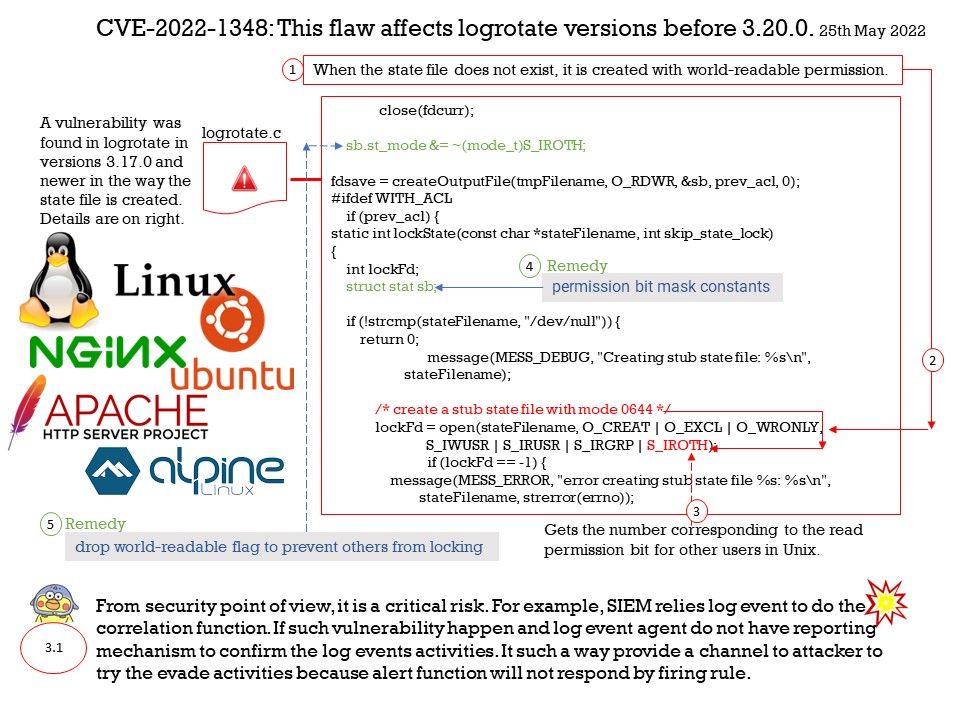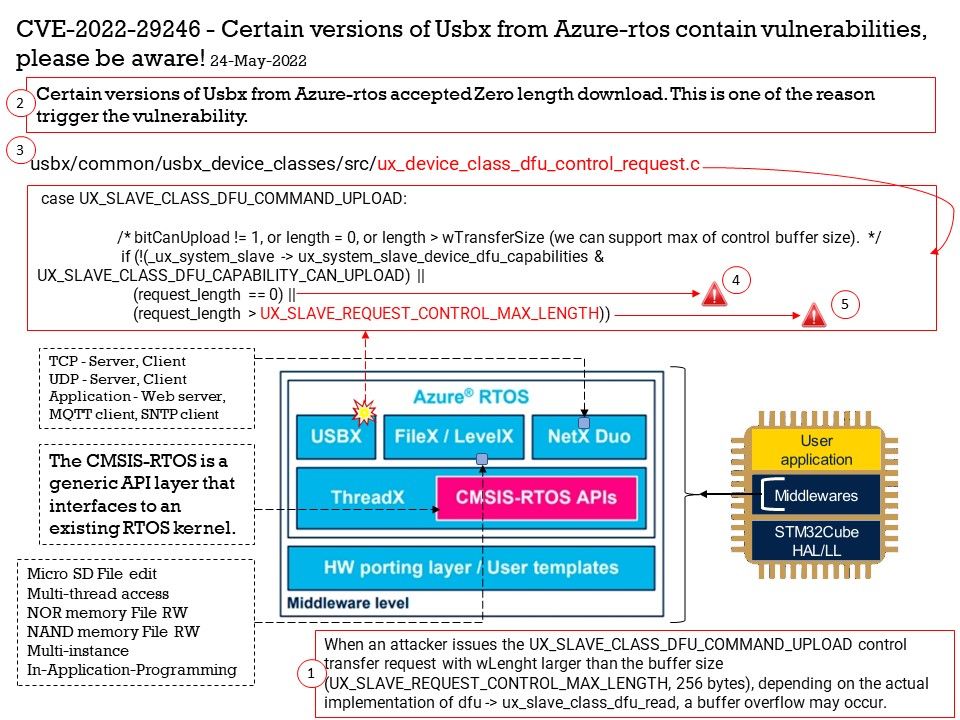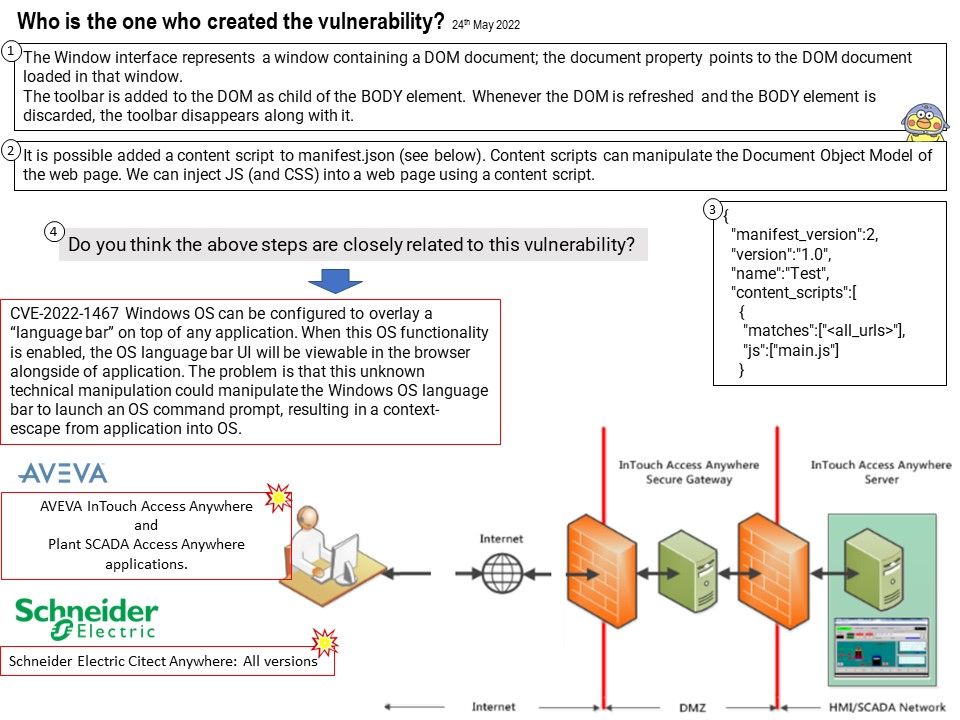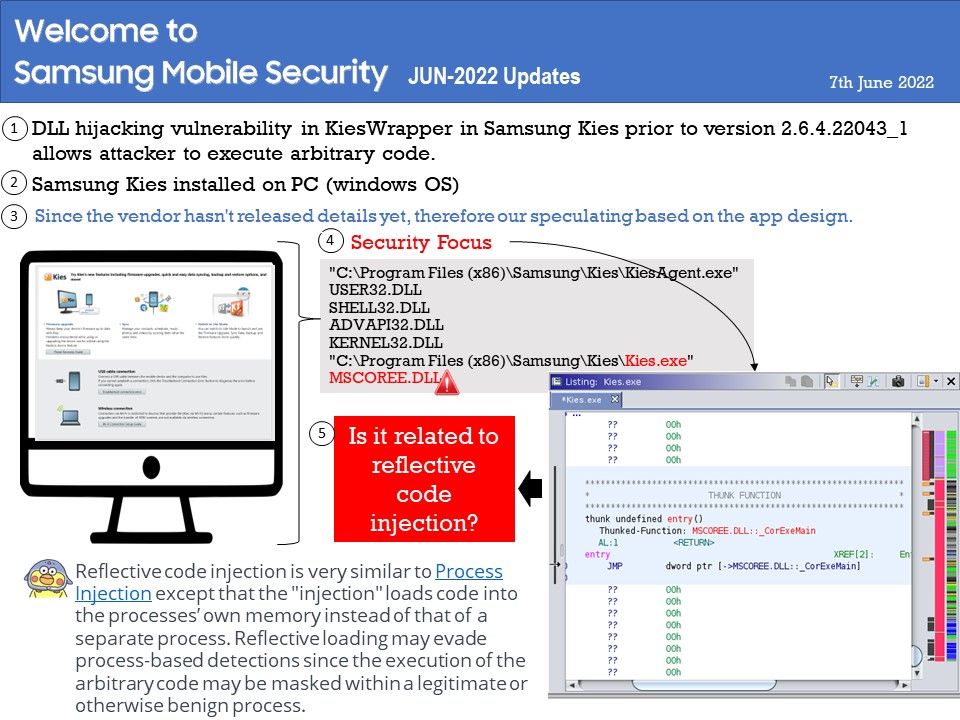
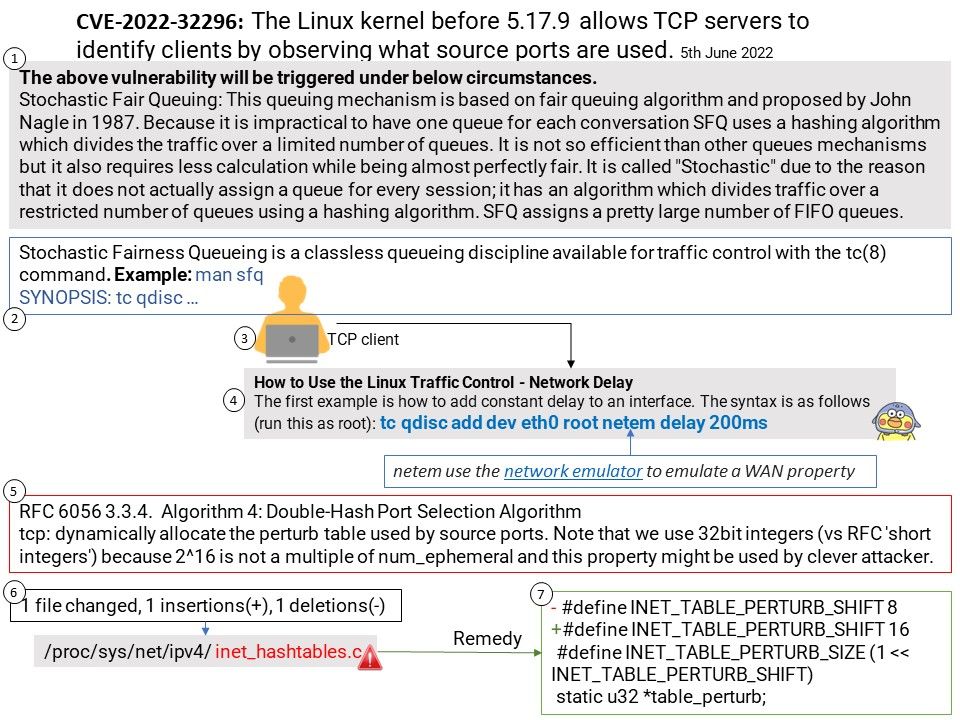
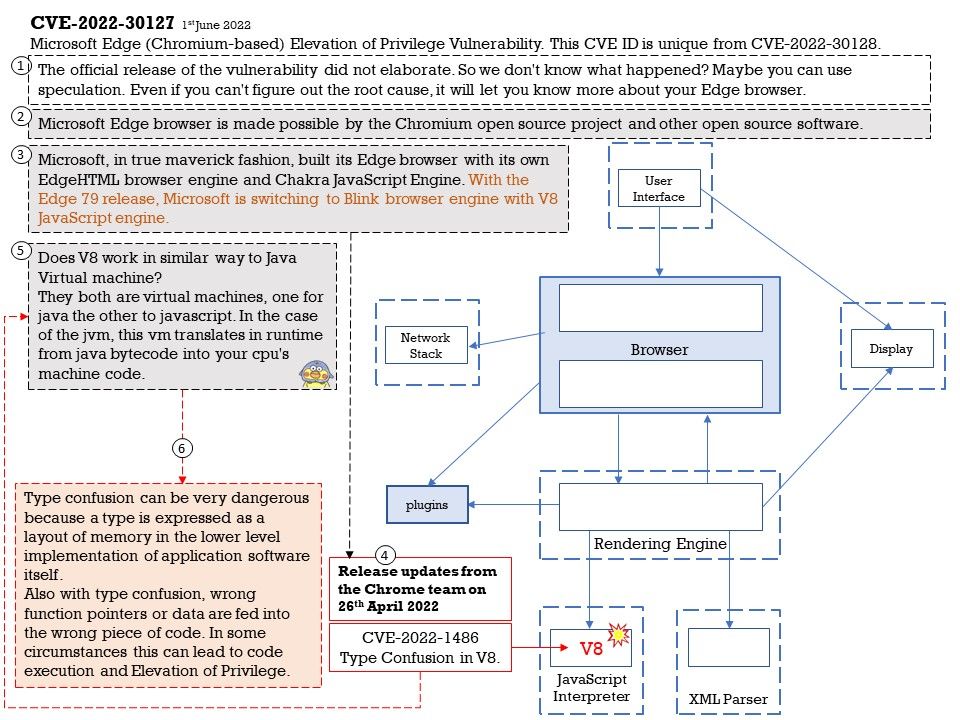
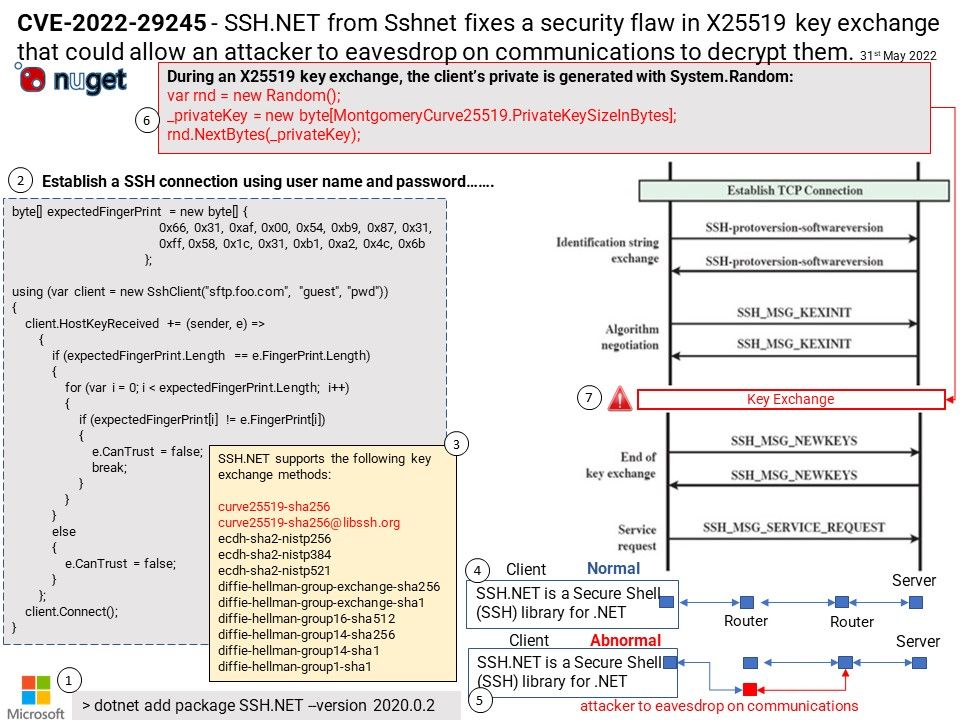
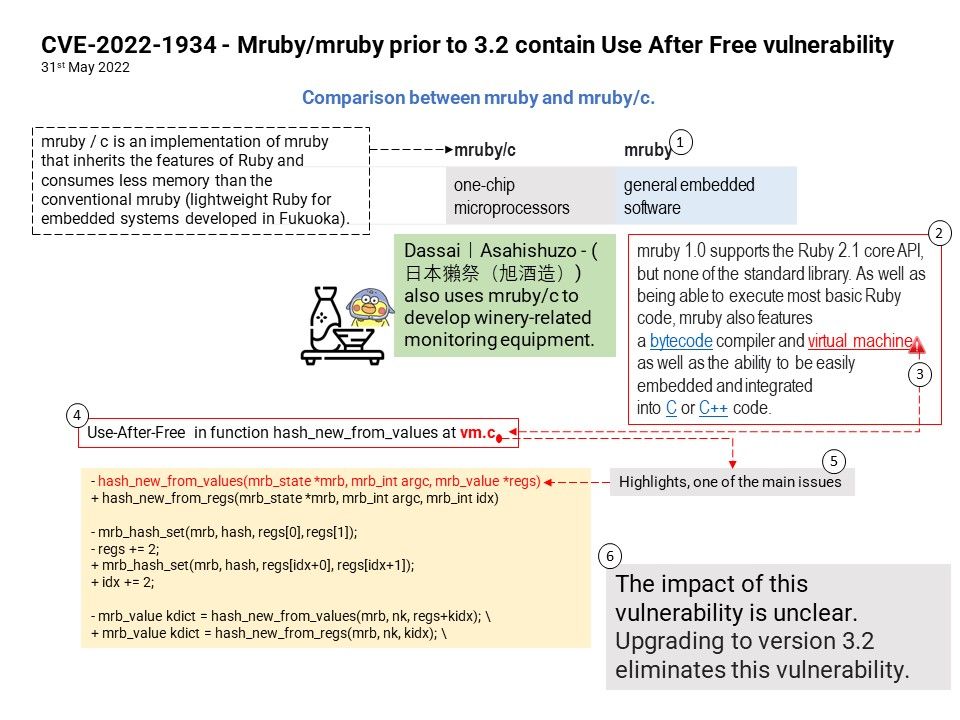
Preface: According to the information provided by the supplier. This vulnerability was reported on April 5, 2022. But we didn’t see that record until this month.
