Preface: In Android 11, its automatically resetting permissions for apps you haven’t used for an extended period of time.
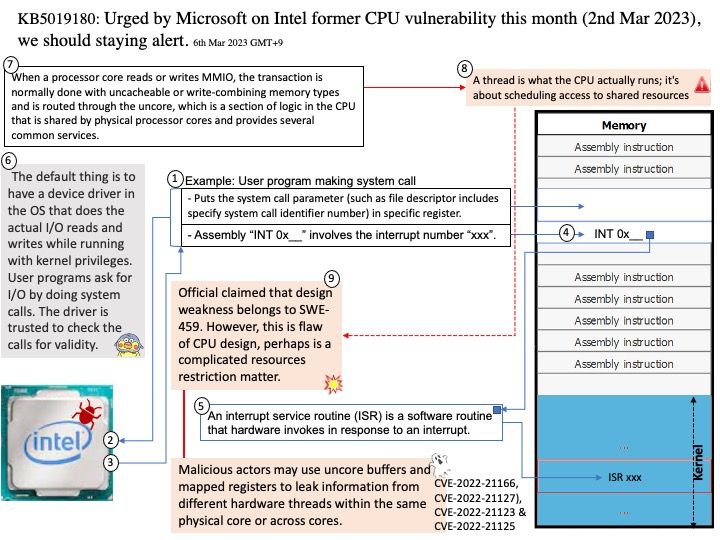
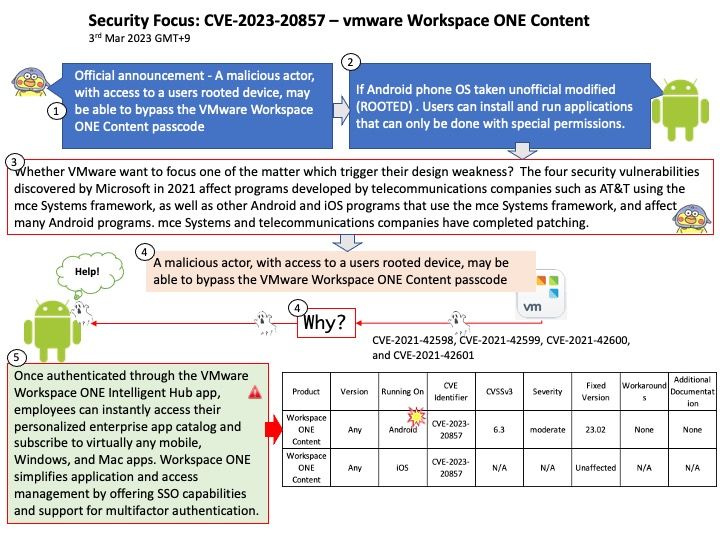
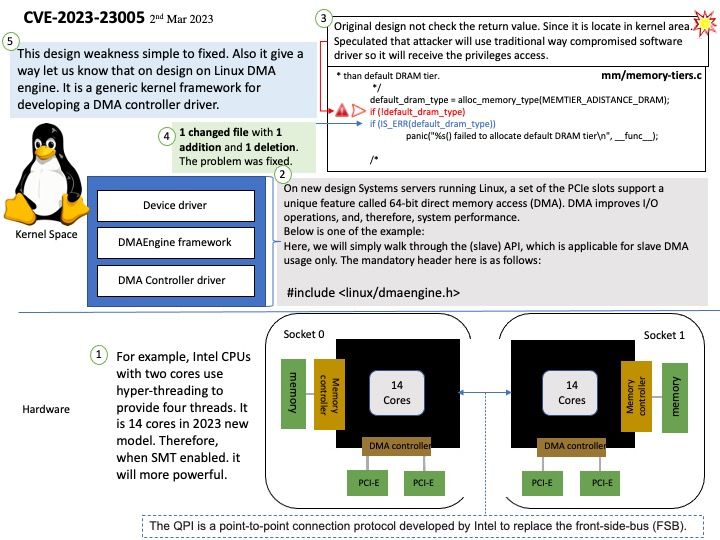
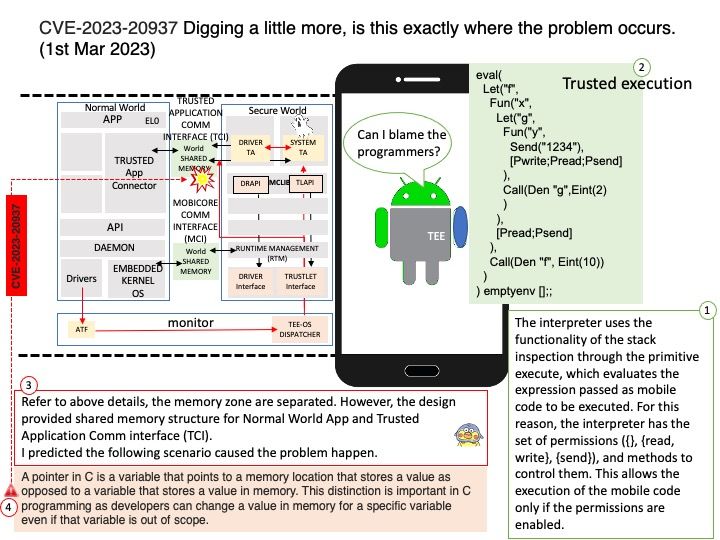
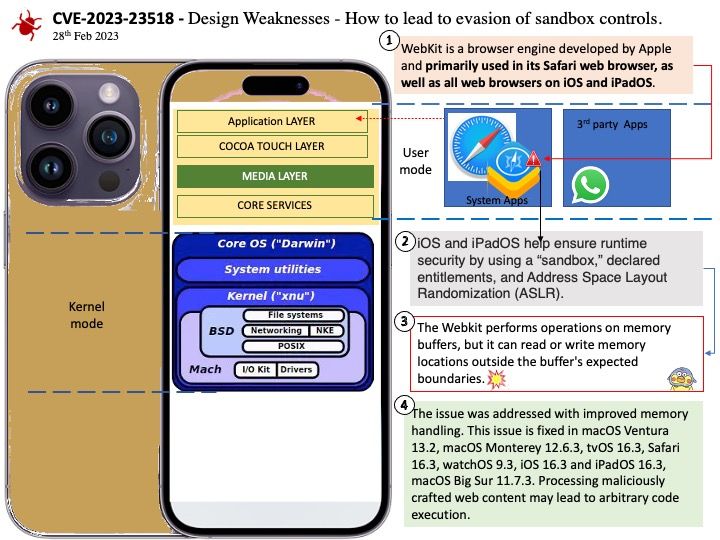
In Android 13, app makers can go above and beyond in removing permissions even more proactively on behalf of their users.
