Preface: In the Linux Kernels n_gsm serial line discipline, which can be exploited by local attackers to gain kernel level root access. It original published by other Linux brand on 8th May 2024.
Background: In Unix systems, a tty (which is short for “teletypewriter”) is the standard representation of a terminal device, with at least input and output capabilities and usually much more. These were originally connected to serial ports, but most today are virtual terminals, connected to either a text-mode console (DOS-like) or a graphical terminal program (like xterm or gnome-terminal).
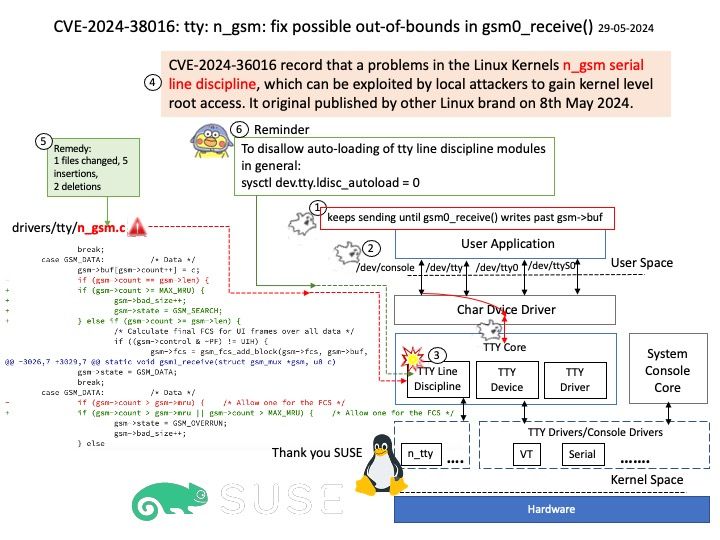
Vulnerability details: tty: n_gsm: fix possible out-of-bounds in gsm0_receive()
Assuming the following:
– side A configures the n_gsm in basic option mode
– side B sends the header of a basic option mode frame with data length 1
– side A switches to advanced option mode
– side B sends 2 data bytes which exceeds gsm->len
Reason: gsm->len is not used in advanced option mode.
– side A switches to basic option mode
– side B keeps sending until gsm0_receive() writes past gsm->buf Reason: Neither gsm->state nor gsm->len have been reset after reconfiguration.
Official details: For detail, please refer to link – https://www.tenable.com/cve/CVE-2024-36016