Background: Samsung Kies is the official tool from Samsung for Android devices. Using Samsung Kies, you can view apps in full screen on your Windows, no matter what network you’re on. You can personalise services too, simply by becoming a Samsung Apps member or registering your mobile phone. If transferring data from Samsung device to PC is your prime intention then Samsung Kies would be a good choice.
Additional reference: The new version of Smart Switch let you move data from your old device to your new Galaxy device quickly and easily.
Vulnerability details: DLL hijacking vulnerability in KiesWrapper in Samsung Kies prior to version 2.6.4.22043_1 allows attacker to execute arbitrary code. The patch changes to load default DLL in Windows. Since the vendor hasn’t released details yet, therefore our speculating based on the app design.
According to my observations. The following details may be related to such vulnerabilities. But I think MSCOREE[.]dll will be closely related to this.
“C:\Program Files (x86)\Samsung\Kies\KiesAgent[.]exe”
USER32[.]DLL
SHELL32[.]DLL
ADVAPI32[.]DLL
KERNEL32[.]DLL
“C:\Program Files (x86)\Samsung\Kies\Kies[.]exe”
MSCOREE[.]DLL
So, it is possible for cyber criminal exploit this design weakness by Reflective Code Loading.
About Reflective code loading: Reflective code injection is very similar to Process Injection except that the “injection” loads code into the processes’ own memory instead of that of a separate process. Reflective loading may evade process-based detections since the execution of the arbitrary code may be masked within a legitimate or otherwise benign process. Reflectively loading payloads directly into memory may also avoid creating files or other artifacts on disk, while also enabling malware to keep these payloads encrypted (or otherwise obfuscated) until execution.
Remedy: Install version 2.6.4.22043_1
For details, please refer to the official announcement – https://security.samsungmobile.com/serviceWeb.smsb?year=2022&month=6

.jpg)