How do I stop Android from removing app permissions? Go into your system settings, go to app settings, find the app, go to permissions. There should be a toggle option named “Remove permissions if app isn’t used”. Turn that option off.
The above function is one of the preventive controls in Android. Vulnerabilities occur because outdated applications may have design flaws.
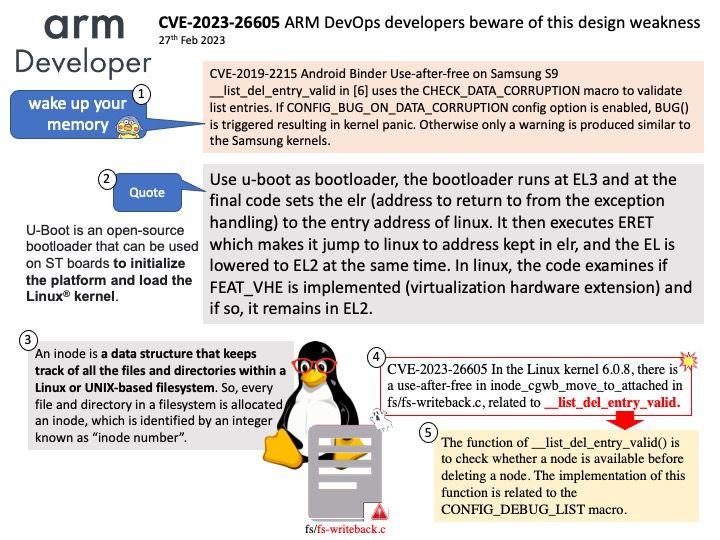
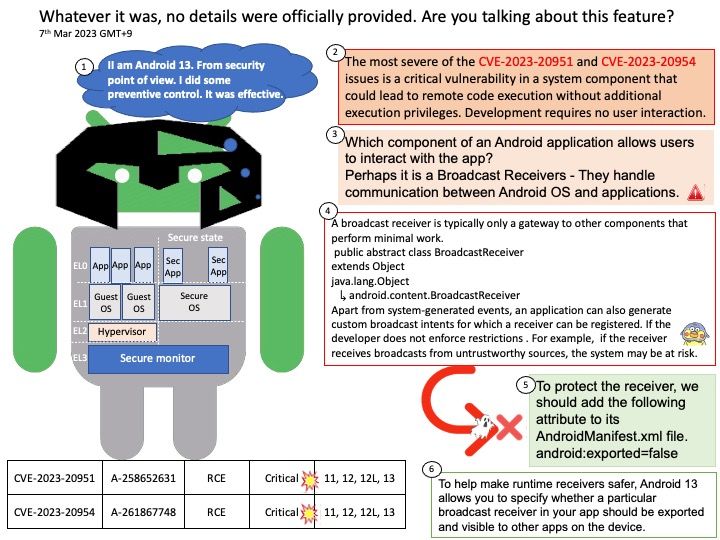
Background: Which component of an Android application allows users to interact with the app?
