Official Posted: 31st May 2024
Preface: PowerVR not limited 2D and 3D rendering, and for video encoding, decoding, associated image processing. It also develops AI accelerators called Neural Network Accelerator (NNA). The IMG Series4 is a revolutionary neural network accelerator (NNA) for the automotive industry that enables ADAS and autonomous driving.
PowerVR accelerators are not manufactured by PowerVR, but instead their IP blocks of integrated circuit designs and patents are licensed to other companies.
Remark: An IP block is a reusable unit of logic, cell, or chip layout design and can be used as building block for various chip- and logic designs. By making this technology available NXP is opening up the opportunity for chip designers to leverage our building blocks in a wide assortment of on-chip solutions.
Background: What is DDK? To build the Android kernel and other kernel artifacts (modules, boot images, etc.), they provide a framework called “Kleaf”. For Android 14+, Kleaf is strongly recommended. One part of Kleaf is the Driver Development Kit (DDK) which is used to build external modules.
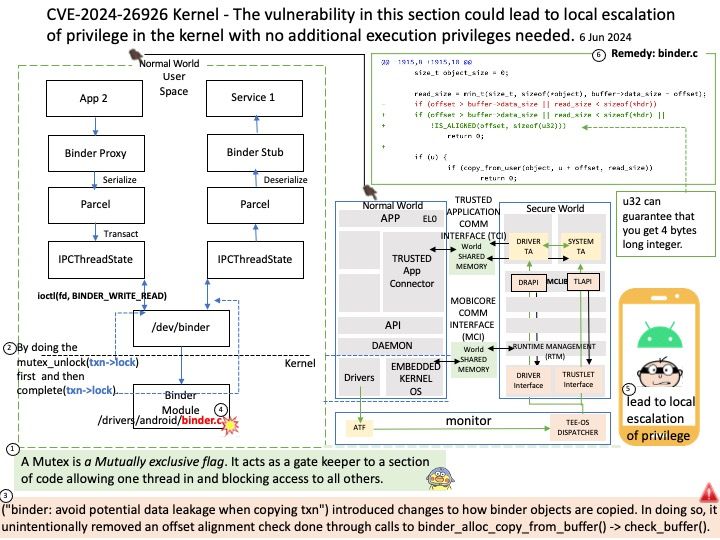
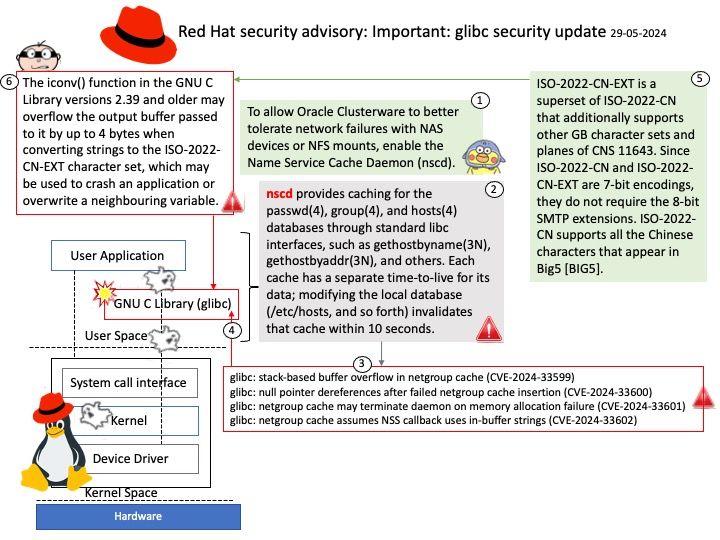
Vulnerability details: CVE-2024-31335 – GPU – PowerVR: Wrong order of operations in DevmemIntUnmapPMR2 may lead to temporarily dangling PTEs.
Software installed and run as a non-privileged user may conduct improper GPU system calls to trigger use-after-free kernel exceptions.
Official announcement: For detail, please refer to link –
https://www.imaginationtech.com/gpu-driver-vulnerabilities/#may24