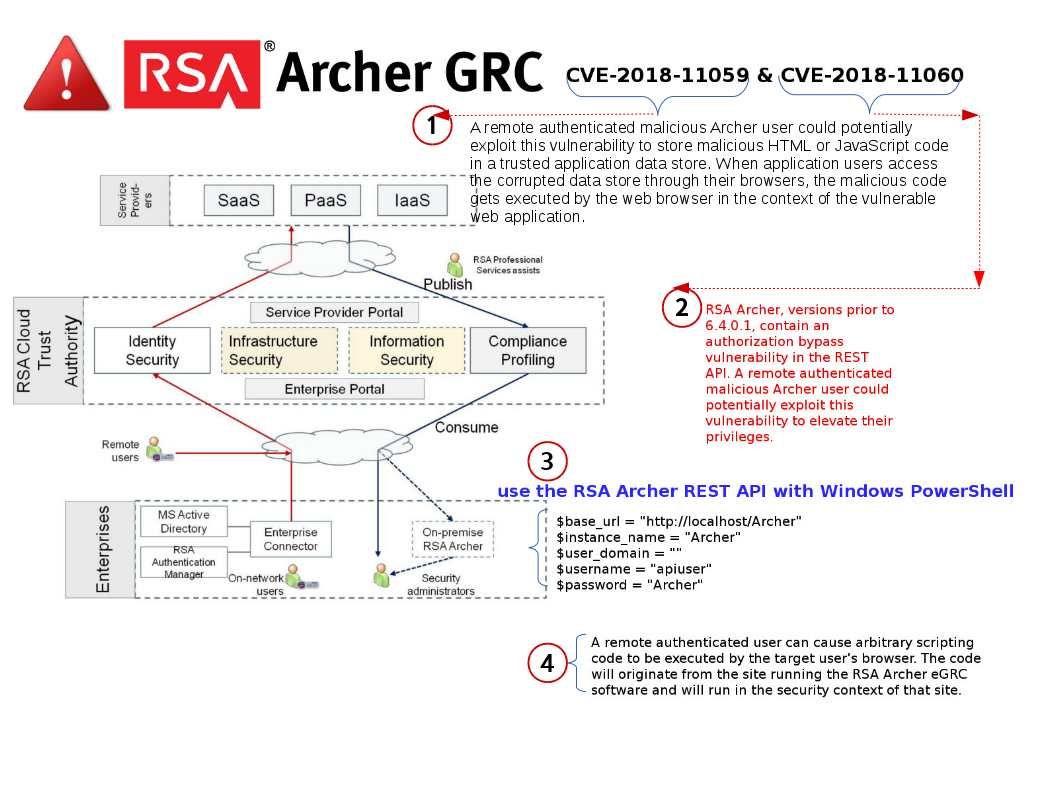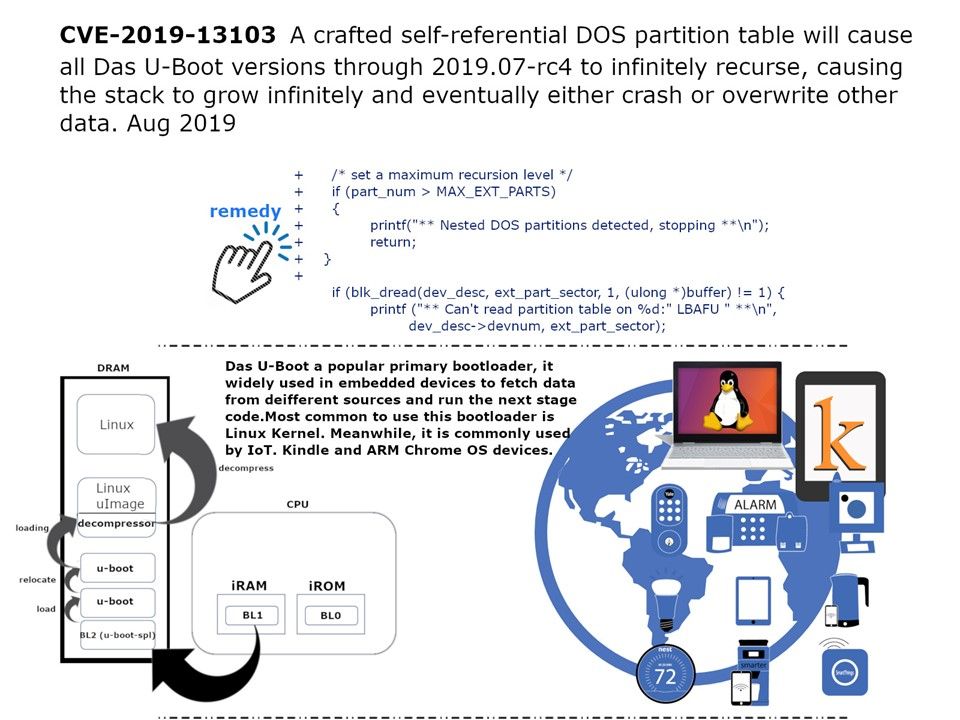
Vulnerability details: A crafted self-referential DOS partition table will cause all Das U-Boot versions through 2019.07-rc4 to infinitely recurse, causing the stack to grow infinitely and eventually either crash or overwrite other data.
Introduction: Das U-Boot a popular primary bootloader, it widely used in embedded devices to fetch data from different sources and run the next stage code.In the technology and computer markets, widely used to this bootloader is Linux Kernel. Meanwhile, it is commonly used by IoT. Kindle and ARM ChromeOS devices.
Remedy: Official remediation solution is disable DOS partition default sector for 512 because it’s not very common at all to use large numbers of partitions. Meanwhile set a maximum recursion level (refer to the parameter shown on attached diagram).
Please note that Das U-Boot has other vulnerabilities found. The CVE details shown as below:
CVE-2019-14192, CVE-2019-14193, CVE-2019-14194, CVE-2019-14195, CVE-2019-14196, CVE-2019-14197, CVE-2019-14198, CVE-2019-14199, CVE-2019-14200, CVE-2019-14201, CVE-2019-14202, CVE-2019-14203 and CVE-2019-14204
Above vulnerabilities could let attacker gain remote code execution at the U-Boot powered device when U-Boot is configured to use the network for fetching the next stage boot resources.
Official announcement on CVW-2019-13103 – https://lists.denx.de/pipermail/u-boot/2019-July/375512.html