exception type when a PMP violation occurs during address translation.
Reference: https://github.com/openhwgroup/cva6/issues/906 Weakness Enumeration – unknown
CVE-2022-34643 – RISCV ISA Sim commit ac466a21df442c59962589ba296c702631e041b5 implements the incorrect exception priotrity when accessing memory.
https://github.com/riscv-software-src/riscv-isa-sim/issues/971 Weakness Enumeration – unknown