Preface: Oracle Database 19c is the current long term release, and it provides the highest level of release stability and longest time-frame for support and bug fixes. Oracle Database 21c, also available for production use today as an innovation release, provides an early insight into the many enhancements and new capabilities.
Background: Use the CREATE PROCEDURE statement to create a standalone stored procedure or a call specification.
A procedure is a group of PL/SQL statements that you can call by name. A call specification (sometimes called call spec) declares a Java method or a third-generation language (3GL) routine so that it can be called from SQL and PL/SQL. The call spec tells Oracle Database which Java method to invoke when a call is made. It also tells the database what type conversions to make for the arguments and return value.
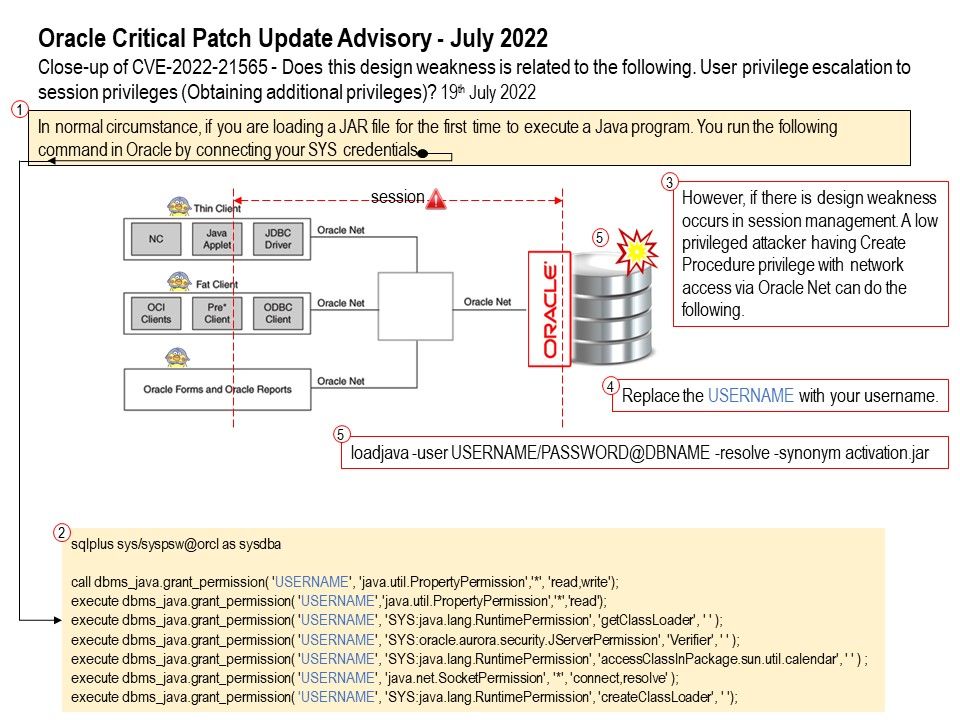
In Oracle Database, use loadjava utility to load JAR file. The loadjava utility creates schema objects in Oracle database and then load JAR file contents into it.
About Designating Database Privileges and JVM Permissions
You must have the following SQL database privileges to load classes:
- CREATE PROCEDURE and CREATE TABLE privileges to load into your schema.
- CREATE ANY PROCEDURE and CREATE ANY TABLE privileges to load into another schema.
- oracle.aurora.security.JServerPermission.loadLibraryInClass.classname
Vulnerability details: Vulnerability in the Java VM component of Oracle Database Server. Supported versions that are affected are 12.1.0.2, 19c and 21c. Easily exploitable vulnerability allows low privileged attacker having Create Procedure privilege with network access via Oracle Net to compromise Java VM. Successful attacks of this vulnerability can result in unauthorized creation, deletion or modification access to critical data or all Java VM accessible data.
Official announcement – Oracle Critical Patch Update Advisory – July 2022. See the link for details – https://www.oracle.com/security-alerts/cpujul2022.html