Broadcast Receivers – They handle communication between Android OS and applications.
A broadcast receiver is typically only a gateway to other components that perform minimal work.
public abstract class BroadcastReceiver
extends Object
java.lang.Object
↳ android.content.BroadcastReceiver
Apart from system-generated events, an application can also generate custom broadcast intents for which a receiver can be registered. If the developer does not enforce restrictions . For example, if the receiver receives broadcasts from untrustworthy sources, the system may be at risk.
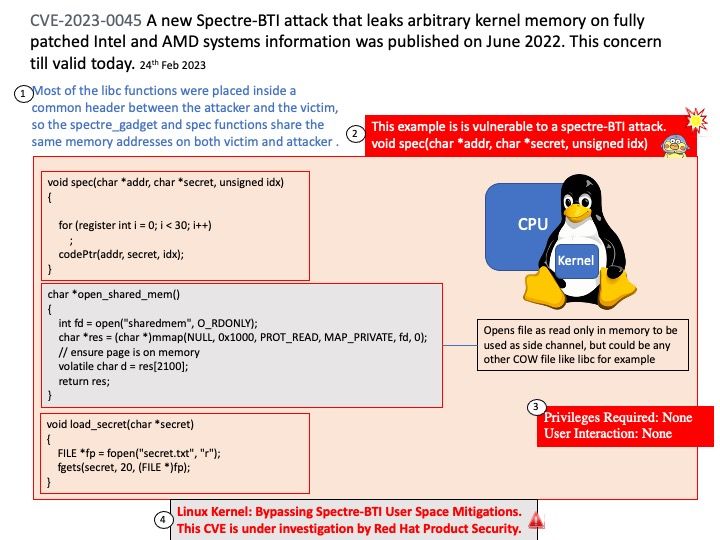
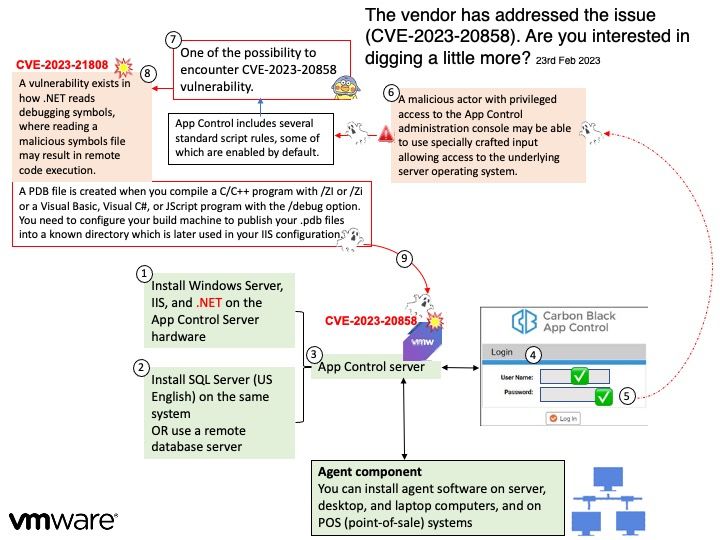
Vulnerability details: The most severe of the CVE-2023-20951 and CVE-2023-20954 issues is a critical vulnerability in a system component that could lead to remote code execution without additional execution privileges. Development requires no user interaction. As the supplier does not provide details! Therefore, it should be patched according to the vendor instructions.
Official details: For more information on this topic, see url – https://source.android.com/docs/security/bulletin/2023-03-01