Preface: In linux distributions the term ‘upstream’ (also applied to kernel) refers to the original version (as is released by software developers) of a program/software (kernel in your case) while ‘downstream’ refers to the software provided by linux distribution.
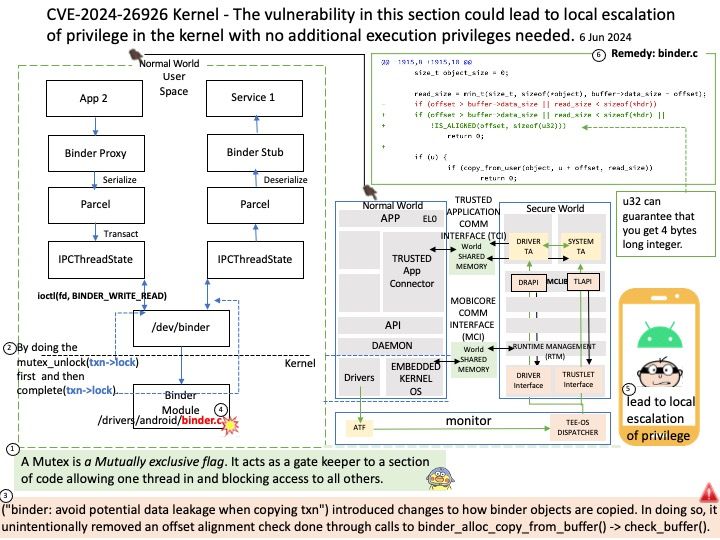
Background: There are many ways to communicate with IPC, such as: Shared Memory, Message Queue, PIPE, FIFO, Unix Socket, etc. A process cannot access another process’s memory. However, the kernel has control over all processes and therefore can expose an interface that enables IPC. In Binder, this interface is the /dev/binder device, which is implemented by the Binder kernel driver.
Ref: A Mutex is a Mutually exclusive flag. It acts as a gate keeper to a section of code allowing one thread in and blocking access to all others.
Vulnerability details:
Kernel -The vulnerability in this section could lead to local escalation of privilege in the kernel with no additional execution privileges needed.
Official announcement: For detail, please refer to link –
https://source.android.com/docs/security/bulletin/2024-06-01